A new and highly sophisticated cyber threat actor, known as TAG-150, has emerged on the global stage, wreaking havoc since March 2025 with a suite of custom malware families and an expansive, multi-tiered infrastructure used to compromise organizations and individuals alike.
Insikt Group research has revealed that TAG-150’s infrastructure is structured in four tiers, ranging from victim-facing command-and-control (C2) servers to backup and intermediary layers that obfuscate the group’s operations.
These servers are used to manage and deploy a range of malware, including CastleLoader, CastleBot, and the newly uncovered CastleRAT a remote access trojan (RAT) with both Python and C variants.
These initial payloads often deliver further malicious software such as SectopRAT, WarmCookie, and several credential-stealing infostealers, maximizing the potential for data exfiltration and internal compromise.
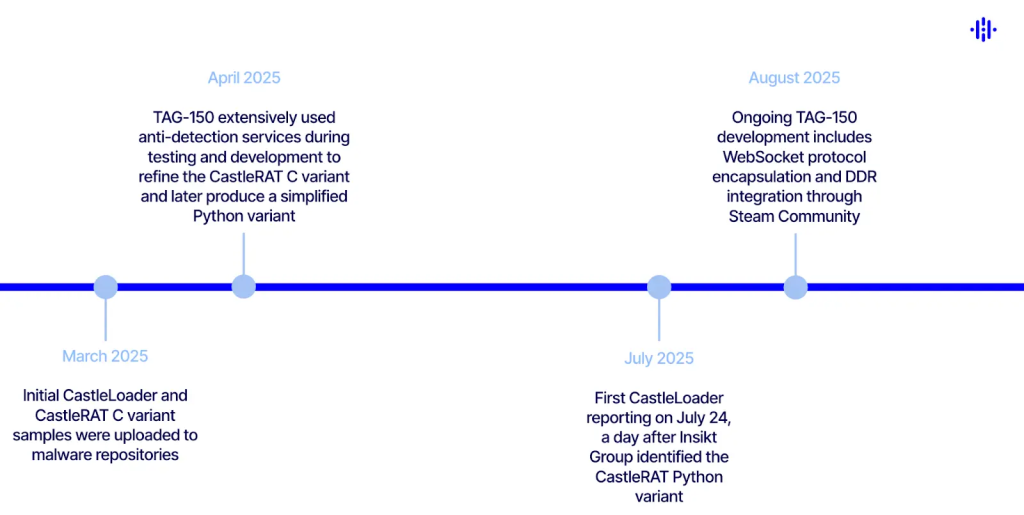
The CastleRAT trojan stands out for its technical sophistication. The Python variant focuses on stealth and is rarely detected by antivirus solutions; it can collect system information, download and execute payloads, run CMD and PowerShell commands, and delete itself to evade detection.
The C variant is even more feature-rich, boasting keylogging, clipboard hijacking, screencapture, file upload/download, persistence mechanisms, and detection evasion techniques, making it a potent tool for remote surveillance and control.
TAG-150’s attack chain typically employs phishing techniques, including fraudulent domains that mimic popular platforms or developer libraries, as well as malicious GitHub repositories.
Victims are lured into executing PowerShell commands, often disguised as legitimate debugging or software update processes.
Upon successful infection a rate as high as 28.7% among interacting victims—the group quickly pivots to deploying secondary payloads and connecting compromised devices to their network of C2 servers.
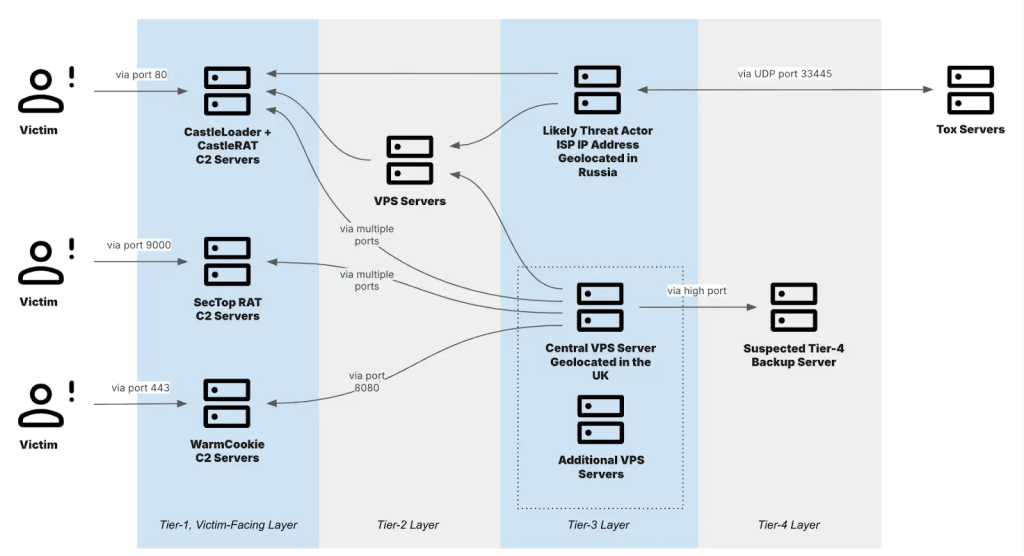
To bolster operational security and resist takedown efforts, TAG-150 leverages privacy-focused services such as Lokinet (Oxen network), file-sharing platforms (Mega.nz, temp.sh), and anti-detection services like Kleenscan.
The rapid adaptability of this group is evidenced by its shift to using Steam Community pages for CastleRAT C2 “dead drops,” as well as its experimentation with encapsulating command protocols within WebSockets.
Infrastructure components are routinely moved across virtual private servers and residential IP ranges, further complicating attribution and mitigation efforts.
Experts recommend blocking all identified TAG-150 infrastructure, deploying updated Sigma, YARA, and Snort detection rules, filtering suspicious emails, and closely monitoring data exfiltration channels.
Given the group’s technical ingenuity and evolving toolkit, security teams must maintain a vigilant watch over emerging trends in the criminal cyber ecosystem.
Insikt Group assesses that TAG-150 will continue innovating, developing new malware families and adopting emerging privacy solutions to sustain its operations and continue targeting organizations around the world.
CastleLoader C2 IP Addresses: 62[.]60[.]226[.]73 62[.]60[.]226[.]211 62[.]60[.]226[.]254 79[.]132[.]130[.]142 80[.]77[.]23[.]48 85[.]158[.]108[.]135 94[.]159[.]113[.]123 |
|---|
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
