Published On : 2026-02-06

Ransomware of the week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found Milkyway Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Milkyway Ransomware
Milkyway is a ransomware strain identified by researchers that targets organizational environments by encrypting files across infected systems. During execution, it systematically encrypts accessible data and appends the “.milkyway” extension to each affected file, rendering them unusable (for example, 2.png becomes 2.png.milkyway). After completing the encryption process, the malware displays a full-screen ransom message to notify the victim of the attack. Based on established ransomware behavior, decryption without the attackers’ assistance is generally not feasible unless the malware contains critical cryptographic flaws. While removing Milkyway from the operating system can halt further encryption activity, it does not reverse the damage already done; encrypted files can only be restored from secure backups created before the infection and stored separately from the compromised network.

Screenshot of files encrypted by the ransomware (Source: Surface Web)
The ransom note asserts that the victim’s entire infrastructure has been compromised, claiming that all servers, workstations, and even backups are unavailable due to encryption. The attackers state that they possess the necessary decryption keys and software but will release them only after receiving payment, emphasizing that no decryption will occur without prepayment. To pressure the victim, the note includes multiple threats, such as leaking stolen data, reporting the organization to tax authorities, security services, and law enforcement, and publicly disclosing sensitive information. It further warns that login credentials and internal information may be shared and that the attackers will contact the victim’s clients and partners directly. The note instructs the victim to initiate contact via a provided Outlook email address, reinforcing the urgency and coercive nature of the demand.
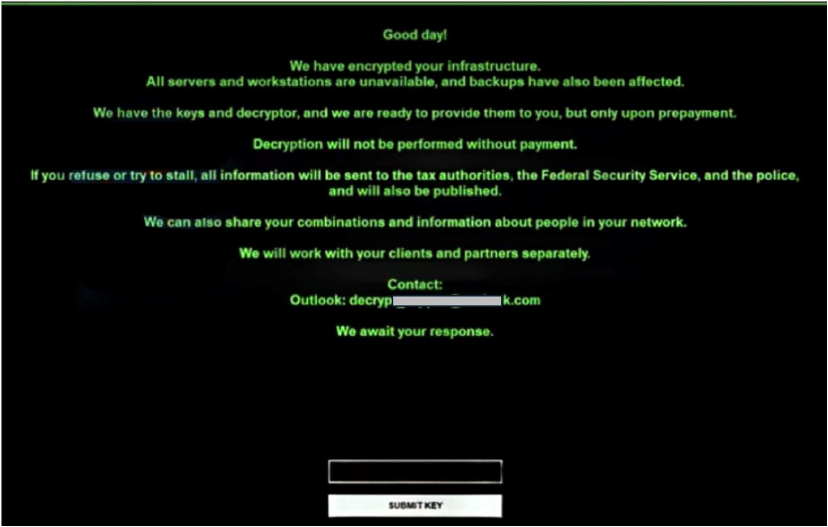
The appearance of the Milkyway ransom note screen (Source: Surface Web)
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Execution | T1569.002 | System Services: Service Execution |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1112 | Modify Registry |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Command and control | T1095 | Non-Application Layer Protocol |
Relevancy and Insights:
- The ransomware primarily affects the Windows operating system, which is commonly utilized in enterprise environments across multiple industries.
- The ransomware maintains long-term presence on the system by creating and modifying Windows scheduled tasks, which allow it to automatically execute even after restarts or user logins. It sets tasks to run with SYSTEM-level privileges and uses recurring triggers such as hourly or logon events. By doing so, the malware ensures its payload is consistently launched, enabling it to finish encryption, re-establish control, or run additional malicious actions without relying on user interaction.
- The ransomware kills processes like vssadmin.exe Delete Shadows /all /quiet and wmic shadowcopy delete /nointeractive to eliminate Volume Shadow Copies, which Windows utilizes for backup and restoration. By deleting these shadow copies, the malware guarantees that victims are unable to retrieve their files through system restore points or backup tools.
- The ransomware terminates processes such as vssadmin.exe Delete Shadows /all/quiet and wmic shadowcopy delete /nointeractive to delete Volume Shadow Copies, which are used by Windows for backup and restore. By deleting shadow copies, the malware prevents victims from restoring their data using built-in recovery features such as system restore points or local backup mechanisms.
- Detect-debug-environment: The ransomware technique is used to determine if it is being monitored in environments such as sandboxes, virtual machines, or under debugging tools. To perform this check, the malware may look for specific processes, drivers, or artifacts linked to analysis tools, measure timing to spot inconsistencies, or scan for system traits uncommon in real user machines. When such conditions are identified, the malicious program can modify its behavior, such as pausing execution, shutting down, or withholding key payload actions to avoid detection and make detailed analysis more difficult.
ETLM Assessment:
CYFIRMA’s assessment indicates that this ransomware is currently in an early or developing state, but it has the potential to evolve into a more sophisticated and damaging threat. As development progresses, Milkyway could mature into a full- scale ransomware operation with improved encryption routines, better evasion techniques, and more reliable execution across complex enterprise environments. Future variants may incorporate advanced obfuscation, privilege escalation, and lateral movement capabilities, enabling broader and faster impact within large networks.
Additionally, Milkyway could transition into a structured ransomware-as-a-service (RaaS) model, allowing affiliates to deploy it in exchange for a share of the profits. This evolution would likely be accompanied by expanded extortion strategies, such as more systematic data theft, targeted pressure campaigns, and customized ransom negotiations. If actively maintained, the ransomware may also adopt mechanisms to disable security tools, exploit unpatched vulnerabilities, and automate propagation, significantly increasing both its reach and its operational effectiveness.
Sigma rule:
title: Uncommon Svchost Command Line Parameter tags:
– attack.defense-evasion
– attack.privilege-escalation
– attack.t1036.005
– attack.t1055
– attack.t1055.012 logsource:
category: process_creation product: windows
detection: selection:
# Example of command to simulate: “C:WindowsSystem32svchost.exe” calc.exe
Image|endswith: ‘svchost.exe’ filter_main_flags:
CommandLine|re: ‘-ksw1,64(s?(-p|-s))?’ filter_main_empty:
CommandLine: ” filter_main_null:
CommandLine: null filter_optional_defender:
ParentImage|endswith: ‘MsMpEng.exe’ CommandLine|contains: ‘svchost.exe’
filter_optional_mrt: ParentImage|endswith: ‘MRT.exe’ CommandLine: ‘svchost.exe’
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_* falsepositives:
– Unlikely level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATIONS
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local environments.
- Ensure that backups of critical systems are maintained, which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATIONS
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is a requirement to inform the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATIONS
- Update all applications/software regularly with the latest versions and security patches alike.
- Add the Sigma rule for threat detection and monitoring, which will help to detect anomalies in log events and identify and monitor suspicious activities.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
Trending Malware of the Week
Type: Infostealer RAT| Objectives: Espionage| Threat Actor: Unknown| Target Technology: Windows OS | Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “Pulsar RAT” is trending.
Overview of Operation Pulsar RAT
Security researchers have uncovered a highly covert Windows-based malware operation that reflects how modern cyber threats are evolving toward stealth, persistence, and long-term exploitation. Instead of relying on obvious malicious files or noisy exploits, this campaign quietly embeds itself into systems using legitimate Windows components and trusted processes. By blending into normal activity, the malware significantly reduces its visibility, allowing attackers to operate for extended periods without raising suspicion.
Once established, the threat deploys its core functionality directly into system memory rather than storing traditional executable files on disk. This approach helps it avoid detection by many conventional security tools and makes forensic analysis more difficult. The malware is structured in a modular fashion, meaning different components handle different tasks, such as maintaining access, gathering information, and communicating with remote operators. This flexible design allows attackers to update or replace individual parts without rebuilding the entire framework.
The campaign is primarily focused on collecting valuable data and enabling remote control of infected machines. It targets a wide range of information, including saved credentials, personal communications, and details about installed applications and system configurations. In addition, it can activate surveillance features such as screen monitoring, audio capture, and camera access, effectively turning compromised systems into silent monitoring devices. Stolen data is then sent out using popular online platforms, helping the attackers hide malicious traffic within everyday internet usage.
Overall, this activity illustrates a broader shift toward memory-resident, multi-stage malware that prioritizes stealth and endurance over quick impact. The use of publicly available tools combined with heavily modified malicious code shows how threat actors can rapidly build powerful operations without developing everything from scratch. For defenders, this reinforces the importance of behavior-based detection and continuous monitoring, as traditional signature-focused security alone is no longer sufficient to counter these increasingly sophisticated threats.
Attack Method
The attack observed in this campaign follows a carefully engineered, multi-layer execution chain designed to establish stealthy persistence, deploy payloads entirely in memory, and maintain continuous control of compromised systems. Initial access is achieved through an obfuscated batch script that copies itself into a concealed per- user directory and registers a randomized entry within the Windows Run registry key. This ensures execution at every user logon without requiring administrative privileges. Rather than dropping a malicious executable, the batch file extracts an embedded Base64-encoded PowerShell payload from within its own contents, writes it temporarily to disk, launches it using a hidden PowerShell instance with execution policy bypass enabled, and then deletes the script. This self-extracting and self-cleaning behavior minimizes static artifacts while reliably transitioning the attack into its next stage.
The decoded PowerShell script functions as an advanced in-memory loader. It contains an encrypted byte array that is decrypted at runtime using a bitwise XOR routine, producing shellcode generated by the Donut framework. To execute this shellcode, the script dynamically compiles C# code inside PowerShell that exposes native Windows API functions, such as OpenProcess, VirtualAllocEx, WriteProcessMemory, and CreateRemoteThread. After an intentional delay intended to evade sandbox detection, the loader injects the decrypted shellcode into a legitimate process and spawns a remote thread to begin execution. This approach allows the core payload to run inside a trusted Windows process while avoiding the creation of a visible executable on disk.
A persistent watchdog mechanism is embedded within the same PowerShell loader to guarantee long-term execution. The script continuously monitors whether the injected process is still alive and, if it terminates, automatically selects another commonly trusted process and repeats the injection sequence. This results in continuous process migration, making takedown efforts more complex because killing a single process does not eliminate the infection. The use of widely present system processes as hosts also obscures malicious activity within normal operating system behavior.
Once active, the injected shellcode decrypts and loads an obfuscated .NET assembly directly into memory. This assembly acts as a combined remote access trojan and information stealer. It establishes encrypted communication with command-and- control infrastructure, enumerates system and user details, harvests credentials and application data, and supports attacker-issued commands such as remote shell access, file management, and surveillance. Collected information is packaged into compressed archives and exfiltrated through commonly used cloud-based messaging services, allowing outbound traffic to blend into legitimate network patterns. Together, these steps form a tightly integrated attack method that prioritizes stealth, resilience, and sustained control over compromised environments.
The following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic (ID) | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| T1059.001 | Command and Scripting Interpreter: PowerShell | |
| T1059.005 | Command and Scripting Interpreter: Visual Basic | |
| T1059.006 | Command and Scripting Interpreter: Python | |
| T1059.007 | Command and Scripting Interpreter: JavaScript | |
| T1106 | Native API | |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| T1070 | Indicator Removal | |
| T1027.002 | Obfuscated Files or Information: Software Packing | |
| T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File | |
| T1027.015 | Obfuscated Files or Information: Compression | |
| T1620 | Reflective Code Loading | |
| Discovery | T1057 | Process Discovery |
| Command and control | T1105 | Ingress Tool Transfer |
| T1071 .001 | Application Layer Protocol: Web Protocols |
INSIGHTS
- One important insight from this malware operation is how threat actors are increasingly prioritizing concealment over speed. Rather than aiming for rapid disruption or immediate monetization, the attackers invest significant effort into staying unnoticed for as long as possible. This reflects a strategic shift toward campaigns that value quiet persistence and gradual data collection, suggesting that attackers now view prolonged access itself as a high-value asset.
- Another notable insight is the growing convergence between commodity malware and advanced threat techniques. Tools and frameworks that were once associated mainly with high-end actors are now being combined with widely available components, creating hybrid threats that blur traditional classifications. This blending lowers the barrier for building complex campaigns while still producing malware that behaves in sophisticated ways, complicating how analysts label and categorize such activity.
- A further insight lies in how attackers exploit everyday digital ecosystems to support their operations. By using common online platforms and services as part of their workflow, malicious activity becomes harder to distinguish from normal user behavior. This reliance on familiar infrastructure highlights how modern malware campaigns are no longer isolated technical constructs, but rather integrated into the same digital environments that legitimate users depend on every day.
ETLM ASSESSMENT
From an ETLM perspective, CYFIRMA assesses that this activity signals a future in which malware operations increasingly favor quiet, long-term positioning inside enterprise environments rather than short-lived, disruptive attacks. As these campaigns become more patient and adaptive, organizations are likely to face a steady rise in incidents where compromise is only discovered after significant data has already been collected or systems have been quietly manipulated. For employees, this trend may translate into greater exposure to indirect consequences of compromise, such as misuse of their digital identities, monitoring of everyday work activities, and erosion of personal privacy within corporate systems. Over time, the cumulative effect of these developments is expected to reshape organizational risk landscapes, where the impact of hidden, prolonged intrusions becomes as damaging as large-scale, visible breaches, fundamentally altering how businesses perceive and experience cyber risk.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule WIN_MultiStage_Donut_Pulsar_Stealer
meta:
description = “Detects malware based on MD5 hashes, file names, and C2 IP” author = “CYFIRMA”
date = “2026-02-02”
malware_family = “Donut Loader / Pulsar RAT / Stealer” strings:
/* — MD5 Hashes — */
$md5_bat = “648c0ba2bb1cde47fa8812f254821a72” ascii
$md5_ps1 = “69392e0d2b877cb932ab709ebe758975” ascii
$md5_client = “666493877fb7328c3e8c313fbcfdfd1e” ascii
$md5_pulsar = “0020b06dc2018cc2b5bf98945a39cbd3” ascii
$md5_stealer = “3abcad7678dd78832a164349aceeaa59” ascii
/* — File Names — */
$fn_bat = “0a1a98b5f9fc7c62.bat” ascii
$fn_ps1 = “ps_7b948266.ps1” ascii
$fn_pulsar = “Pulsar.Common.dll” ascii
$fn_stealer = “Stealerv37.dll” ascii
/* — C2 Indicator — */
$c2_ip = “185.132.53.17:7800” ascii
condition:
any of ($md5_*) or any of ($fn_*) or $c2_ip
Recommendations:
STRATEGIC RECOMMENDATIONS
- Adopt a Behavior-Centric Security Strategy: Shift organizational security posture toward behavior-based detection and analytics to identify stealthy, in-memory threats that evade traditional signature-driven controls.
- Strengthen Enterprise-Wide Visibility: Implement centralized logging and telemetry across endpoints, servers, and network infrastructure to improve detection of anomalous activity and long-dwell intrusions.
- Integrate Threat Intelligence into Security Operations: Establish processes to continuously ingest, validate, and operationalize threat intelligence to keep defensive controls aligned with evolving attacker techniques.
MANAGEMENT RECOMMENDATIONS
- Formalize Cyber Risk Governance: Define clear ownership, escalation paths, and accountability for cybersecurity risk at both technical and executive levels.
- Sustain Investment in Security Capabilities: Allocate budget for modern EDR, NDR, and security analytics platforms that can detect memory-resident and multi-stage attacks.
- Enhance Workforce Awareness: Conduct regular security awareness programs focused on malware delivery methods, social engineering, and safe computing practices.
TACTICAL RECOMMENDATIONS
- Strict Application and Update Governance: Enforce application control policies that restrict software installation and updates exclusively to verified, trusted, and digitally signed sources to reduce exposure to trojanized or fake update packages.
- Harden PowerShell and Script Execution: Enable script logging, constrained language mode, and execution policy enforcement to limit abuse of scripting environments.
- Monitor Persistence Mechanisms: Continuously audit registry Run keys, scheduled tasks, and startup folders for unauthorized entries.
- Network Egress Monitoring: Inspect outbound traffic for unusual connections to cloud services, messaging platforms, and untrusted external hosts.
CYFIRMA’S WEEKLY INSIGHTS
1. Weekly Attack Types and Trends
Key Intelligence Signals:
- Attack Type: Ransomware Attacks, Spear-Phishing, Vulnerabilities & Exploits, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains, Espionage.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware – Everest Ransomware, The Gentlemen Ransomware| Malware – Pulsar RAT
- Everest Ransomware – One of the ransomware groups.
- The Gentlemen Ransomware – One of the ransomware groups.
Please refer to the trending malware advisory for details on the following: - Malware – Pulsar RAT
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.
2. Threat Actor in Focus
DRAGONFLY (TA17-293A): Cyber Operations and Strategic Impact Analysis
- Threat Actor: Dragonfly
- Attack Type: Credential Dumping, Spear-Phishing, Malware Implant, Watering Hole Attack, Exploitation of Vulnerabilities, Staged Target
- Objective: Information theft, Espionage, Financial Gains
- Suspected Target Technology: Office Suites Software, Operating System, Web Application
- Suspected Target Geography: China, France, Germany, Ireland, Italy, Japan, Poland, Spain, Turkey, United Kingdom, United States
- Suspected Target Industries: Airlines, Capital Goods, Construction & Engineering, Energy, Energy Equipment & Services, Government, ICS, Manufacturing, Pharmaceuticals, Aviation, Engineering, Industrial, Nuclear, Scada, Water
- Business Impact: Financial Loss, Data Theft, Operational Disruption, Reputational Damage
About the Threat Actor
DRAGONFLY is a Russian threat actor active since at least 2011, with a long-standing focus on the energy sector and other critical infrastructure. The group resurfaced in September 2017, conducting attacks against energy organizations across Asia, Europe, and North America. DRAGONFLY has also been linked to the major cyberattacks on Ukraine’s power grid in 2015 and 2016, which resulted in widespread power outages.
Also known by aliases such as Energetic Bear, Crouching Yeti, Group 24, Koala Team, Bersek Bear, and Anger Bear, DRAGONFLY primarily targets ICS and SCADA environments. Its notable campaign, TA17-293A, demonstrates a structured two-phase attack approach in which initial compromises of staging targets are used as pivot points to launch further attacks against larger, intended targets.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2023-22518 | Confluence Data Center and Server | 9.8 | Link |
| CVE-2017-17215 | Huawei HG532 | 8.8 | – |
| CVE-2023-4966 | NetScaler ADC and NetScaler Gateway | 7.5 | Link |
| CVE-2023-36884 | Microsoft Windows and Netlogon Remote Protocol (MS-NRPC) | 10.0 | Link1, Link2 |
| CVE-2020-0688 | Microsoft Exchange software | 8.8 | Link1, Link2 |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1595.002 | Active Scanning: Vulnerability Scanning |
| Reconnaissance | T1591.002 | Gather Victim Org Information: Business Relationships |
| Reconnaissance | T1598.002 | Phishing for Information: Spear phishing Attachment |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Resource Development | T1608.004 | Stage Capabilities: Drive-by-Target |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server |
| Resource Development | T1584.004 | Compromise Infrastructure: Server |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1195.002 | Supply Chain Compromise: Compromise Software Supply Chain |
| Initial Access | T1078 | Valid Accounts |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Persistence | T1133 | External Remote Services |
| Persistence | T1112 | Modify Registry |
| Persistence | T1078 | Valid Accounts |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1136.001 | Create Account: Local Account |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1098.007 | Account Manipulation: Additional Local or Domain Groups |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1098.007 | Account Manipulation: Additional Local or Domain Groups |
| Privilege Escalation | T1078 | Valid Accounts |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1221 | Template Injection |
| Defense Evasion | T1036.010 | Masquerading: Masquerade Account Name |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1078 | Valid Accounts |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1562.004 | Impair Defenses: Disable or Modify System Firewall |
| Defense Evasion | T1564.002 | Hide Artifacts: Hidden Users |
| Credential Access | T1110 | Brute Force |
| Credential Access | T1110.002 | Brute Force: Password Cracking |
| Credential Access | T1187 | Forced Authentication |
| Credential Access | T1003.002 | OS Credential Dumping: Security Account Manager |
| Credential Access | T1003.003 | OS Credential Dumping: NTDS |
| Credential Access | T1003.004 | OS Credential Dumping: LSA Secrets |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1069.002 | Permission Groups Discovery: Domain Groups |
| Discovery | T1012 | Query Registry |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Lateral Movement | T1210 | Exploitation of Remote Services |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1560 | Archive Collected Data |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Collection | T1114.002 | Email Collection: Remote Email Collection |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071.002 | Application Layer Protocol: File Transfer Protocols |
| Command and Control | T1105 | Ingress Tool Transfer |
Latest Developments Observed
Researchers report that the threat actor is suspected of targeting over 30 Polish organisations in renewable energy, manufacturing, and energy/utilities sectors, aiming for operational disruption and long-term espionage. The initial access vector is believed to be the exploitation of a vulnerable FortiGate appliance. These suspected attacks reflect sustained interest in critical industrial and infrastructure networks.
ETLM Insights
DRAGONFLY conducts strategically driven cyber operations where intelligence collection, disruption, and operational positioning outweigh financial motives. The threat actor targets energy, manufacturing, and other critical infrastructure, leveraging access to OT/ICS networks to undermine operational resilience and gain asymmetric strategic leverage.
The actor employs a methodical approach, exploiting exposed perimeter devices for initial access, followed by internal reconnaissance, credential abuse, lateral movement, and privilege escalation. Compromised staging entities are used to expand reach, maintain footholds, and support long-term intelligence collection against high-value targets.
Recent activity highlights destructive and hybrid techniques, including custom wiper deployment, controller manipulation, and file deletion, alongside ongoing interest in SCADA modernization and OT infrastructure. DRAGONFLY is expected to further refine OT-focused tradecraft, strengthen persistence across IT–OT environments, and maintain readiness for timed disruption aligned with strategic objectives.
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
YARA Rules
rule Dragonfly_Campaign_Indicators
meta:
author = “CYFIRMA”
description = “Detects artifacts associated with Dragonfly-related activity based on CVEs, IPs, domains, and files”
reference = “Internal Threat Intel” date = “2026-02-03”
strings:
// CVEs
$cve1 = “CVE-2023-22518”
$cve2 = “CVE-2017-17215”
$cve3 = “CVE-2023-4966”
$cve4 = “CVE-2020-1472”
$cve5 = “CVE-2020-0688”
// IPs
$ip1 = “69.172.201.208”
$ip2 = “117.18.237.29”
$ip3 = “171.25.193.25”
$ip4 = “23.227.38.74”
$ip5 = “23.227.38.32”
// Domains
$domain1 = “tureg.info”
$domain2 = “satanal.info”
$domain3 = “user.name”
$domain4 = “adatum.com”
$domain5 = “5iantlavalamp.com”
// Files
$file1 = “hrm3jvh9v.dll”
$file2 = “exe159d860d0cfa59816c686e4a9914113.exe”
$file3 = “e159d860d0cfa59816c686e4a9914113.exe”
condition:
any of ($cve*) or any of ($ip*) or any of ($domain*) or any of ($file*)
Recommendations
Strategic Recommendations
- Incorporate Digital Risk Protection (DRP) as part of the overall security posture to proactively defend against impersonations and phishing attacks.
- Assess and deploy alternatives for an advanced endpoint protection solution that provides detection/prevention for malware and malicious activities that do not rely on signature-based detection methods.
- Deploy Zero Trust Policy that leverages tools like security information management, advanced security analytics platforms, security user behaviour analytics, and other analytics systems to help the organization’s security personnel observe in real-time what is happening within their networks so they can orient defences more intelligently.
Management Recommendations
- Invest in user education and implement standard operating procedures for the handling of financial and sensitive data transactions commonly targeted by impersonation attacks. Reinforce this training with context-aware banners and in- line prompts to help educate users.
- Regularly reinforce awareness of unauthorized attempts with end-users across the environment and emphasize the human weakness in mandatory information security training sessions.
- Move beyond the traditional model of security awareness towards Improved Simulation and training exercises that mimic real attack scenarios, account for behaviors that lead to a compromise, and are measured against real attacks the organization receives.
Tactical Recommendations
- For better protection coverage against email attacks (like spear phishing, business email compromise, or credential phishing attacks), organizations should augment built-in email security with layers that take a materially different approach to threat detection.
- Protect accounts with multi-factor authentication. Exert caution when opening email attachments or clicking on embedded links supplied via email communications, SMS, or messaging.
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Add the YARA rules for threat detection and monitoring, which will help to detect anomalies in log events, identify and monitor suspicious activities.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
3. Major Geopolitical Developments in Cybersecurity
Chinese APTs Hit Asia with High-End Malware
China-linked APT groups continue to intensify cyberattacks across Asia, deploying sophisticated tools against gambling sites and government entities in the region. Researchers have tracked the versatile JScript-based command-and-control framework PeckBirdy since 2023, used by China-aligned threat actors in two distinct campaigns, one primarily financially motivated, in which the group injected malicious scripts into Chinese gambling websites. Another one, tracked from July 2024 onward, has been more espionage-oriented. This campaign targeted Asian government entities, private organizations (including a Philippine educational institution), and other sectors. Attackers injected PeckBirdy links into websites for credential harvesting and malware delivery, using diverse execution methods such as Mshta for remote access, ScriptControl (.NET), Node.js, Windows Script Host (WScript), or Active Server Pages (ASP) environments.
Researchers attribute both campaigns to China-aligned actors, noting overlaps with clusters like Earth Baxia for SHADOW-EARTH-045. The researchers highlight that Chinese APTs often share tools and infrastructure, blurring lines between cybercrime and espionage.
ETLM Assessment:
The Asia-Pacific (APAC) region accounts for over half of global APT activity, fueled by its massive population, major economies (Japan, China, South Korea), geopolitical rivalries, and especially the high volume and sophistication of Chinese state-aligned operations. These actors rank among the world’s most advanced, frequently innovating malware and tactics, techniques, and procedures (TTPs), while sharing resources across loosely affiliated clusters that can include private entities or criminal groups.
Russian cyberattack against Poland’s energy grid compromised 30 sites
The December 2025 coordinated cyberattack that targeted Poland’s electric grid compromised operational technology (OT) systems at approximately 30 distributed energy resource (DER) sites, according to researchers. These included wind farms, solar (photovoltaic) installations, and combined heat and power (CHP) facilities. Researchers described the incident as the first major cyberattack at scale targeting distributed energy resources—the smaller-scale, decentralized wind, solar, and CHP assets increasingly integrated into power grids around the world. The attackers disrupted communication and control systems at affected sites, resulting in loss of view, loss of control, and denial-of-service conditions. They also disabled key equipment in a way that rendered it beyond repair at certain locations. Importantly, the attack did not cause any widespread power outages or disruptions to Poland’s overall electricity supply, as the centralized transmission backbone remained unaffected. This, however, should not lead to complacency, since the adversaries gained access to operational technology systems critical to grid operations and disabled key equipment beyond repair at the site. Due to the lack of electric outages, asset operators and the broader community may be mistaken in thinking this is not overly concerning. In fact, the attack demonstrated that countries that currently or will depend more on DERs should be alarmed. The attack has been attributed to the Russia-linked threat group ELECTRUM, which shows significant technical and operational overlaps with the well-known Russian state-sponsored actor Sandworm (also known as APT44 or linked to Russia’s military intelligence GRU).
ETLM Assessment:
Poland, as a key frontline NATO and EU member bordering both Russia and its ally Belarus, faces heightened risks from Moscow’s hybrid warfare tactics. The country has been one of the strongest supporters of Ukraine since Russia’s full-scale invasion in 2022, serving as a major transit hub for military aid to Kyiv. In recent years, hacker groups frequently linked by Polish authorities to the Kremlin have repeatedly struck critical infrastructure in Poland, including hospitals, water treatment plants, and sewage systems. Tensions further intensified last September when multiple Russian drones violated Polish airspace, raising serious concerns about Moscow’s readiness to challenge NATO’s defenses. In November, Poland publicly blamed Russia for orchestrating explosions that damaged a crucial railway line used for transporting aid to Ukraine. Poland currently ranks among the most targeted nations worldwide for cyberattacks.
4. Rise in Malware/Ransomware and Phishing
Everest Ransomware Impacts Hosokawa Micron Corporation
- Attack Type: Ransomware
- Target Industry: Industrial Manufacturing & Engineering
- Target Geography: Japan
- Ransomware: Everest Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Hosokawa Micron Corporation (https[:]//www[.]hosokawamicron[.]co[.]jp/), was compromised by Everest Ransomware. Hosokawa Micron Corporation is a global leader in powder and particle processing technology, manufacturing equipment for grinding, classifying, mixing, drying, and particle design used across chemicals, pharmaceuticals, food, minerals, and plastics industries. The compromised data contains confidential and sensitive information belonging to the organization. The Total size of data compromised is approximately 30 GB.
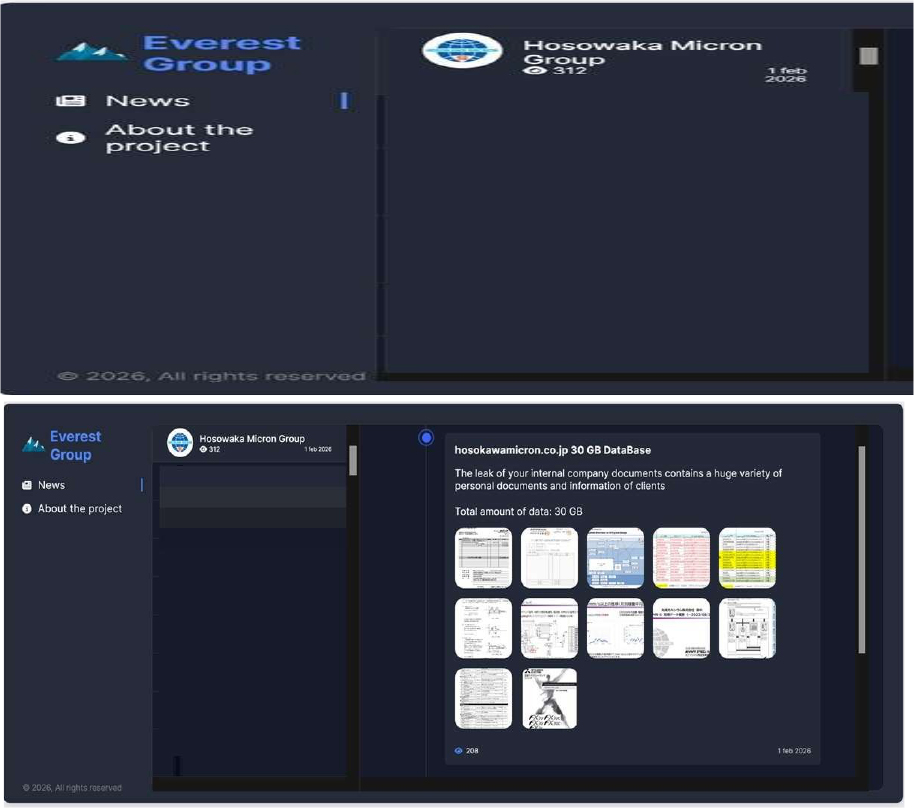
Source: Dark Web
Relevancy & Insights:
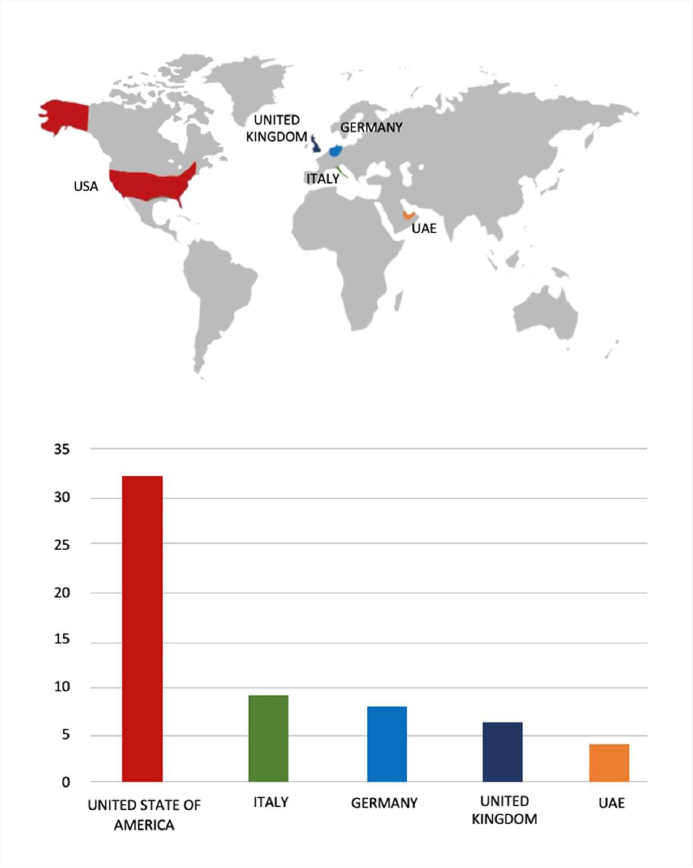
- The Everest Ransomware group primarily targets countries such as the United States of America, Italy, Germany, the United Kingdom, and the United Arab Emirates.
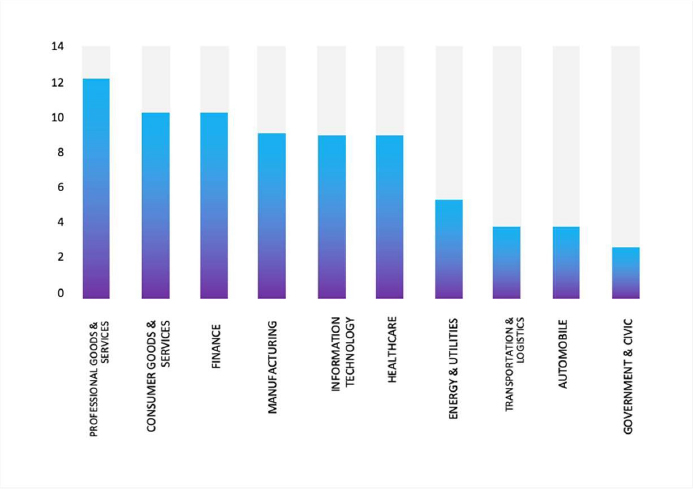
- The Everest Ransomware group primarily targets industries, including Professional Goods & Services, Consumer Goods & Services, Finance, Manufacturing, and Information Technology.
- Based on the Everest Ransomware victims list from 1st Jan 2025 to 03rd Feb 2026, the top 5 Target Countries are as follows:
- The Top 10 Industries most affected by the Everest Ransomware victims list from 1st Jan 2025 to 03rd Feb 2026 are as follows:
ETLM Assessment:
According to CYFIRMA’s assessment, Everest ransomware continues to pose a persistent and evolving cyber threat. The group is actively broadening its targeting across new sectors, expanding its role as an initial access broker, and increasingly relying on data-leak extortion as its core operational tactic. Organizations are advised to remain vigilant by strengthening access controls, closely monitoring for lateral movement and Cobalt Strike–related activity, and maintaining robust incident response and detection capabilities to mitigate the risks posed by Everest’s ongoing campaigns.
The Gentlemen Ransomware Impacts Handsome
Attack Type: Ransomware
Target Industry: Manufacturing
Target Geography: Indonesia
Ransomware: The Gentlemen Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
CYFIRMA observed in an underground forum that a company from Indonesia, Handsome(https[:]//www[.]handsomegroup[.]com/), was compromised by the Gentlemen Ransomware. Handsome Industrial Company, Limited operates as a veteran OEM manufacturer and key production partner for global entertainment giants like Disney and Marvel. Specializing in high-quality toys, electronics, and consumer goods featuring iconic characters, the company maintains production facilities in China and Indonesia to serve major retailers across the United States, Europe, Asia, and Australia. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.

Source: Dark Web
Relevancy & Insights:
- The Gentlemen is a relatively highly sophisticated ransomware-as-a-service (RaaS) group that emerged in mid-2025.
- The Gentlemen Ransomware group primarily targets countries such as the United States of America, Brazil, Vietnam, Thailand, and Indonesia.
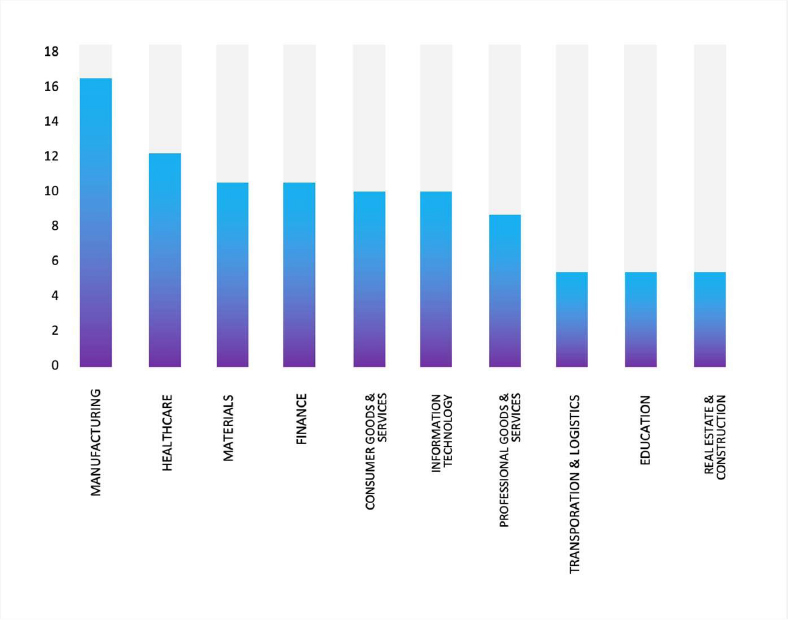
- The Gentlemen Ransomware group primarily targets industries, including Manufacturing, Healthcare, Materials, Finance, and Consumer Goods & Services.
- Based on the Gentlemen Ransomware victims list from 1st July 2025 to 3rd Feb 2026, the top 5 Target Countries are as follows:
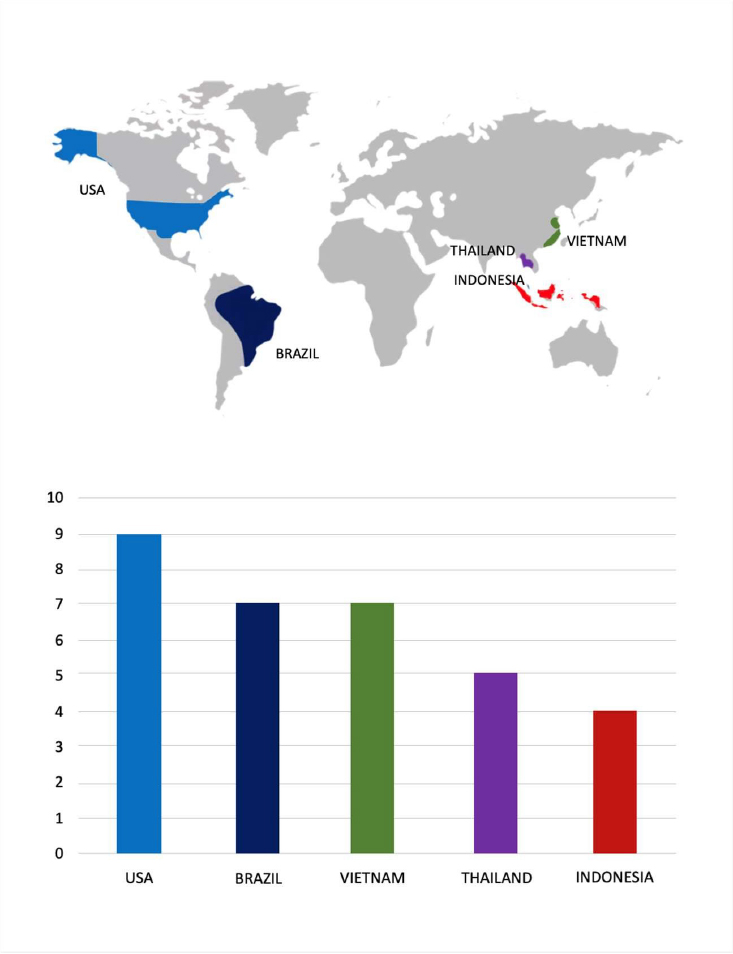
- The Top 10 Industries most affected by the Gentlemen Ransomware victims list from 1st July 2025 to 3rd Feb 2026 are as follows:
ETLM Assessment:
According to CYFIRMA’s assessment, the Gentlemen Ransomware is a highly adaptive and globally active threat that leverages dual-extortion tactics, combining data theft with file encryption. The group employs advanced evasion and persistence techniques, supports cross-platform and scalable ransomware deployment, and conducts targeted attacks across multiple industries and geographic regions. This combination of capabilities makes it a significant risk to enterprise cybersecurity defenses, particularly for organizations with limited detection and incident-response maturity.
5. Vulnerabilities and Exploits
Vulnerability in fast-xml-parser
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Universal components
- Vulnerability: CVE-2026-25128
- CVSS Base Score: 7.5 Source
- Vulnerability Type: Uncaught Exception.
Summary:
The vulnerability allows a remote attacker to perform a denial of service (DoS) attack.
Relevancy & Insights:
The vulnerability exists due to the RangeError issue in the numeric entity.
Impact:
A remote attacker can pass specially crafted input to the application and perform a denial of service (DoS) attack.
Affected Products:
https[:]//github[.]com/NaturalIntelligence/fast-xml- parser/security/advisories/GHSA-37qj-frw5-hhjh/#poc
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
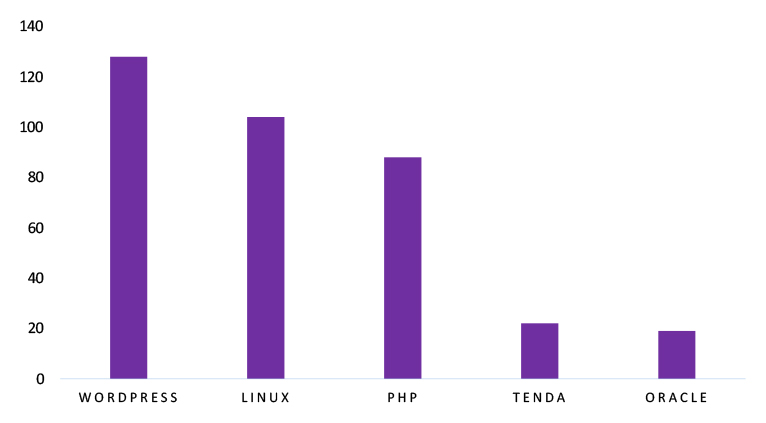
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in fast-xml-parser can pose significant threats to application stability and data processing integrity. This can impact various industries globally, including software development platforms, API-driven services, automation pipelines, and systems that rely on XML parsing for input validation and structured data handling. Ensuring the security of fast-xml-parser is crucial for maintaining the integrity and protection of application workflows, data processing routines, and service reliability across deployments. Therefore, addressing these vulnerabilities is essential to safeguarding data parsing operations, preventing denial-of-service disruptions, and maintaining consistent system performance across different geographic regions and sectors.
6. Latest Cyber-Attacks, Incidents, and Breaches
Sinobi Ransomware attacked and published the data of Impressico Business Solutions
- Threat Actor: Sinobi Ransomware
- Attack Type: Ransomware
- Objective: Data Leak, Financial Gains
- Target Technology: Web Applications
- Target Industry: Information Technology (IT) Services & Consulting
- Target Geography: India
- Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
Recently, we observed that Sinobi Ransomware attacked and published the data of Impressico Business Solutions(https[:]//www[.]impressico[.]com/) on its dark web website. Impressico Business Solutions is a global digital transformation and IT services company that delivers technology solutions and consulting to clients across multiple industries. Headquartered in Noida, India, the company also has operations in the United States, the United Kingdom, Canada, and other regions. The ransomware incident led to the compromise of approximately 150 GB of data, including Contracts, Financial data, and Customer data.
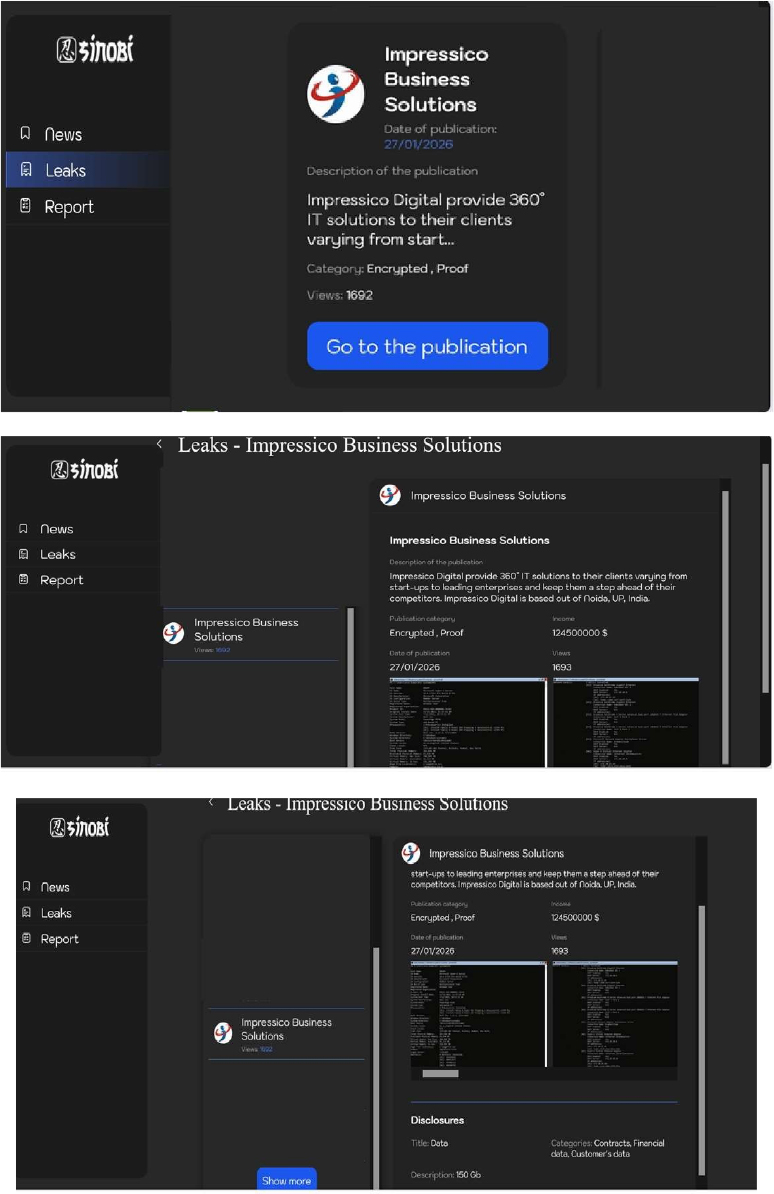
Source: Dark Web
Relevancy & Insights:
- Sinobi Ransomware is a ransomware threat first observed in 2025, suspected to be a rebrand or splinter of the Lynx Ransomware group.
- Sinobi ransomware uses a combination of Curve-25519 Donna and AES-128-CTR encryption, a technique also seen in high-profile ransomware like Babuk, making file recovery virtually impossible without the attacker’s private key.
ETLM Assessment:
According to CYFIRMA’s assessment, Sinobi Ransomware represents a persistent threat in the ransomware landscape, capable of disruptive attacks on both enterprises and mid-sized organisations.
7. Data Leaks
LinkUMKM Advertised on a Leak Site
- Attack Type: Access sale
- Target Industry: Financial Services Technology (FinTech)
- Target Geography: Indonesia
- Objective: Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
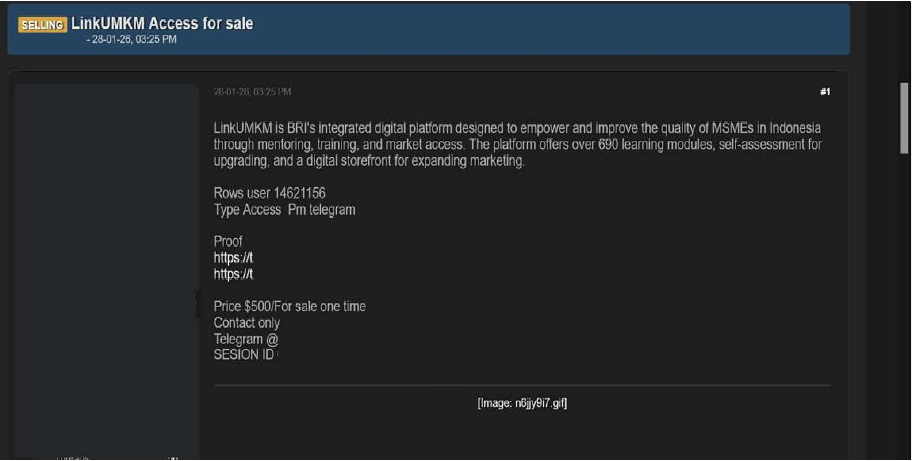
The CYFIRMA research team has identified claims made by a threat actor operating under the alias “KaruHunters,” who alleges responsibility for an unauthorized access sale related to LinkUMKM. LinkUMKM is an integrated digital platform operated by PT Bank Rakyat Indonesia (Persero) Tbk (BRI), designed to support and enhance the capabilities of Micro, Small, and Medium Enterprises (MSMEs) in Indonesia through mentoring, training, and expanded market access. The platform provides more than 690 learning modules, business self-assessment tools for MSME upgrading, and a digital storefront to support marketing expansion.
According to the threat actor, the alleged access involves 14,621,156 user records, with the access being offered privately via Telegram direct messages. The actor is reportedly seeking USD 500 for a one-time sale of the access.
At the time of reporting, the authenticity of this access sale remains unverified, as the claim is based solely on information provided by the threat actor and has not been independently validated.
Source: Underground Forums
Argaam Investment Company (Argaam) Data Advertised on a Leak Site
- Attack Type: Data leak
- Target Industry: Financial Information Services / Financial Data & Analytics
- Target Geography: Saudi Arabia
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary
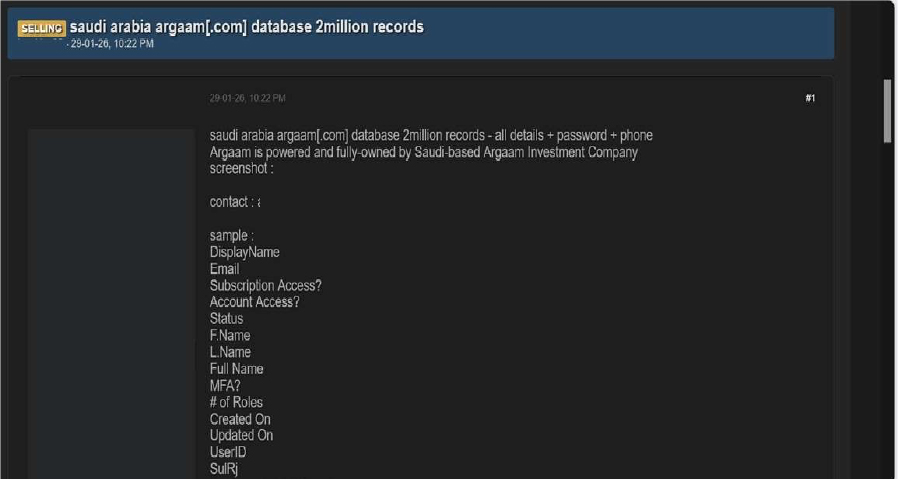
The CYFIRMA research team observed that Argaam Investment Company (Argaam), the Arab world’s leading financial news portal and data provider, has reportedly suffered a significant data breach. A threat actor “pking25” is claiming to sell a database containing 2 million records, asserting that it includes comprehensive user details and credentials. Argaam, which provides real-time updates on financial markets and macroeconomics in Saudi Arabia, is a critical information hub for investors and C-level executives across the Gulf region.
The actor provided a screenshot of what appears to be an administrative interface titled “All Users”. This panel displays sensitive information, including user IDs, display names, and email addresses, with a navigation bar suggesting thousands of pages of records.
The allegedly compromised data includes:
- Full names
- Email addresses
- Phone numbers
- Passwords
- Display names
- User IDs
- Account status (e.g., Active)
- Multi-factor authentication (MFA) status
- Subscription and account access levels
- Account creation and update timestamps
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “KaruHunters” is a highly active and sophisticated group specializing in data leaks. Numerous credible sources attribute multiple security breaches to this group, involving unauthorized access to systems and the illicit sale of stolen data on dark web marketplaces. KaruHunters’ operations highlight the persistent and evolving nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to enhance their cybersecurity posture through continuous monitoring, leveraging advanced threat intelligence, and adopting proactive defense strategies to protect sensitive data and vital infrastructure.
Recommendations: Enhance the cybersecurity posture by:
1. Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being exploited.
2. Ensure proper database configuration to mitigate the risk of database-related attacks.
3. Establish robust password management policies, incorporating multi-factor authentication and role-based access to fortify credential security and prevent unauthorized access.
8. Other Observations
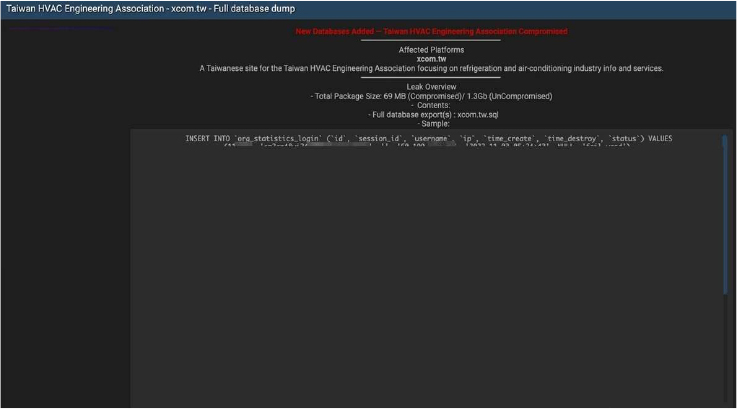
The CYFIRMA Research team observed that the Taiwan HVAC Engineering Association (THA), a professional trade organization dedicated to the refrigeration and air-conditioning industry in Taiwan, has reportedly suffered a significant data breach.
The leaked information appears to include sensitive administrative records, user credentials, and tender-related data involving various educational and government institutions across Taiwan. Sample data suggests the breach impacts several schools and municipal offices, including the Taichung City Lixing Elementary School and the Ministry of Justice’s Bade Exterior Prison.
The allegedly compromised data includes:
- Full names
- Email addresses
- Usernames and plain-text passwords
- IP addresses and login session IDs
- Contact telephone and mobile numbers
- Home and company addresses
- Birthday and gender information
- Professional titles and educational backgrounds
- Government tender details and project descriptions
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
Source: Underground Forums
RECOMMENDATIONS
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organisations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, and active network monitoring, through next-generation security solutions and a ready-to-go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence, providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied, and the proper implementation of security technologies, followed by corrective actions, remediations, and lessons learned.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcomings of EDR and SIEM solutions.
- Ensure that detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies should be continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defences based on the tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security controls, such as reCAPTCHA (completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.
Situational Awareness – Cyber News
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.

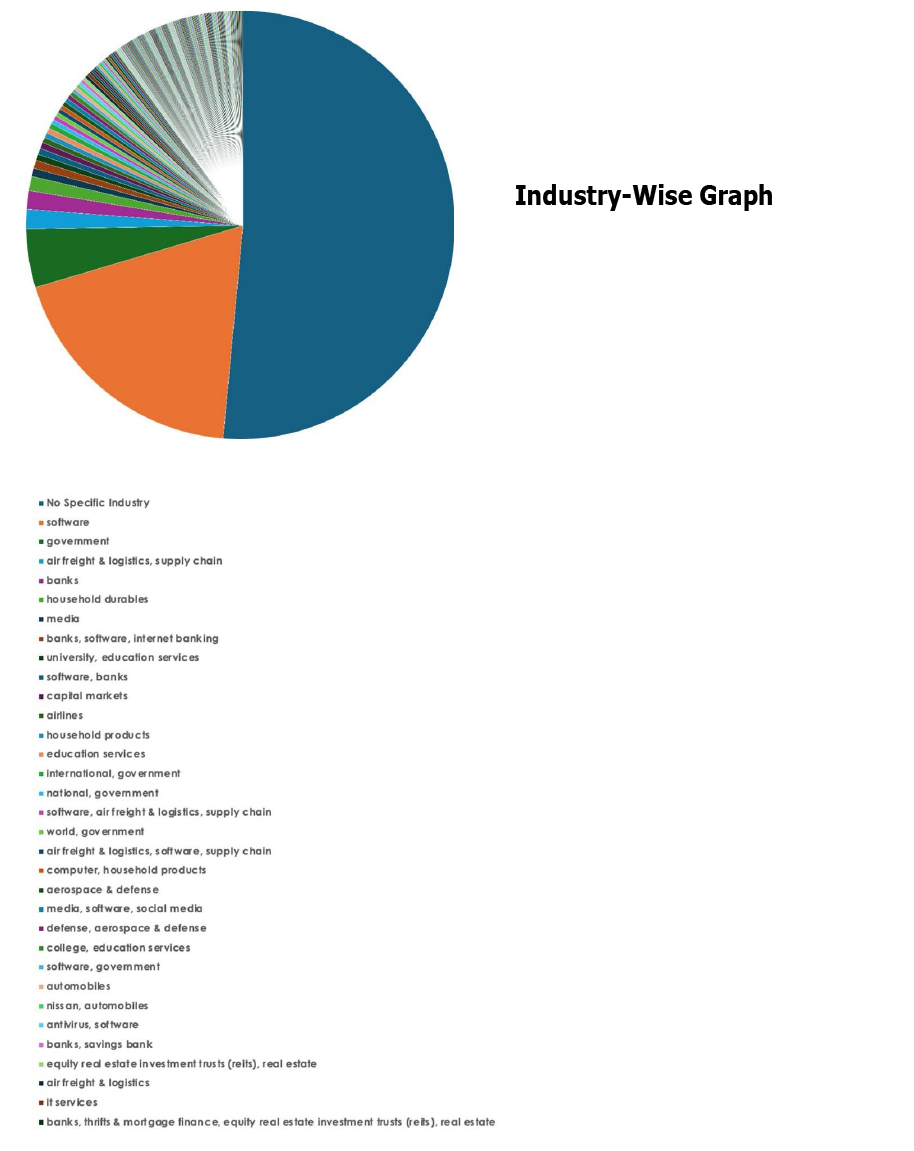
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.
