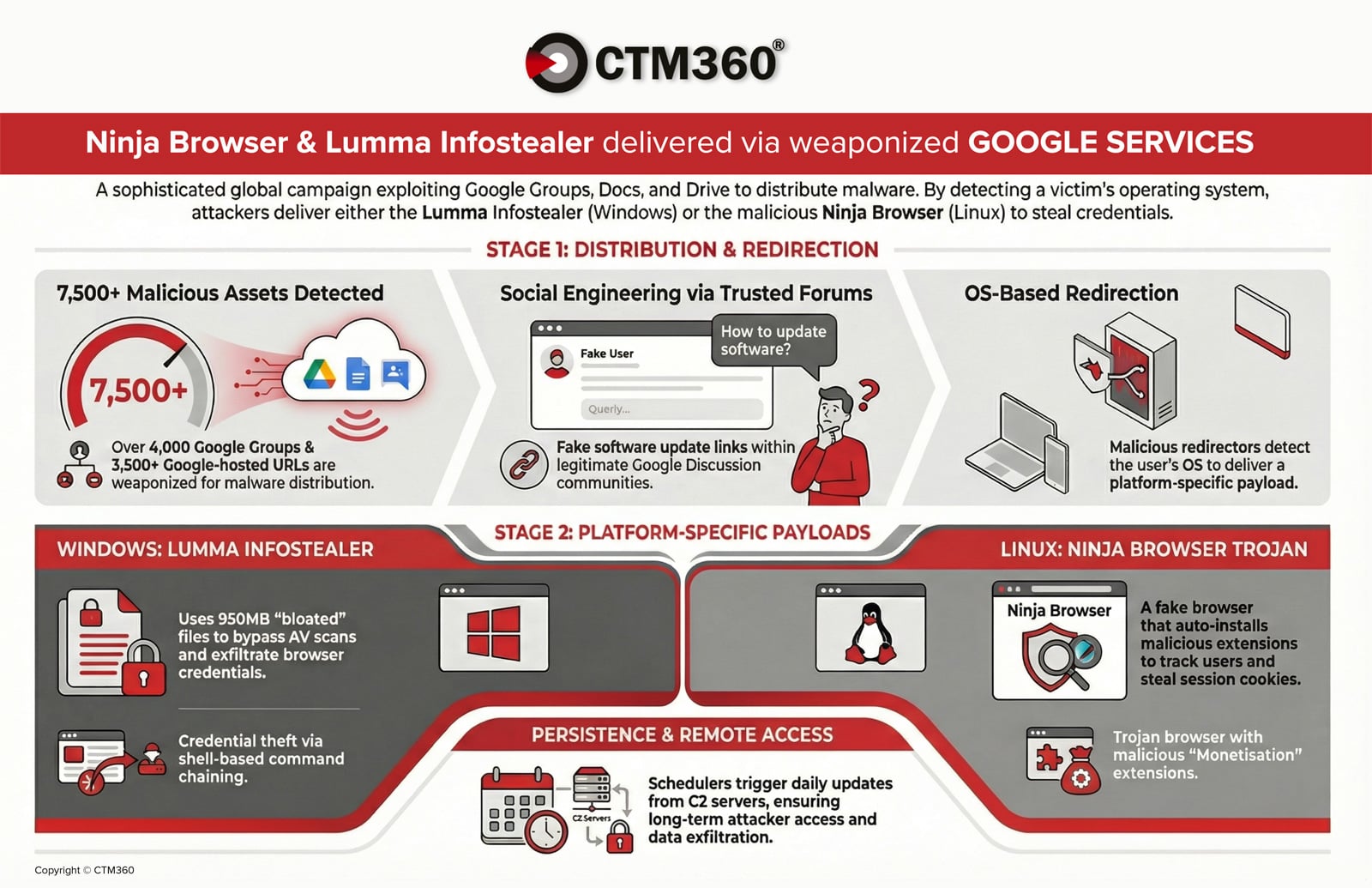
CTM360 reports that more than 4,000 malicious Google Groups and 3,500 Google-hosted URLs are being used in an active malware campaign targeting global organizations.
The attackers abuse Google’s trusted ecosystem to distribute credential-stealing malware and establish persistent access on compromised devices.
The activity is global, with attackers embedding organization names and industry-relevant keywords into posts to increase credibility and drive downloads.
Read the full report here: https://www.ctm360.com/reports/ninja-browser-lumma-infostealer
How the campaign works
The attack chain begins with social engineering inside Google Groups. Threat actors infiltrate industry-related forums and post technical discussions that appear legitimate, covering topics such as network issues, authentication errors, or software configurations
Within these threads, attackers embed download links disguised as: “Download Organization_Name for Windows 10”
To evade detection, they use URL shorteners or Google-hosted redirectors via Docs and Drive. The redirector is designed to detect the victim’s operating system and deliver different payloads depending on whether the target is using Windows or Linux
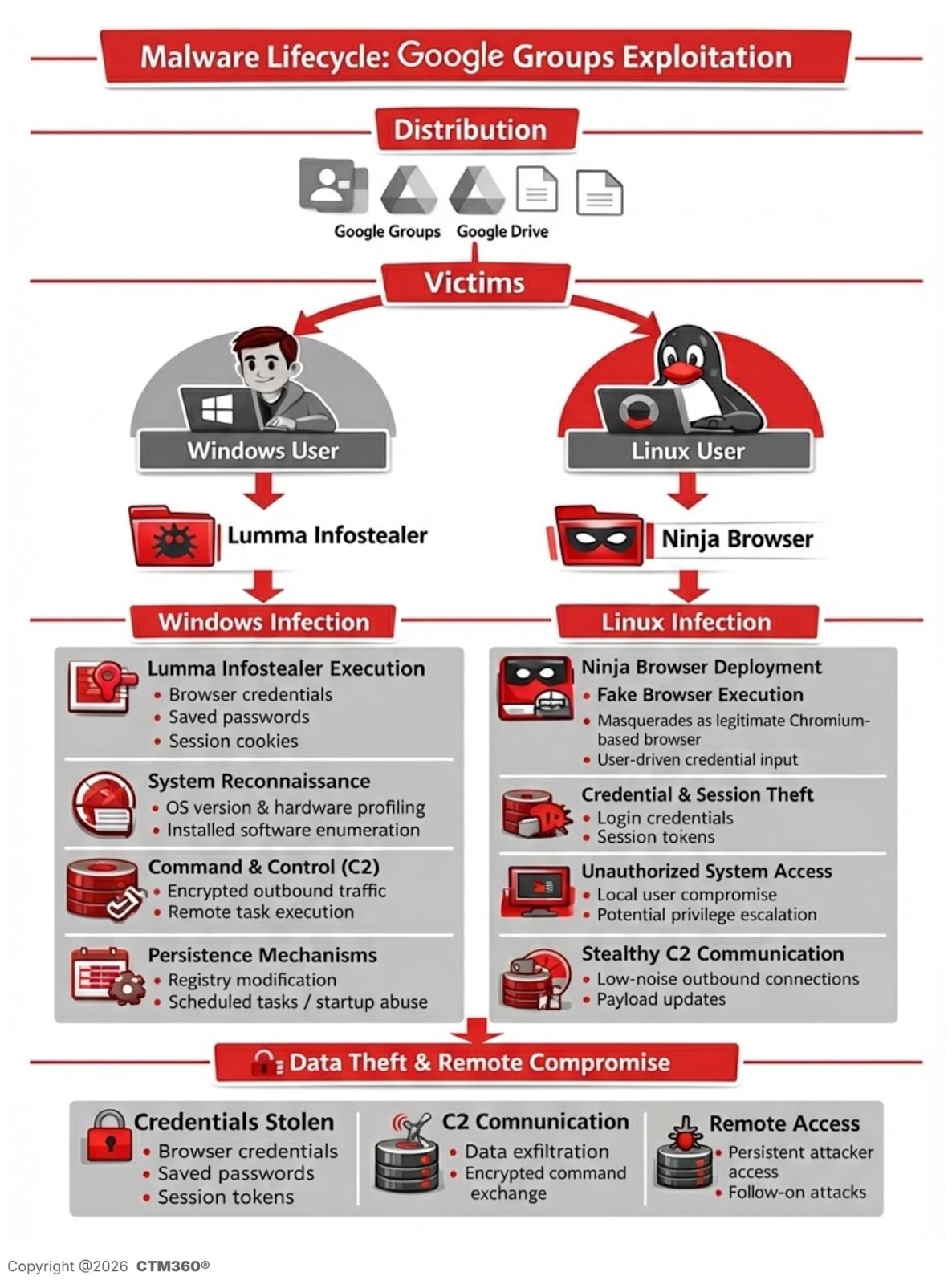
Windows Infection Flow: Lumma Info-Stealer
For Windows users, the campaign delivers a password-protected compressed archive hosted on a malicious file-sharing infrastructure
Oversized archive to evade detection
The decompressed archive size is approximately 950MB, though the actual malicious payload is only around 33MB. CTM360 researchers found that the executable was padded with null bytes — a technique designed to exceed antivirus file-size scanning thresholds and disrupt static analysis engines.
AutoIt-based reconstruction
Once executed, the malware:
-
Reassembles segmented binary files.
-
Launches an AutoIt-compiled executable.
-
Decrypts and executes a memory-resident payload.
The behavior matches Lumma Stealer, a commercially sold infostealer frequently used in credential-harvesting campaigns
Observed behavior includes:
-
Browser credential exfiltration.
-
Session cookie harvesting.
-
Shell-based command execution.
-
HTTP POST requests to C2 infrastructure (e.g., healgeni[.]live).
-
Use of multipart/form-data POST requests to mask exfiltrated content.
CTM360 identified multiple associated IP addresses and SHA-256 hashes linked to the Lumma-stealer payload.
CTM360 identified thousands of fraudulent HYIP websites that mimic legitimate crypto and forex trading platforms and funnel victims into high-loss investment traps.
Get insights into attacker infrastructure, fake compliance signals, and how these scams monetize through crypto wallets, cards, and payment gateways.
Linux Infection Flow: Trojanized “Ninja Browser”
Linux users are redirected to download a trojanized Chromium-based browser branded as “Ninja Browser.”
The software presents itself as a privacy-focused browser with built-in anonymity features.
However, CTM360’s analysis reveals that it silently installs malicious extensions without user consent and implements hidden persistence mechanisms that enable future compromise by the threat actor.
Malicious extension behavior
A built-in extension named “NinjaBrowserMonetisation” was observed to:
-
Track users via unique identifiers
-
Inject scripts into web sessions
-
Load remote content
-
Manipulate browser tabs and cookies
-
Store data externally
The extension contains heavily obfuscated JavaScript using XOR and Base56-like encoding
While not immediately activating all embedded domains, the infrastructure suggests future payload deployment capability.
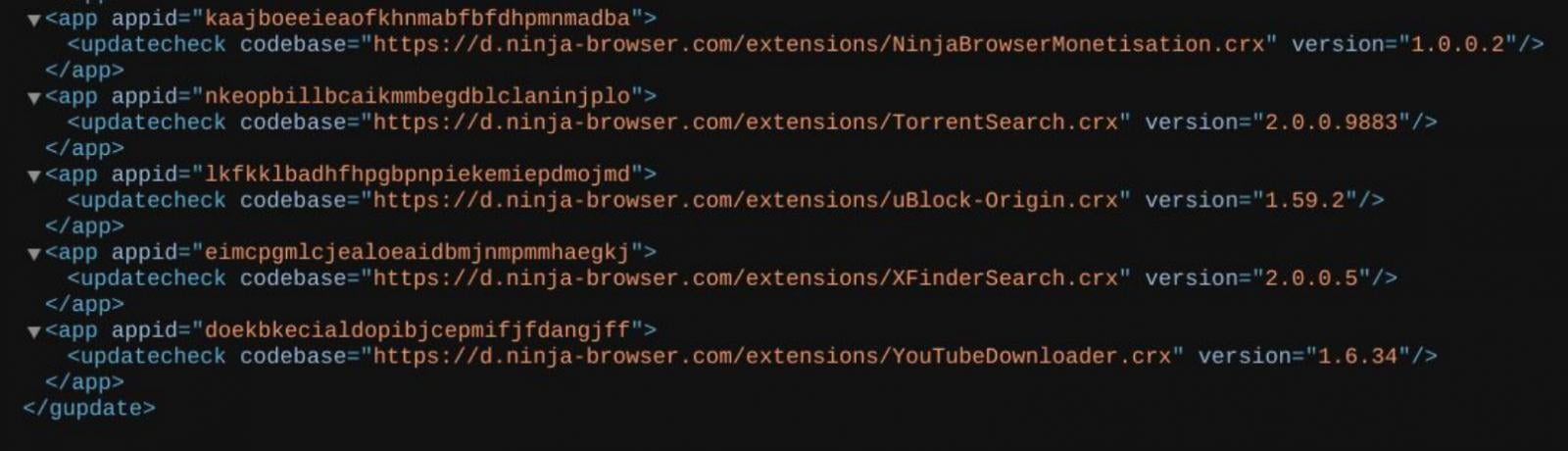
Source: CTM360
Silent persistence mechanism
CTM360 also identified scheduled tasks configured to:
-
Poll attacker-controlled servers daily
-
Silently install updates without user interaction
-
Maintain long-term persistence
Additionally, researchers observed that the browser defaults to a Russian-based search engine named “X-Finder” and redirects to another suspicious AI-themed search page
The infrastructure appears tied to domains such as:
-
ninja-browser[.]com
-
nb-download[.]com
-
nbdownload[.]space
Campaign Infrastructure & Indicators of Compromise
CTM360 linked the activity to infrastructure, including:
IPs:
-
152.42.139[.]18
-
89.111.170[.]100
C2 domain:
-
healgeni[.]live
Multiple SHA-256 hashes and domains associated with credential harvesting and info-stealer distribution were identified and are available in the report.
Risks to organizations
Lumma Stealer risks:
-
Credential and session token theft
-
Account takeover
-
Financial fraud
-
Lateral movement in enterprise environments
Ninja Browser risks:
-
Silent credential harvesting
-
Remote command execution
-
Backdoor-like persistence
-
Automatic malicious updates without user consent
Because the campaign abuses Google-hosted services, the attack bypasses traditional trust-based filtering mechanisms and increases user confidence in malicious content.
Defensive recommendations
CTM360 advises organizations to:
-
Inspect shortened URLs and Google Docs/Drive redirect chains.
-
Block the IoCs at firewall and EDR levels.
-
Educate users against downloading software from public forums/sources without verification.
-
Monitor scheduled task creation on endpoints.
-
Audit browser extension installations.
The campaign highlights a broader trend: attackers are increasingly weaponizing trusted SaaS platforms as delivery infrastructure to evade detection.
About the Research
The findings were published in CTM360’s February 2026 threat intelligence report, “Ninja Browser & Lumma Infostealer Delivered via Weaponized Google Services”
CTM360 continues to monitor this activity and track related infrastructure.
Read the full report here: https://www.ctm360.com/reports/ninja-browser-lumma-infostealer
Detect Cyber Threats 24/7 with CTM360
Monitor, analyze, and promptly mitigate risks across your external digital landscape with the CTM360.
Sponsored and written by CTM360.
