A dangerous digital threat has emerged, specifically targeting mobile users in Turkiye to drain their bank accounts. Researchers from the cybersecurity firm Kaspersky’s threat intelligence unit Securelist first spotted this Android-based Trojan (a virus hiding inside a normal-looking file) in August 2025, naming it Frogblight. The malware has evolved rapidly, with researchers noting frequent updates throughout September 2025 to evade detection.
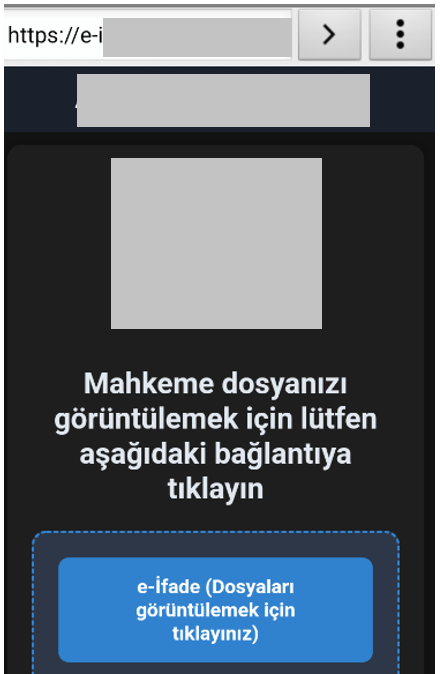
The primary way Frogblight spreads is through smishing (SMS phishing). Scammers send text messages to people in Turkiye, claiming the recipient is involved in a legal court case or eligible for financial aid, providing a link to download a file viewer or support app.
Scammers also spoof social support apps (e.g. fake portals for the Ministry of Family and Social Services or files named e-ifade.apk) to trick people into thinking they are applying for state aid.
As we know it, fear is a powerful motivator, leading many to install the malicious file. Once installed, the app uses the Turkish name ‘Davalarım’ (My Court Cases) to appear legitimate and requests extensive permissions to read SMS and access storage.
Further investigation revealed that the code contains comments in Turkish, suggesting the creators are native speakers. Interestingly, researchers noted the virus is smart enough to hide; it will actually shut down if it detects it is being tested on a fake phone (used by experts for study) or if the device is physically located in the United States.
SecureList’s detailed analysis reveals that the malware doesn’t just steal passwords; it acts like a spy. After a user grants permission, the app opens an actual government website to look official. It then waits for the user to select a banking login to inject hidden JavaScript code.
This code records everything the user types. Newer versions have added features like keylogging (recording keystrokes), stealing contact lists, and gathering private call logs.
“Frogblight represents a concerning evolution in mobile banking threats,” noted Georgy Bubenok, a malware analyst at Kaspersky, explaining that using legitimate government portals makes these traps much more effective.
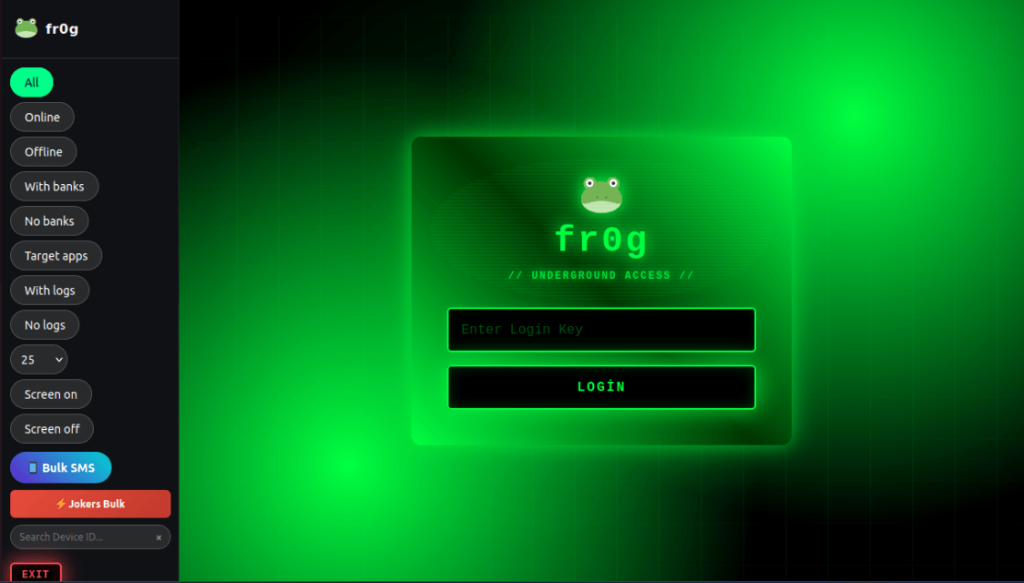
It is worth noting that hackers have expanded their disguises, with newer versions pretending to be the Google Chrome browser or universal social aid tools. Researchers chose the name Frogblight because the hackers’ control center featured a frog-themed design named ‘fr0g.’ They even found the source code on GitHub alongside other malware like Coper, suggesting it is sold as malware-as-a-service (MaaS) to other criminals.
To keep your finances safe, Kaspersky researchers recommend avoiding APK files sent via text or untrusted websites, and scrutinising app permission requests; for instance, a simple file viewer should not need to manage your SMS messages.