Astaroth, a notorious banking trojan, has reemerged in a campaign that abuses trusted cloud platforms to maintain resilience against takedown efforts.
The infection process begins with highly targeted phishing emails, often themed around business, document signing, or job applications, which trick recipients into downloading a ZIP file.
This archive contains an obfuscated Windows Shortcut (LNK) file. When executed, the LNK triggers JavaScript via mshta.exe, enabling the download of additional obfuscated scripts aimed at circumventing analysis and detection through geographical restrictions.
These scripts then fetch a bundle of files, including an AutoIT-compiled script, interpreter, encrypted payload, and configuration files.
The use of memory injection through shellcode, executed inside the AutoIT process, allows the trojan to deploy its Delphi-based DLL payload without leaving evident disk traces.
Astaroth is specifically engineered to recognize anti-analysis environments and will terminate itself if security tools, virtual machines, or specific language or locale settings are detected.
Once embedded, Astaroth transforms into an invisible pickpocket, actively surveilling the victim’s system for banking and cryptocurrency activities.
The malware constantly checks for browsers and applications with window class names linked to popular web browsers, such as Chrome, Mozilla, and Internet Explorer.
It focuses on a wide range of South American financial institutions, including Caixa, Safra, and Itau, as well as numerous cryptocurrency platforms, such as Binance and Metamask.
If a user accesses a banking or crypto website, Astaroth hooks the system’s keyboard events to capture login credentials and other sensitive information. This targeted surveillance underscores the growing convergence between traditional banking threats and attacks on crypto assets.
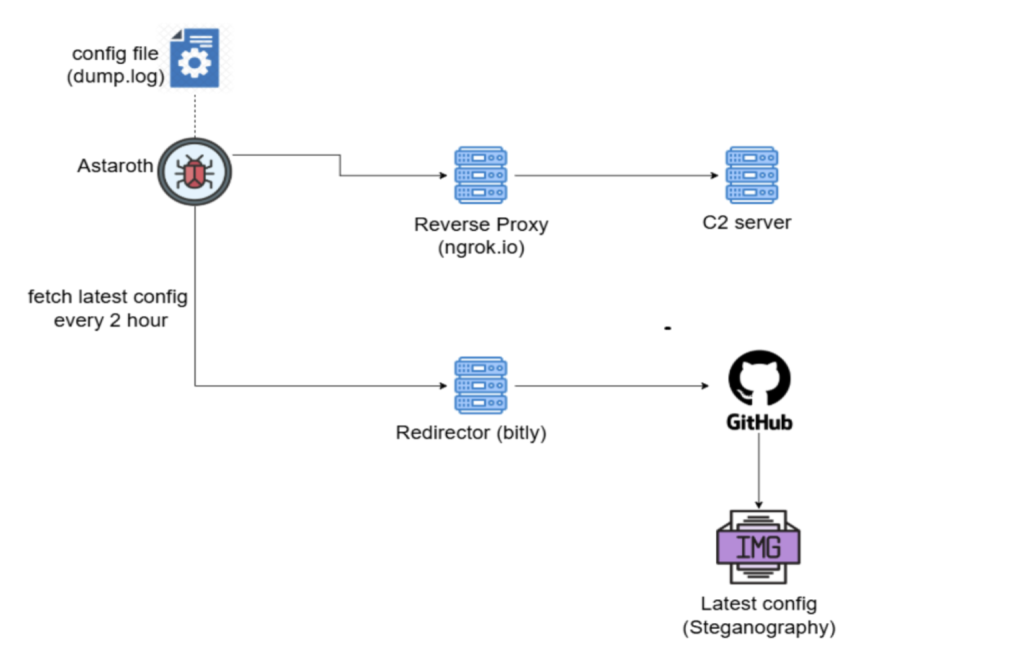
Credentials are exfiltrated using a custom binary protocol sent via Ngrok-powered reverse proxy tunnels, which further masks activity from defenders and complicates efforts to block malicious communications at the network layer.
Astaroth’s campaign is distinguished by its innovative abuse of GitHub, used as a resilient channel for malware configuration updates.
When conventional command-and-control servers are disrupted by law enforcement or security researchers, Astaroth pivots to GitHub repositories that host config files cleverly embedded in PNG images via steganography.
Every few hours, the malware fetches new images from these repositories, extracting updated configuration settings hidden in pixel data.
This strategy enables attackers to maintain control of infected hosts regardless of interruptions to their primary infrastructure, leveraging GitHub’s global reach and legitimacy to avoid immediate detection or removal.
Numerous malicious repositories linked to the campaign were identified, reported, and subsequently taken down through coordinated action between McAfee and GitHub. However, the threat highlights the increasing sophistication of adversary tactics.
The persistent mechanism, involving a dropped LNK in the Windows startup folder, ensures that Astaroth launches with each reboot, reinforcing its foothold on compromised systems.
In conclusion, the Astaroth campaign reveals critical trends in malware adaptation: the fusion of cloud infrastructure abuse, advanced anti-analysis techniques, and live credential harvesting targeting both banking and cryptocurrency platforms.
Organizations and individuals in high-risk geographies, especially in Brazil, where the latest attacks concentrate, must employ robust email security, multi-factor authentication, and continuous endpoint monitoring to stay resilient against these evolving threats.
| IOC | Hash / URL |
| 7418ffa31f8a51a04274fc8f610fa4d5aa5758746617020ee57493546ae35b70 7609973939b46fe13266eacd1f06b533f8991337d6334c15ab78e28fa3b320be 11f0d7e18f9a2913d2480b6a6955ebc92e40434ad11bed62d1ff81ddd3dda945 |
|
| ZIP URL | https://91.220.167.72.host.secureserver[.]net/peHg4yDUYgzNeAvm5.zip |
| LNK | 34207fbffcb38ed51cd469d082c0c518b696bac4eb61e5b191a141b5459669df |
| JS Downloader | 28515ea1ed7befb39f428f046ba034d92d44a075cc7a6f252d6faf681bdba39c |
| Download server | clafenval.medicarium[.]help sprudiz.medicinatramp[.]click frecil.medicinatramp[.]beauty stroal.medicoassocidos[.]beauty strosonvaz.medicoassocidos[.]help gluminal188.trovaodoceara[.]sbs scrivinlinfer.medicinatramp[.]icu trisinsil.medicesterium[.]help brusar.trovaodoceara[.]autos gramgunvel.medicoassocidos[.]beauty blojannindor0.trovaodoceara[.]motorcycles |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
