North Korean nation-state operators tracked as Contagious Interview and Famous Chollima have refined their BeaverTail and InvisibleFerret malware distribution infrastructure, deploying compiled executables via ClickFix social engineering lures since May 2025.
Unlike prior campaigns targeting software developers with JavaScript repositories, this iteration focuses on marketing and trading roles within cryptocurrency and retail organizations.
The shift evidences an operational adaptation aimed at expanding the pool of susceptible victims beyond technically proficient users.
Visiting the threat actor’s bespoke fake hiring platform hosted at businesshire. Top, served through a Vercel deployment hireprolix-iauhsmsuv-gabriels-projects-75362d20.vercel.app, targets encounter tailored application pages for cryptocurrency trader positions at four Web3 firms, plus sales and marketing roles at three blockchain organizations and a U.S. e-commerce retailer.
The platform also invites investment inquiries. Upon page load, embedded JavaScript probes browser window objects for wallet extensions including Ethereum, TronLink, TrustWallet, and Phantom and relays discoveries to the actor’s backend at nvidiasdk.fly[.]dev.
Geolocation is fetched via api.ipify.org, while visitor IPs are harvested to enforce an allowlist of fourteen addresses tied to operational safety.
When applicants attempt to record a video response under the guise of a technical interview, the site triggers a fake camera or microphone error and displays dynamic, OS-specific troubleshooting instructions.
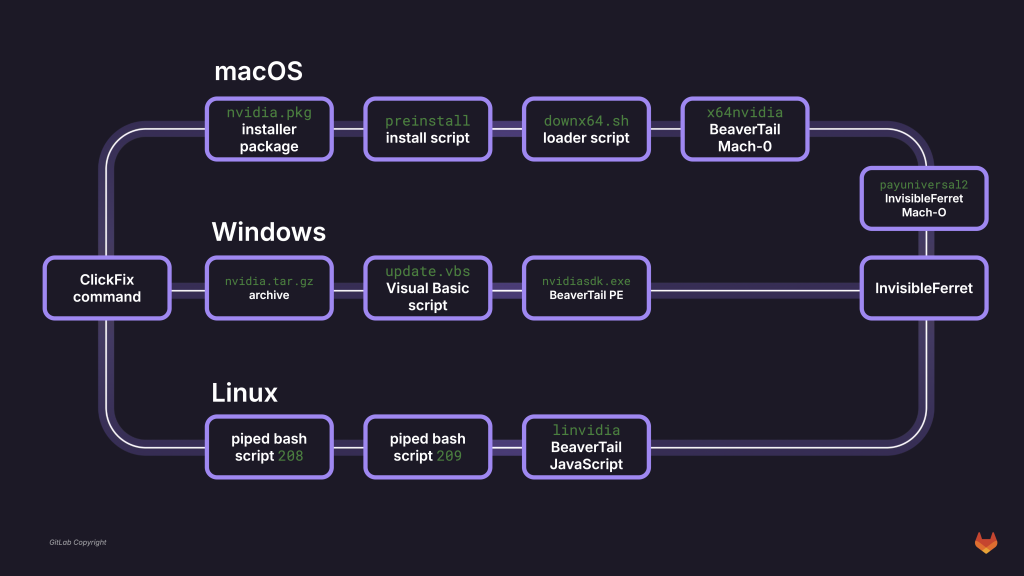
These guide users to execute a second-stage payload via system commands: on macOS, curl and sudo installer fetch a .pkg file; on Windows, curl or wget downloads a tarball then runs update.vbs; on Linux, a one-liner installs Node.js and invokes the downloaded JavaScript stealer.
Numeric user-agent headers (204 on macOS, 203 on Windows, and 209 on Linux) act as guardrails, ensuring that only genuine targets receive malicious binaries, while decoy payloads shield automated analysis.
The macOS and Windows infection chains bundle BeaverTail’s JavaScript stealer into native executables using pkg and PyInstaller, diverging from earlier QT-compiled variants.
The macOS installer com. nvidia. hpc.pkg executes a pre-install script that reads a testing-phase artifact variable (~/.myvars: MY_PASWOR) before downloading downx64.sh from the RominaMabelRamirez/dify GitHub repository.
This script retrieves two Mach-O binaries, x64nvidia (BeaverTail) and payuniversal2 (InvisibleFerret), executing payuniversal2 only if Python is absent or BeaverTail fails to drop its entry script.
The Windows archive nvidia.tar.gz includes nvidiasdk.exe (BeaverTail), a hidden 7-Zip executable for extracting Python dependencies, and update.vbs to orchestrate execution.
On Linux, the JavaScript stealer executes directly via Node, targeting only eight wallet extensions and omitting non-Chrome browser routines to reduce its size by one-third.
Both BeaverTail and InvisibleFerret contact C2 at 172.86.93.139 using “tttttt” as the campaign identifier. Static detection rates on VirusTotal remain minimal, while runtime behaviors yield consistent network callbacks and file system operations.
The campaign’s developmental artifacts, low sandbox footprints, and limited secondary payload prevalence indicate a testing phase with constrained scale.
Nonetheless, the shift to compiled malware variants and non-technical targets underscores the need for retail and crypto sector organizations to hunt for anomalous execution patterns and suspicious C2 communications.
| IOC | Type | Description |
|---|---|---|
| 05ae07783d30b37aa5f0ffff86adde57d0d497fe915537a3fc010230b54e1ee8 | SHA256 | nvidia.pkg malicious macOS installer package |
| 247fdba5fbfd076d9c530d937406aa097d6794b9af26bfc64bf6ea765ed51a50 | SHA256 | preinstall script contained in nvidia.pkg |
| 65665c3faba4fbfed12488e945306b10131afb9d3ad928accdcef75e0945a086 | SHA256 | downx64.sh macOS installer script |
| 25c9fc5c5564a74430b92cb658d43e441dee1b3c0f692dc2571ac2918efa9a52 | SHA256 | x64nvidia BeaverTail Mach-O file |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
