Chaos ransomware has undergone a significant transformation in 2025, marking its first departure from .NET programming with the introduction of Chaos-C++, a sophisticated variant that combines destructive tactics with cryptocurrency theft capabilities.
This evolution represents a concerning shift toward more aggressive extortion methods that amplify both operational impact and financial risk for victims.
The latest variant masquerades as “System Optimizer v2.1,” a fake utility that displays bogus optimization messages while silently deploying its ransomware payload.
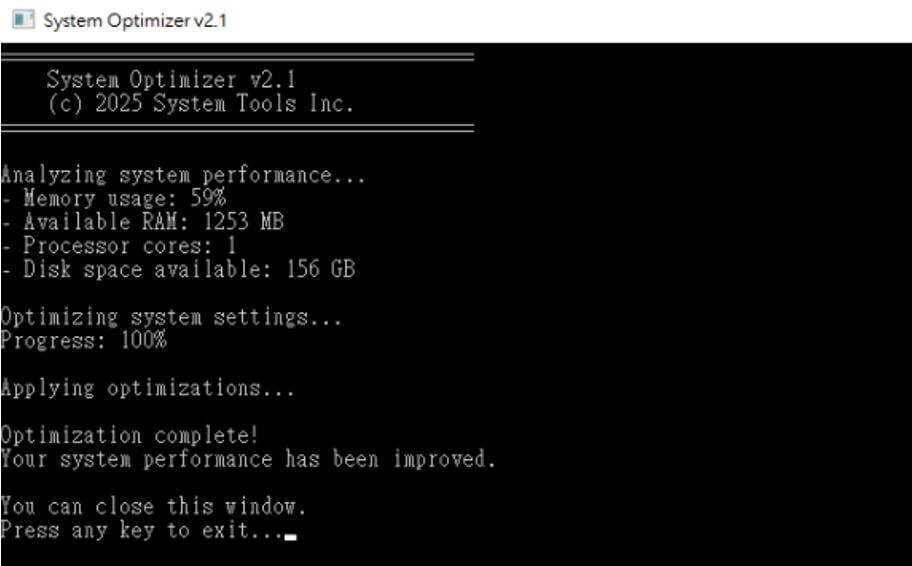
The downloader (SHA256: 2fb01284cb8496ce32e57d921070acd54c64cab5bb3e37fa5750ece54f88b2a4) creates a hidden log file at %TMP%sysopt.log and writes the payload to %TMP%svc[XXXX].tmp, using randomly generated characters, prioritizing stealth execution through the use of CREATE_NO_WINDOW flags.
Chaos-C++ implements a sophisticated size-based file handling strategy that prioritizes speed and destruction over traditional encryption approaches.
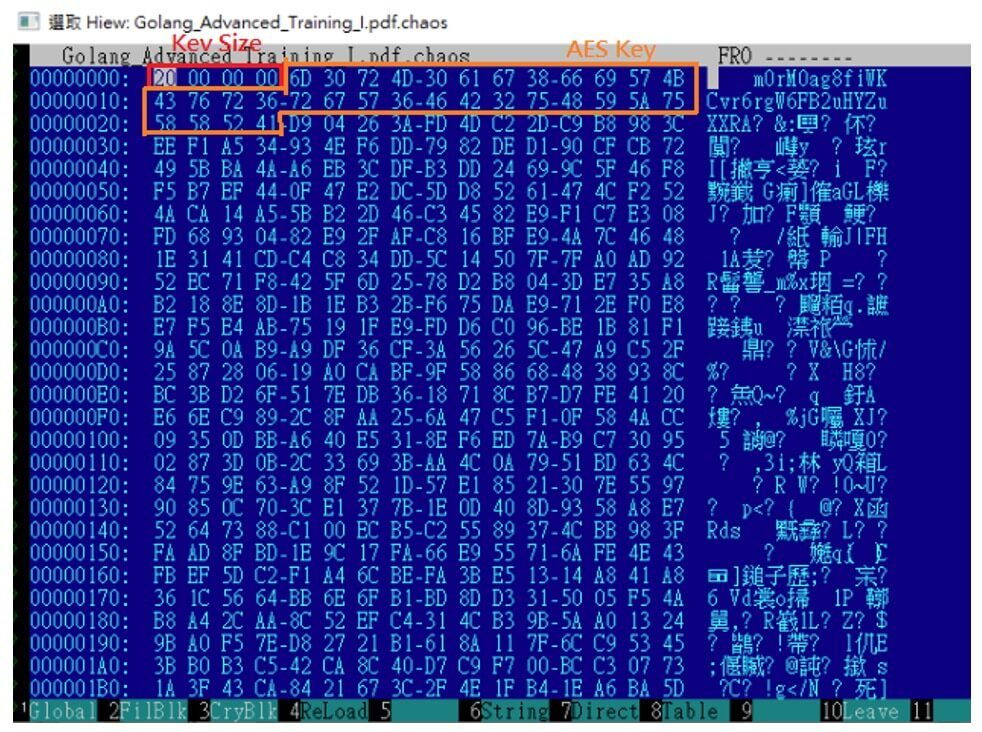
Files under 50MB undergo full AES-256-CFB encryption using Windows CryptoAPI functions, with an XOR-based fallback encryption mechanism in place when the crypto functions are unavailable.
The ransomware targets over 40 file extensions while avoiding critical system directories to maintain operational stability.
The variant’s most concerning feature involves its treatment of larger files. Files between 50MB and 1.3GB are deliberately skipped and left untouched, while files exceeding 1.3GB have their content completely deleted rather than encrypted.
This destructive approach eliminates recovery possibilities for critical data, such as archives, databases, and backups, rendering it more akin to a wiper than traditional ransomware.
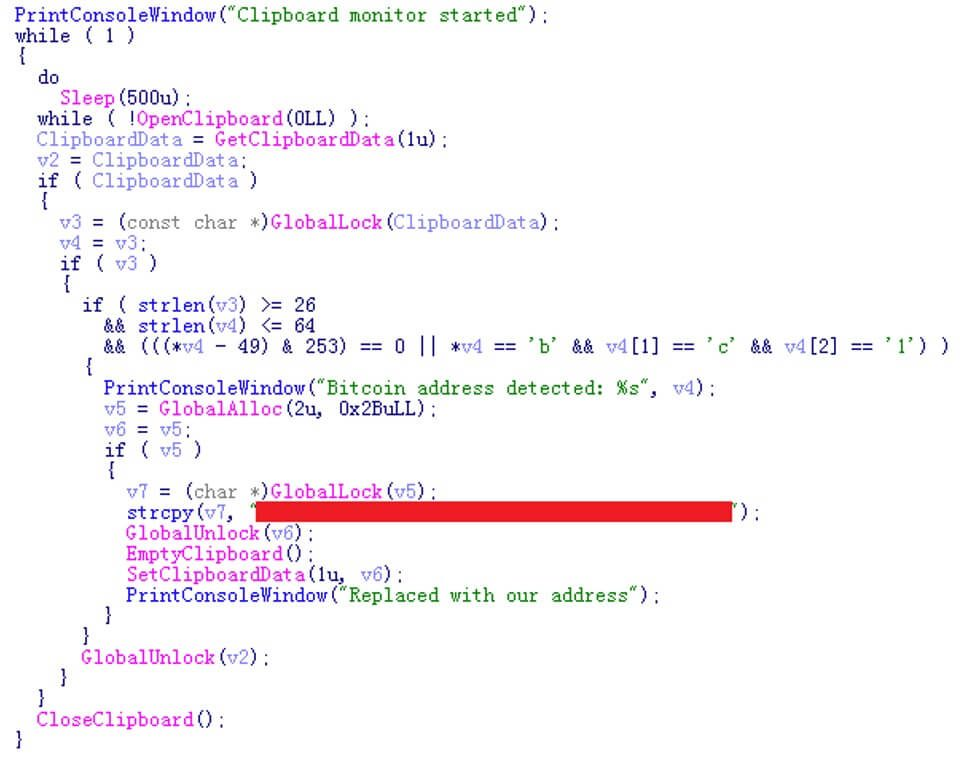
Beyond encryption, Chaos-C++ introduces clipboard hijacking capabilities that automatically intercept and replace Bitcoin addresses copied to the system clipboard.
The malware validates addresses by checking their length (26-64 characters) and recognizing legitimate formats including P2PKH (prefix “1”), P2SH (prefix “3”), and Bech32 (prefix “bc1”) wallets.
When valid cryptocurrency addresses are detected, the ransomware replaces them with an attacker-controlled Bech32 Bitcoin wallet using Windows Clipboard API functions.
This dual-threat approach ensures victims unknowingly redirect payments to attackers even when attempting legitimate cryptocurrency transactions.
The ransomware maintains persistence through the SvcHost_Mutex_7z459ajrk mutex and creates %APPDATA%READ_IT.txt to prevent reinfection. Upon completion, it displays an “Encryption complete” message and deploys ransom notes, while continuing to monitor the clipboard.
Security researchers note that Chaos-C++’s evolution from previous .NET variants demonstrates the threat actors’ experimentation with balancing execution speed against damage scope, suggesting future variants may adopt increasingly wiper-like characteristics that prioritize destruction over recovery incentives.
| SHA256 | Note |
| 2fb01284cb8496ce32e57d921070acd54c64cab5bb3e37fa5750ece54f88b2a4 | Chaos Downloader |
| 19f5999948a4dcc9b5956e797d1194f9498b214479d2a6da8cb8d5a1c0ce3267 | Chaos ransomware |
| f200ea7ccc5c9b0eaada74046551ed18a3a9d11c9e87999b25e6b8ee55857359 | Chaos ransomware |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
