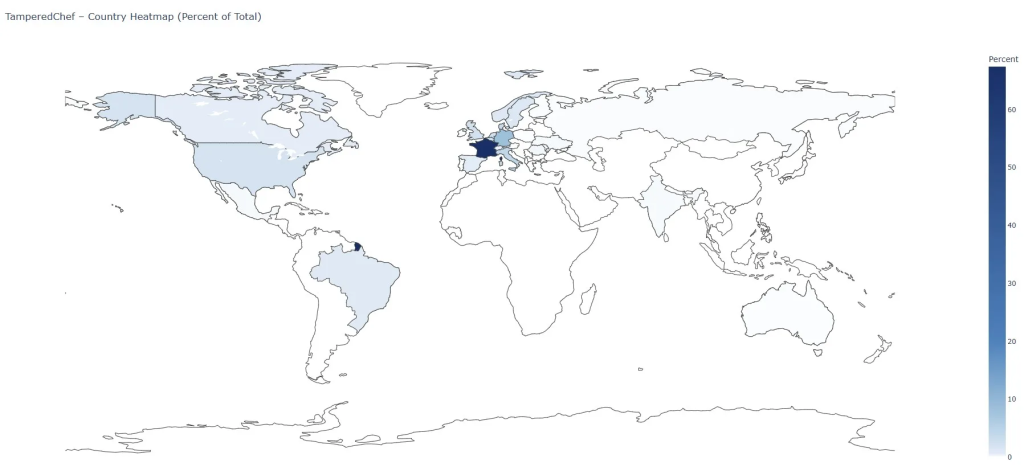
A sophisticated campaign dubbed TamperedChef leveraged an elaborate advertising push and a fully functional decoy application to compromise European organizations.
Posing as the legitimate AppSuite PDF Editor, the malware remained dormant for nearly two months, offering genuine PDF editing features to evade detection.
When the malicious payload was activated on August 21, 2025, it harvested saved browser credentials, paving the way for potential backdoor installation and underscoring the severe risks posed by well-engineered supply chain attacks.
The infection chain began with search-engine advertisements promising a free PDF editor. Users who clicked the ads were redirected to attacker-controlled domains hosting a malicious Microsoft Installer (MSI) package.
This installer displayed a standard End User License Agreement dialog, complete with localized French text in some variants, to establish trust and bypass automated sandbox detonations that lack user interaction.
Upon accepting the EULA, the MSI retrieved the actual Electron-based AppSuite PDF Editor installer from vault.appsuites.ai over an unencrypted HTTP connection.
Installation occurred silently under the user’s profile directory and established persistence by creating an autorun registry entry, enabling execution at each logon without requiring administrative privileges.
This approach allowed the malware to blend into corporate environments with strict privilege controls while maintaining resilience against simple removal attempts.
Once installed, PDF Editor.exe launched as a Chromium-based browser shell, loading its interface and core PDF functionality remotely from pdf-tool.appsuites.ai.
The local application comprised two critical components: a heavily obfuscated JavaScript file, pdfeditor.js, and a native NodeJS module, Utilityaddon.node.
The JavaScript stub handled benign editing tasks by asynchronously fetching UI elements and processing user inputs, while simultaneously embedding malicious routines that scanned browser profile folders for credentials stored in Chrome, Firefox, and Edge.
The native module provided low-level registry manipulation and scheduled task capabilities, enabling the malware to adjust persistence or execute additional payloads at predetermined intervals.
By separating the editing interface from the stealthy credential-stealing code, the attackers minimized immediate detection and extended the window before defensive signatures could be deployed.
Upon activation of credential theft on August 21, incident responders identified anomalous network traffic consistent with browser profile exfiltration.
Threat actors swiftly issued “clean” application updates (versions 1.0.40 and 1.0.41) that removed code obfuscation and overt malicious logic but still maintained connections to attacker-controlled infrastructure for telemetry and potential future commands.
Concurrently, telemetry revealed a parallel decoy application, AppSuite Print, built and signed on May 20, 2025, with identical certificate metadata. However, this variant saw no deployment in the wild and appears abandoned.
Leveraging artifacts and code reuse from the PDF Editor campaign, attackers are now testing an early-stage successor named S3-Forge, which retains the familiar Electron UI but connects to freeonlinetools.info.
Unsigned and packaged via Squirrel and NuGet, S3-Forge indicates a shift toward new distribution tactics and continued refinement of decoy applications. Initial samples surfaced on VirusTotal on August 26, 2025, demonstrating the adversary’s agility in evolving their arsenal.
Organizations should forbid installations from untrusted ads, enforce strict application whitelisting, and require code-signing validation.
Immediately rotate compromised browser credentials, invalidate sessions, and disable or limit browser-based password storage. Deploy behavioral monitoring for obfuscated JavaScript in Electron applications and regularly audit autorun entries to detect persistent threats early.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
