Two sets of researchers have discovered two new separate sets of malware, embedded through a number of apps available through various means, that work in much the same way. And worst of all, some of them are even found on the Google Play Store, making the usual “don’t install apps from unfamiliar places” refrain less effective.
This pair of malware seem to be separate, but both work in similar ways. They take advantage of your phone’s processes to endlessly click on adverts, slowing your phone down and having a massive impact on your battery.
The most recently discovered malware, as yet unnamed, was discovered by researchers at mobile security company Dr.Web, and reported by Bleeping Computer. This malware uses the TensorFlow.js library included in Android phones by Google in order to allow machine learning processes to work in browsers.
And work it does — when triggered, the malware opens a virtual (fake) display, on which it displays and clicks on ads. The use of a machine learning process means the clicks seem far more natural than more classic ad-clickers. However, the impact on your device is just as bad as previous malware, with the impact on processing speed and battery life being significant.
Even worse, the malware also opens a permanent livestream to your device, which allows attackers to interact with the virtual display as required.
Notably, the apps come from Xiaomi’s GetApps software catalogue. According to Dr.Web, the apps are uploaded without the malware, which is then added later on, skirting any potential safety nets.
The malware has also, unsurprisingly, heavily infected third-party AP sites like Apkmody and Moddroid. Researchers claim the latter’s Editor’s Choice list is chock full of infected apps, as are “premium” versions of apps like Spotify found on Telegram channels.
Usually, the best choice of action is to avoid downloading apps from any third-party stores, but malware has also been found on the Google Play Store.
Discovered by a team at Checkpoint in November of last year, the malware, dubbed GhostAd, functions much the same as the more recent threat. GhostAd keeps itself in your foreground processes, getting around Google’s usual safeguards by keeping a blank notification open.
This threat is particularly nasty, as it uses an automatic scheduler that boots the process back up again, even if it’s been otherwise shut down. This makes it a tough one to stop once it’s started.
Thankfully, the apps highlighted by Checkpoint have been removed by Google, but it’s alarming that they were able to gain a foothold there in the first place. One infected app was even able to find its way to the number two position on Google Play’s Top Free Tools list.
Since the infected apps are now gone, you probably don’t need to worry about these — but it’s important to note the apps’ deceptive practices were correctly identified in their review sections. So make sure you read the reviews of any app you’re about to install if it doesn’t come from a trusted app developer.


 Credit: Dr.Web
Credit: Dr.Web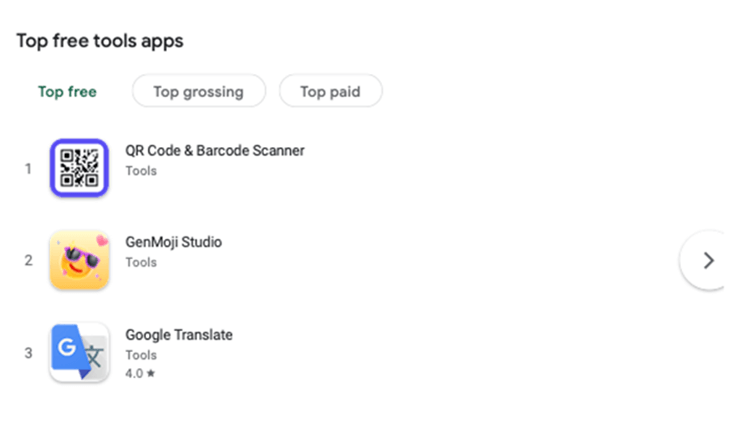 Credit: Checkpoint
Credit: Checkpoint Credit: Lucas Gouveia / Android Police
Credit: Lucas Gouveia / Android Police