Sekoia.io’s Threat Detection and Research (TDR) team has published a technical deep dive on the PolarEdge Backdoor, a newly identified IoT malware implant observed targeting QNAP NAS devices through exploitation of CVE-2023-20118, a remote code execution flaw in Cisco routers.
The discovery follows the team’s earlier identification of the PolarEdge botnet in January 2025, which abused IoT infrastructure belonging to Asus, QNAP, and Synology routers.
Detected by honeypots on February 10, 2025, the campaign delivered a shell script (“q”) via FTP that fetched and executed the PolarEdge implant.
The 1.6 MB ELF binary, although not obfuscated, employs multiple anti-analysis measures and a combination of cryptographic algorithms to conceal its configuration and internal workings.
At its core, PolarEdge implements an embedded TLS server using the mbedTLS 2.8.0 library, which is unusual among IoT malware that typically connects outbound to command servers.
This local TLS listener enables inbound, authenticated control using a custom binary protocol. The malware verifies a sequence of embedded tokens within each request and executes commands received over encrypted sessions.
The absence of authentication mechanisms beyond static “magic tokens” means that any party in possession of these values could potentially hijack infected devices.
The backdoor’s configuration resides in the last 512 bytes of the ELF binary, XOR-encrypted with key 0x11 and split into three segments: a filter file identifier (“GLyzaagK”), server parameters including listening port 49254, and the C2 server list.
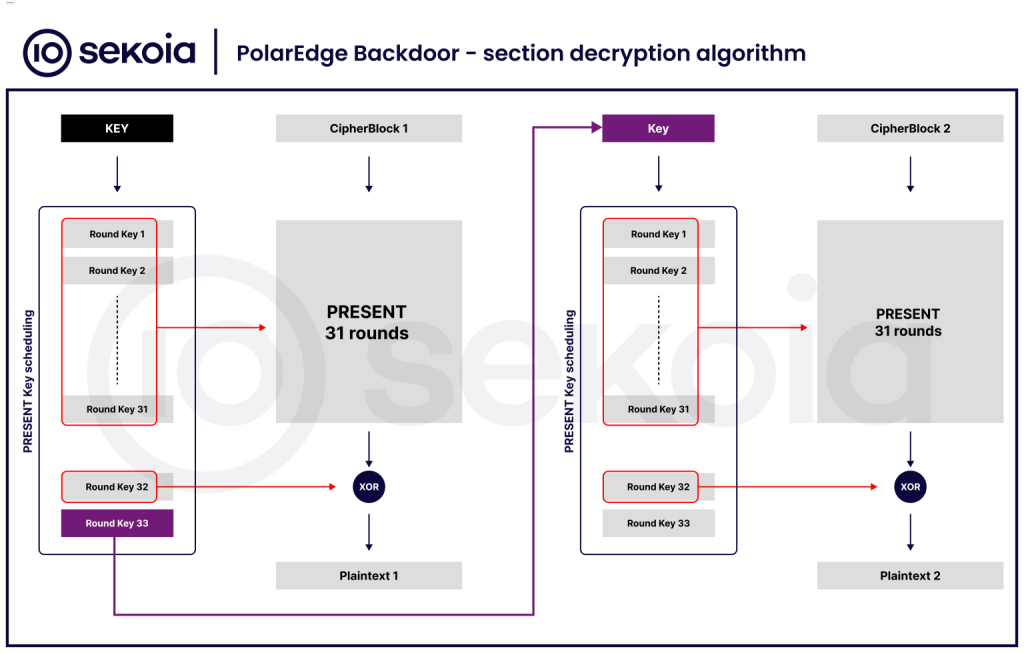
During execution, the implant decrypts embedded sections (.init_rodata and .init_text) using the PRESENT block cipher, a lightweight 64-bit encryption algorithm, revealing certificates, routine code, and hardcoded command handlers.
Notably, PolarEdge chains successive PRESENT keys for multi-block decryption, a rare choice in modern malware design.
To evade detection, the implant disguises itself using system-like process names such as “igmpproxy” or “httpd” and overlays its own /proc/<pid> directory with /proc/1, effectively concealing runtime attributes.
It lacks persistence across reboots but employs a fork-based watchdog that relaunches the binary every 30 seconds if the parent process terminates.
PolarEdge supports two auxiliary modes. Connect-back mode allows TLS-based download of files from remote servers, while debug mode permits dynamic reconfiguration of C2 destinations by decrypting base64-encoded parameters.
Daily fingerprinting routines send identifiers such as device IP, MAC address, process ID, and firmware tag (“QNAP_2”) to its C2 via encrypted HTTP GET requests, with potential for on-demand payload delivery through /tmp/.qnax.sh.
The analysis positions PolarEdge as a sophisticated IoT-oriented malware adopting mature encryption and stealth mechanisms typically reserved for desktop APT toolkits, signaling a growing convergence between network appliance exploitation and advanced modular implant design.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
