
A new malware-as-a-service (MaaS) platform named Atroposia provides cybercriminals a remote access trojan that combines capabilities for persistent access, evasion, data theft, and local vulnerability scanning.
The malware is available for a $200 monthly subscription that unlocks advanced features such as hidden remote desktop, file system control, data exfiltration, clipboard theft, credential theft, cryptocurrency wallet theft, and DNS hijacking.
Atroposia was discovered by researchers at data security company Varonis, who warned that it’s the latest example of an easy-to-use, affordable “plug and play” toolkit, alongside SpamGPT and MatrixPDF.
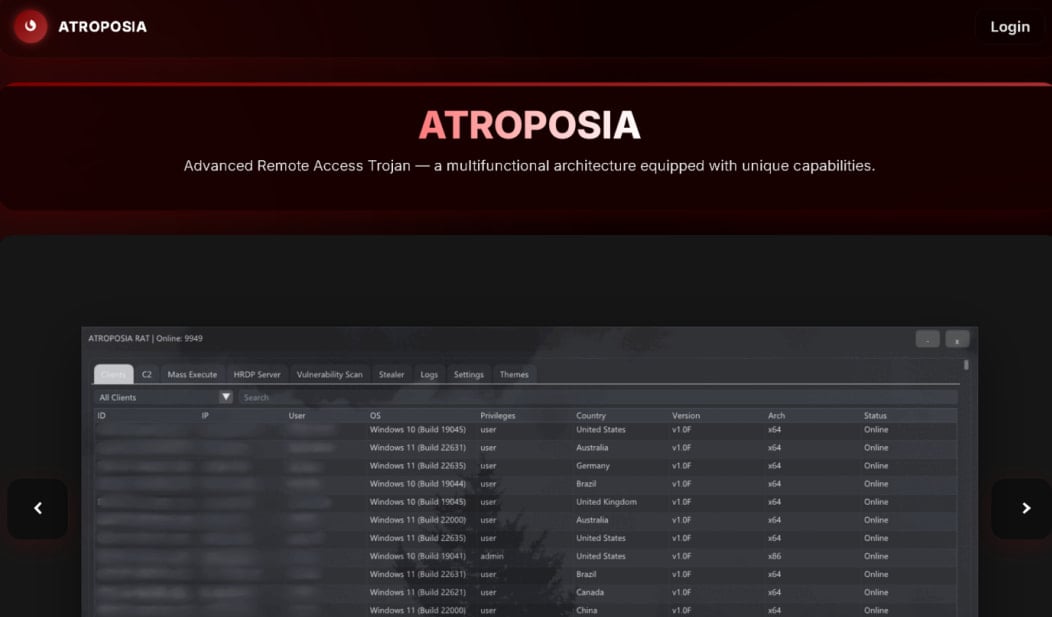
Source: Varonis
Atroposia is a modular RAT that communicates with its command-and-control (C2) infrastructure over encrypted channels and can bypass the User Account Control (UAC) protection to increase privileges privilege on Windows systems.
According to the researchers, it can maintain persistent, stealthy access on infected hosts, and its main capabilities include:
- HRDP Connect module that spawns a covert desktop session in the background, allowing an attacker to open apps, view documents and email, and interact with the user’s session without any visible indication. Varonis says standard remote-access monitoring can fail to detect it.
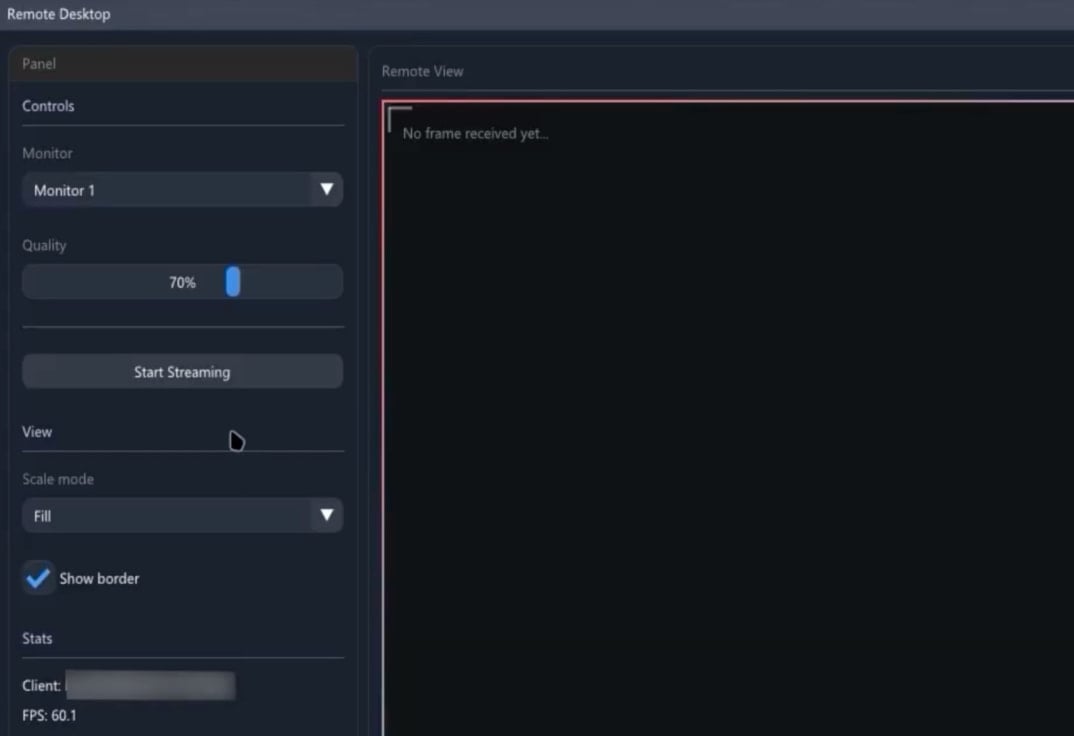
Remote desktop module
Source: Varonis - Explorer-style file manager that allows remote file browsing copying, deleting, and execution capabilities. A grabber component looks for specific files, filtering them based on extension or a keyword, compresses the data into password-protected ZIP archives, and exfiltrates it using in-memory techniques to minimize traces.
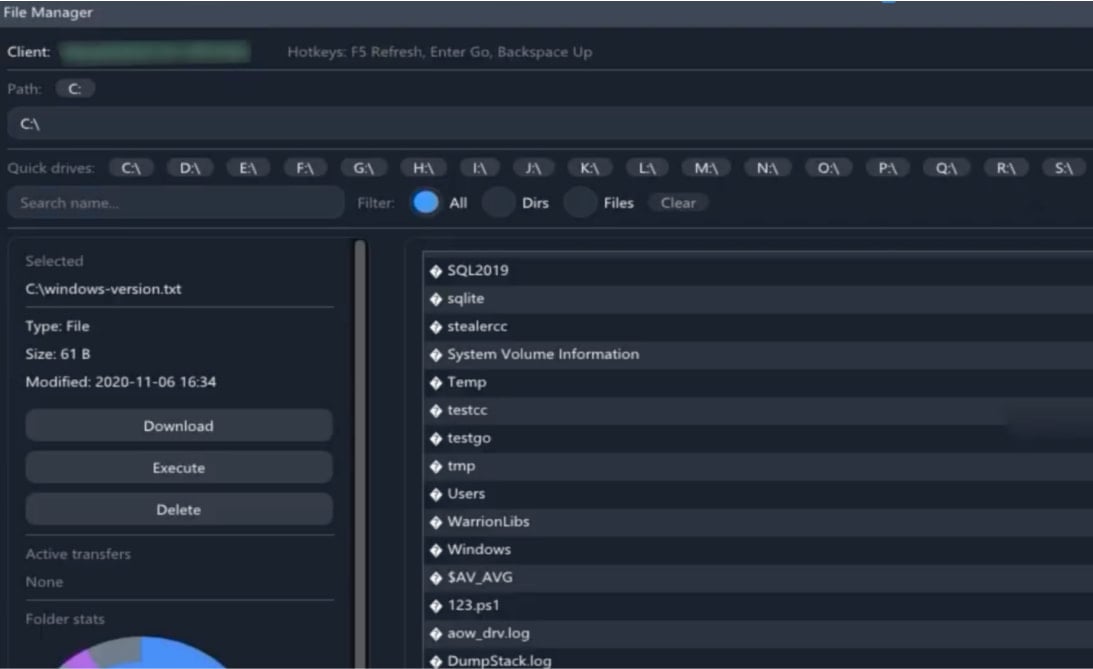
The file management module
Source: Varonis - Stealer module targets saved logins, crypto wallets, and chat files, while a clipboard manager captures everything copied in real time (passwords, API keys, wallet addresses) and presents a history to the attacker.
- Host-level DNS hijack module that maps domains to attacker IPs so the victim is silently routed to rogue servers, enabling phishing, MITM, fake updates, ad or malware injection, and DNS-based exfiltration.
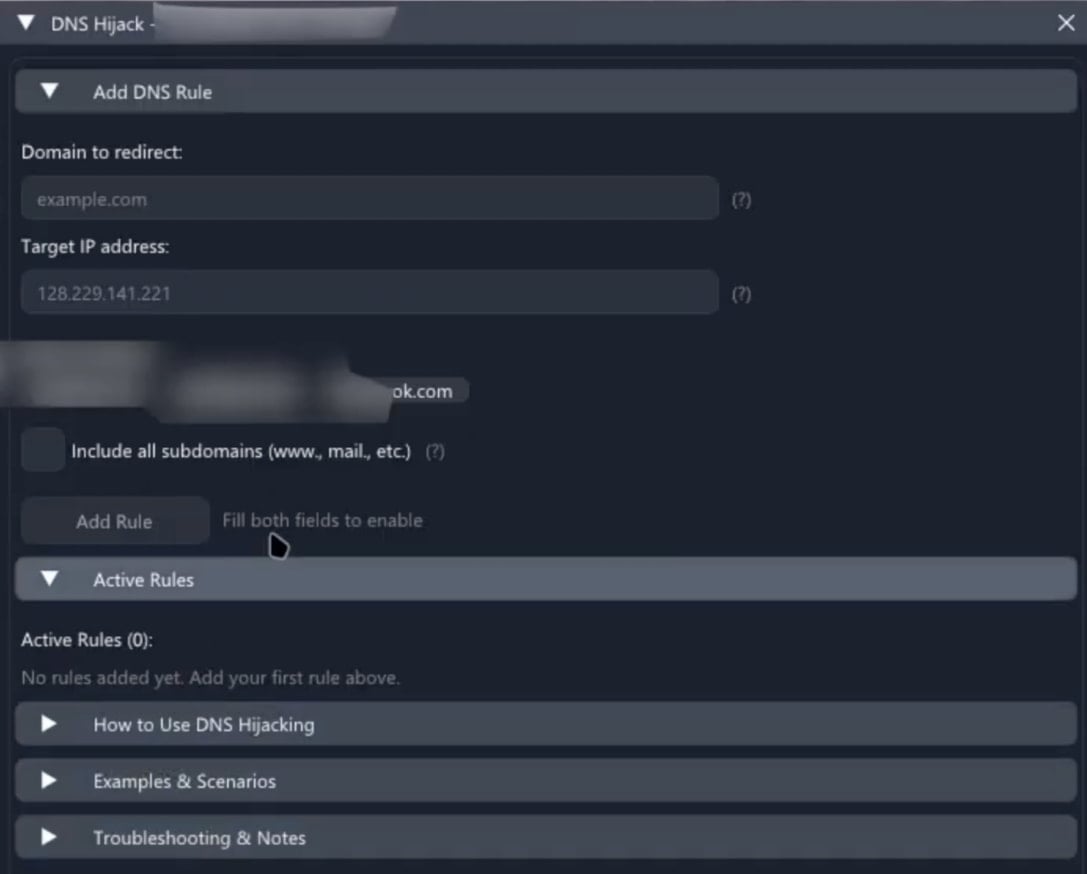
DNS hijacking module
Source: Varonis - Built-in local vulnerability scanner that audits missing patches, unsafe settings, and vulnerable software, returning a score that allows attackers to prioritize exploits, demonstrating the RAT’s modular, plugin-based workflow.
The researchers say that the vulnerability check “is dangerous in corporate environments because the malware might find an outdated VPN client or an unpatched privilege escalation bug.” This can be easily used to gain deeper access.
Varonis’ researchers say the module checks for missing patches, insecure settings, and outdated software versions. The function may also be used to find nearby systems that can be exploited.
The emergence of Atroposia adds yet another MaaS option for cybercriminals, lowering the technical barrier and enabling low-skilled threat actors to execute effective campaigns.
To mitigate the risk, users are advised to download software only from official sites and reputable sources, avoid pirated software and torrents, skip promoted search results, and never execute commands they find online that they don’t understand.
46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.

