An aggressive malware campaign dubbed SORVEPOTEL has been detected actively targeting Windows environments by leveraging compromised WhatsApp sessions to achieve rapid, large-scale propagation.
Trend™ Research telemetry reveals that 457 of the 477 confirmed infections are clustered in Brazil, underscoring a regional focus on Brazilian enterprises and public service organizations.
Early indicators suggest that the manufacturing, technology, education, and construction sectors have also been impacted.
Initial infections begin with a convincing phishing message sent through WhatsApp or email. The message often originates from a trusted contact’s compromised account and contains a ZIP archive attachment masquerading as a benign document.
Common filenames include “RES-20250930_112057.zip,” “ORCAMENTO_114418.zip,” or “ComprovanteSantander-75319981.682657420.zip.”
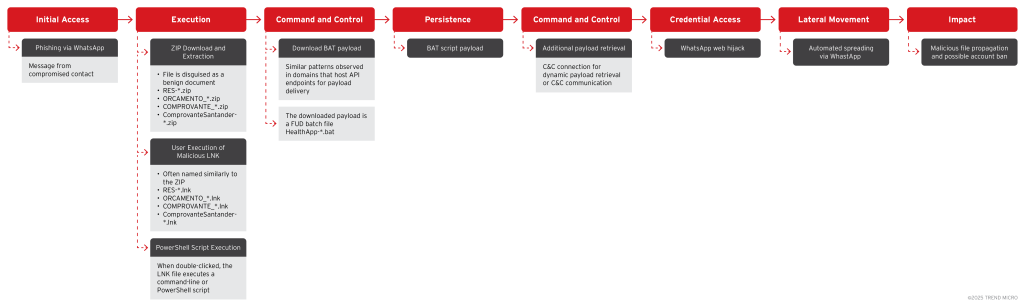
The text, written in Portuguese, instructs recipients to “baixa o zip no PC e abre” (download the ZIP on PC and open it), thereby exploiting user trust and bypassing mobile defenses.
Upon extraction, the ZIP file reveals a malicious Windows shortcut (.LNK) that, when executed, launches an obfuscated PowerShell command.
The embedded command leverages the Invoke-Expression (IEX) function with Base64-encoded parameters (-enc) and runs in hidden mode (-w hidden), effectively downloading and executing a batch (.BAT) script from attacker-controlled domains such as sorvetenopoate[.]com and expahnsiveuser[.]com.
The secondary payload is a PowerShell-based downloader that is used Net.WebClient to fetch additional modules from multiple C2 domains.
This script establishes persistence by copying itself into the Windows Startup folder and composes further PowerShell commands through iterative for loops to maintain stealth. All code execution occurs in memory, minimizing disk artifacts and evading traditional antivirus solutions.
The malware’s persistence mechanism ensures automatic re-execution on each system boot. At the same time, obfuscated domains employ typo-squatting tactics such as “sorvetenopotel” (resembling the innocuous phrase “sorvete no pote”) to blend malicious traffic with legitimate network flows.
A hallmark of SORVEPOTEL is its capability to hijack WhatsApp Web sessions. Once the malware detects an active session, it programmatically resends the same malicious ZIP file to every contact and group associated with the compromised account.
This automation results in hundreds of spam messages per minute, frequently triggering account suspensions due to WhatsApp’s anti-spam policies.
Although no evidence of data exfiltration or ransomware encryption has surfaced, the campaign’s design suggests an emphasis on maximizing distribution velocity rather than achieving deep system compromise.
Past Brazilian malware families employing similar LNK and PowerShell techniques have targeted financial credentials, suggesting potential evolution toward data theft in future SORVEPOTEL variants.
Organizations should disable automatic downloads of media and documents in WhatsApp settings to prevent inadvertent execution of malicious archives.
Enforcing application whitelisting or containerization for personal messaging apps on enterprise endpoints can block unapproved file transfers. Conducting regular user training to identify suspicious attachments and discourage downloading executables via messaging platforms remains essential.
Staying vigilant and applying layered security controls can mitigate the risk posed by self-propagating malware campaigns such as SORVEPOTEL.
SHA 256 Detection File name 2150f38c436eabebd3a93b3ace1064315153c882ce763991b6d0fb798766e0db Trojan.LNK.SORVEPOTEL.YAFJB ComprovanteSantander-18736748.908476642.lnk bd62148637152396b757c8b106d5a62982bce9df12f0a6030dda9138e44e7328 Trojan.LNK.SORVEPOTEL.YAFJB DOC-98083986_4B17B4B2.lnk 2d83c4d620866f4ae647ed6a70113686bb7b80b1a7bbdcf544fd0ffec105c4a6 Trojan.LNK.SORVEPOTEL.YAFJB 3b68826e4a1d95b1dd58b3bf1095750f31a72d8bddd1dbb35e6547ac0cf4769b Trojan.LNK.SORVEPOTEL.YAFJB 1a0af26749f5bc21732c53fc12f3a148215c8221cbeffe920411656f1ffe7500 Trojan.LNK.SORVEPOTEL.YAFJB 441a2ad553d166df3cd0ea02482f4b8370e8f9618753e1937a251a6318cb8eba Trojan.LNK.SORVEPOTEL.YAFJB ComprovanteSantander-63800793.391345519.lnk dcdde53c50aef9531c9f59f341a4e2d59796cdd94a973f2c2a464b2cafed41f5 Trojan.LNK.SORVEPOTEL.YAFJB c50b6ff360e5614d91f80a5e2d616a9d0d1a9984751bf251f065426a63dac0b5 Trojan.BAT.SORVEPOTEL.YAFJB HealthApp-0d97b7.ba
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
