Published On : 2025-10-31

Ransomware of the week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows, Network Shares, Removable Storage, Tor-based Communication, Cloud/Exfiltration Tools.
Target Geographies: Global (English-speaking focus: United States, Western Europe, Australia), Opportunistic regions (Asia, Eastern Europe, Latin America).
Target Industries: Aerospace & Defense, Government contractors, Technology/Engineering firms.
Introduction:
CYFIRMA Research and Advisory Team has found KYBER Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
KYBER Ransomware:
Researchers have discovered a new ransomware strain called KYBER. This ransomware encrypts victims’ files, renaming them and appending a random extension to filenames (e.g., .#~~~”), and creates a ransom note (“ReadMeForDecrypt.txt”)

Screenshot of files encrypted by the ransomware (Source: Surface Web)
The Kyber Ransomware note informs victims that their files have been encrypted using the AES-256-CTR algorithm, with encryption keys generated through X25519 and Kyber1024, making decryption without their help practically impossible. The attackers claim to have exfiltrated a large amount of sensitive data from the victim’s network, warning that if communication is not established within one to two weeks, the organization’s name and samples of stolen data will be publicly posted on their leak blog. To prove their ability to decrypt files, they offer free decryption for three small files and provide examples of the stolen data upon request. The note attempts to build trust by emphasizing their “professionalism” and the confidentiality of negotiations, while discouraging victims from contacting law enforcement, as it would allegedly prevent payment and not stop data publication. They also warn against tampering with encrypted files, claiming it could make recovery impossible. Finally, the attackers instruct victims to download the Tor Browser and access a unique anonymous chat link to initiate communication and negotiate ransom payment.
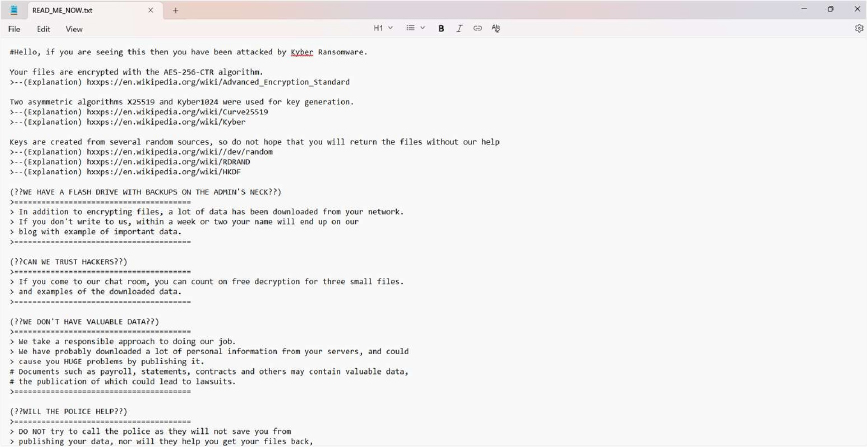
Screenshot: The appearance of KYBER ‘s ransom note (“READ_ME_NOW.txt”) (Source: Surface Web)
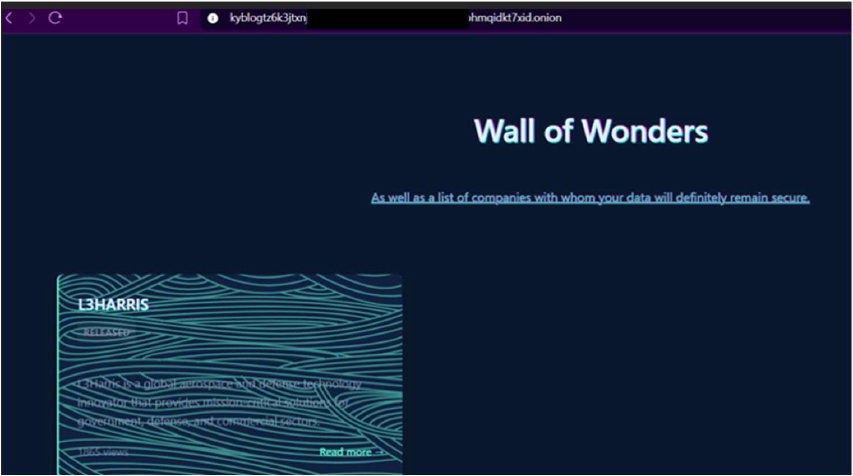
Screenshot: Kyber’s data leak site
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1543 | Create or Modify System Process |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1543 | Create or Modify System Process |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562 | Impair Defenses |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1552 | Unsecured Credentials |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518 | Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
- The ransomware primarily targets Windows OS, which is utilised by enterprises in a variety of industries.
- Calls to WMI: The ransomware is making calls to the Windows Management Instrumentation (WMI) framework. WMI is a powerful tool used by many legitimate applications and services, but it can also be exploited by malware to execute commands, collect information, or perform system modifications.
- Long-sleeps: Ransomware utilizes extended sleep intervals to evade detection by security software, enabling it to operate stealthily and increasing the likelihood of completing file encryption before being identified.
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot software. This technique is used by the ransomware to determine whether it is operating in a debug environment. This feature aids the ransomware in avoiding analysis and detection attempts.
- Persistence: The ransomware exhibits persistence mechanisms to ensure its survival and ongoing malicious activities within the compromised environment. This could involve creating autostart entries or modifying system settings to maintain a foothold and facilitate future attacks.
ETLM Assessment:
CYFIRMA’s assessment indicates that the KYBER ransomware group is rapidly evolving from a conventional encryptor into a structured, data-driven extortion operation, reflecting increasing technical sophistication and operational maturity. Evidence from the ransom note and observed artifacts—such as the use of hybrid encryption (AES-256-CTR with X25519 and Kyber1024), explicit claims of mass data exfiltration, offers of limited free decryption to build trust, Tor-based anonymous communication channels, and threats of public data leaks—demonstrates a professionalized approach consistent with emerging high-tier ransomware collectives. These behaviors, combined with coercive communication tactics, leak- based intimidation, and emphasis on negotiation secrecy, strongly indicate a deliberate evolution in tactics, techniques, and procedures (TTPs). With these capabilities already active, it is highly likely that KYBER will advance toward double- or triple-extortion models, deploy dedicated leak sites or data auction platforms, and eventually transition into a Ransomware-as-a-Service (RaaS) ecosystem— positioning it as a scalable, persistent, and globally impactful ransomware threat.
Sigma rule:
title: WannaCry Ransomware Activity tags:
– attack.lateral-movement
– attack.t1210
– attack.discovery
– attack.t1083
– attack.defense-evasion
– attack.t1222.001
– attack.impact
– attack.t1486
– attack.t1490
– detection.emerging-threats logsource:
category: process_creation product: windows
detection: selection_img:
– Image|endswith:
– ‘tasksche.exe’
– ‘mssecsvc.exe’
– ‘taskdl.exe’
– ‘taskhsvc.exe’
– ‘taskse.exe’
– ‘111.exe’
– ‘lhdfrgui.exe’
# – ‘diskpart.exe’ # cannot be used in a rule of level critical
– ‘linuxnew.exe’
– ‘wannacry.exe’
– Image|contains: ‘WanaDecryptor’
selection_cmd:
CommandLine|contains: ‘@[email protected]’ condition: 1 of selection_*
fields:
– CommandLine
– ParentCommandLine falsepositives:
– Unknown level: critical
Source: Surface Web
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local environments.
- Ensure that backups of critical systems are maintained, which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATIONS
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATIONS
- Update all applications/software regularly with the latest versions and security patches alike.
- Add the Sigma rule for threat detection and monitoring, which will help to detect anomalies in log events, identify and monitor suspicious activities.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
Trending Malware of the Week
Type: Backdoor | Objectives: Account takeover, Data theft | Target Technology: Android OS | Target Geography: Brazil, Indonesia
CYFIRMA collects data from various forums, based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “Baohuo” is trending.
Overview of the Baohuo Malware
Researchers have uncovered Baohuo, a malicious backdoor hidden inside altered versions of the Telegram X messenger. Unlike typical data-stealing malware, Baohuo grants cybercriminals near-total control over victims’ Telegram accounts—allowing them to read messages, manage chats, and even manipulate channel memberships without the user’s knowledge. Its ability to hide unauthorized logins and disguise suspicious activity within Telegram sessions makes it particularly deceptive. Interestingly, the attackers employ an unconventional command system through the Redis database, a rare tactic in Android- based threats.
The backdoor’s spread began around mid-2024, primarily through fake advertisements within mobile apps that lure users into downloading counterfeit versions of Telegram X. These ads redirect users to fraudulent websites resembling app stores, often themed around social interaction or dating to increase credibility. Currently, the campaign is focused on Portuguese- and Indonesian-language banners — indicating Brazil and Indonesia as primary targets. However, with over 58,000 infections already detected, the operation’s infrastructure suggests a potential for global expansion.
In addition to malicious websites, Baohuo has been found in several third-party app stores, such as APKPure and ApkSum, sometimes falsely listed under the official Telegram developer’s name. This shows how cybercriminals are exploiting trusted platforms to broaden their reach. With thousands of compromised devices—including smartphones, tablets, smart TVs, and even Android-powered cars—Baohuo stands out as a sophisticated and large-scale campaign blending social engineering with advanced account manipulation.
Attack Method
Baohuo operates through multiple modified versions of the Telegram X messenger, each designed to execute the same malicious goal under different layers of disguise. In some cases, the backdoor is built directly into the app’s main structure, while in others, it is introduced as a dynamic patch or stored separately within the app’s resources to be activated during runtime. This modular approach ensures that, despite the infection, the messenger continues to function normally, keeping victims unaware that their communications and accounts are under the complete control of attackers.
Once installed, Baohuo activates as soon as the messenger launches, allowing the operators to manipulate app behavior without disrupting the user experience. To maintain stealth, it employs mirrored functions that imitate Telegram X’s legitimate processes, creating deceptive pop-ups and phishing messages identical to authentic ones. For deeper manipulations—such as concealing certain chats or hiding connected devices—the malware leverages dynamic modification tools, enabling it to alter the app’s behavior and extract sensitive data, including clipboard contents, without user detection.
A defining aspect of Baohuo’s attack method is its dual communication system. Earlier versions relied solely on conventional command servers, but newer builds also integrate a Redis database for receiving updates and commands—a method rarely observed in Android malware. This setup allows cybercriminals to remotely manage infected devices, issue instructions, and modify configurations even if one control channel goes offline.
Through these connections, Baohuo can carry out extensive operations, such as stealing messages and contacts, collecting account tokens, joining or leaving channels, displaying fake update prompts, and uploading sensitive clipboard data. These capabilities enable attackers to silently maintain long-term control, turning an ordinary messaging app into a powerful espionage and manipulation tool.
Following are the TTPs based on the MITRE Attack Framework for Mobile
| Tactic | Technique ID | Technique Name |
| Initial Access | T1660 | Phishing |
| Defense Evasion | T1628.002 | Hide Artifacts: User Evasion |
| Defense Evasion | T1655 | Masquerading |
| Defense Evasion | T1406 | Obfuscated Files or Information |
| Credential Access | T1414 | Clipboard Data |
| Discovery | T1418 | Software Discovery |
| Discovery | T1421 | System Network Connections Discovery |
| Discovery | T1422 | System Network Configuration Discovery |
| Discovery | T1424 | Process Discovery |
| Discovery | T1426 | System Information Discovery |
| Discovery | T1430 | Location Tracking |
| Collection | T1409 | Stored Application Data |
| Collection | T1414 | Clipboard Data |
| Collection | T1429 | Audio Capture |
| Collection | T1430 | Location Tracking |
| Collection | T1636.003 | Protected User Data: Contact List |
| Collection | T1636.004 | Protected User Data: SMS Messages |
| Command and Control | T1437 | Application Layer Protocol |
INSIGHTS
- Baohuo represents a shift in how cybercriminals exploit trust within popular digital ecosystems. Instead of merely stealing data, the attackers use control over Telegram accounts to manipulate engagement—boosting subscribers, spreading messages, and quietly shaping online interactions. This reflects a broader move from simple theft to social manipulation, where compromised accounts become tools for influence and profit rather than just data sources.
- The psychological and personal effects of Baohuo are particularly concerning. Because it hides within an everyday messaging app, victims rarely suspect anything unusual. Their accounts remain active, conversations appear normal, and yet, behind the scenes, their identities are being used to interact, share content, or even mislead others. This creates a sense of false security, making it one of those threats that erodes trust slowly—where users discover the compromise only after their digital reputation or private information has already been exploited.
- At a broader level, Baohuo exposes the fragility of app distribution networks and the thin line between legitimate and malicious platforms. Its spread through third- party app stores and advertising channels demonstrates how easily a trusted brand can be cloned and repackaged to deceive users. As digital platforms continue to expand into new markets and device types, the Baohuo case stands as a reminder of how misuse of familiar technology can quietly undermine confidence in the very systems people rely on for communication and connection.
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Baohuo’s techniques could pave the way for more advanced threats that exploit popular communication platforms used by both individuals and organizations. As attackers refine their ability to embed backdoors into legitimate-looking apps, everyday users may unknowingly grant access to their private conversations, financial data, and digital identities. This could lead to a rise in large-scale account takeovers, impersonation scams, and privacy breaches that ripple across social and professional spaces alike. Over time, such tactics may redefine how trust is perceived in online interactions, creating an environment where even familiar apps and contacts can no longer be assumed safe.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule Baohuo_URLs_IPs_and_Hashes
meta:
description = “Detects IoCs (file hashes, URLs, IPs) associated with Baohuo” author = “CYFIRMA”
malware = “Baohuo”
strings:
// SHA1 file hashes
$sha1_1 = “4410f69099a037a25e5976df04a91cee7dbfac14”
$sha1_2 = “6699466094cc74e31fae4a959004d70fc5d10e94”
$sha1_3 = “4673bd285e1f6c6e628fd5aa8d7d9a2293310bf5”
$sha1_4 = “fc4b545cce8933b32d82ab792f0f6c12099f1f1a”
// URLs
$url_1 = “https://bvqie.com”
$url_2 = “https://hpncallback.qianxun168.com”
$url_3 = “https://hpncallback.gold5play.com”
$url_4 = “https://sdk-nps.ips5.info”
// IP addresses
$ip_1 = “159.138.237.10”
$ip_2 = “172.10.10.10”
condition:
any of ($sha1*) or any of ($url*) or any of ($ip*)
Recommendations:
STRATEGIC RECOMMENDATIONS
- Implement Mobile Device Management (MDM) policy to enhance corporate data security by monitoring, managing, and securing mobile devices, such as laptops, smartphones, and tablets that are used in enterprises.
- Maintain an up-to-date inventory of all active software used within the organization and perform regular self-audits of workstations, servers, laptops, and mobile devices to identify unauthorized/ restricted software.
- Configure the organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT RECOMMENDATIONS
- Incorporate a written software policy that educates employees on good practices in relation to software and the potential implications of downloading and using restricted software.
- Security Awareness training should be mandated for all company employees. The training should ensure that employees:
- Avoid downloading and executing files from unverified sources.
- Move beyond the traditional model of security awareness towards Improved Simulation and training exercises that mimic real attack scenarios, account for behaviors that lead to a compromise, and are measured against real attacks the organization receives.
TACTICAL RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Evaluate the security and reputation of each piece of open-source software or utilities before usage.
- Enforce policies to validate third-party software before installation.
- Add the Yara rules for threat detection and monitoring, which will help to detect anomalies in log events and identify and monitor suspicious activities.
CYFIRMA’S WEEKLY INSIGHTS
1. Weekly Attack Types and Trends
Key Intelligence Signals:
- Attack Type: Ransomware Attacks, Spear Phishing, Vulnerabilities & Exploits, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains, Espionage.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware – RansomHouse Ransomware, SafePay Ransomware| Malware – Baohuo
- RansomHouse Ransomware– One of the ransomware groups.
- SafePay Ransomware – One of the ransomware groups.
Please refer to the trending malware advisory for details on the following: - Malware – Baohu
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.
2. Threat Actor in Focus
Inside the Threat: MuddyWater – The Stealthy PowerShell Espionage Campaign
- Threat Actor: MuddyWater
- Attack Type: Connection Proxy, Credential Dumping, Exploitation of Vulnerabilities, Spear-phishing, Living off the Land (LOTL).
- Objective: Information theft, Espionage
- Suspected Target Technology: Office Suites Software, Operating System, Web Application, Huawei
- Suspected Target Geography: Austria, Azerbaijan, Bahrain, Belarus, Central Asia, Georgia, India, Iran, Islamic Republic of Iraq, Islamic Republic of Israel, Jordan, Korea, Mali, Middle East, Pakistan, Republic of Russia, Saudi Arabia, Southwest Asia, Tajikistan, Turkey, Ukraine, United Arab Emirates, United States
- Suspected Target Industries: Aerospace & Defense, Agriculture, Capital Goods, Consumer Services, Energy Equipment & Services, Finance, Food, Gaming, High Tech, IT Service Providers, Individuals, Media & Entertainment, Military, NGO, Natural Resources, Oil & Gas, Politics, Telecommunication Services, Transportation, Construction, Cryptocurrency, Education, Engineering, Government, Healthcare, Metals.
- Business Impact: Data Theft, Operational Disruption, Reputational Damage
About the Threat Actor
MuddyWater is an APT group that primarily targets victims in the Middle East, employing in-memory attack techniques via PowerShell. Their operations fall under the “Living off the Land” category, as they avoid creating new binaries on the victim’s system, which helps maintain a low detection profile and minimal forensic footprint.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2017-0199 | Microsoft Office | 7.8 | Link1, link2, link3 |
| CVE-2017-8759 | Microsoft .NET Framework | 7.8 | link |
| CVE-2017-11882 | Microsoft Office | 7.8 | link |
| CVE-2017-17215 | Huawei HG532 | 8.8 | – |
| CVE-2020-0688 | Microsoft Exchange software | 8.8 | Link1, link2 |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1559.001 | Inter-Process Communication: Component Object Model |
| Execution | T1559.002 | Inter-Process Communication: Dynamic Data Exchange |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1137.001 | Office Application Startup: Office Template Macros |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1218.003 | System Binary Proxy Execution: CMSTP |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1027.010 | Obfuscated Files or Information: Command Obfuscation |
| Defense Evasion | T1027.003 | Obfuscated Files or Information: Steganography |
| Defense Evasion | T1027.004 | Obfuscated Files or Information: Compile After Delivery |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Credential Access | T1555 | Credentials from Password Stores |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1003.004 | OS Credential Dumping: LSA Secrets |
| Credential Access | T1003.005 | OS Credential Dumping: Cached Domain Credentials |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Lateral Movement | T1210 | Exploitation of Remote Services |
| Collection | T1113 | Screen Capture |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1104 | Multi-Stage Channels |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1219 | Remote Access Tools |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
Latest Developments Observed
The threat actor is suspected of deploying the Phoenix v4 backdoor in a new phishing campaign that leverages a compromised mailbox accessed through NordVPN to conceal its identity and evade attribution. The campaign primarily targets government and critical infrastructure sectors across the Middle East and North Africa (MENA) regions. The malware gathers system details, modifies registry keys, and connects to a command-and-control (C2) server for instructions. The intent appears to be espionage.
ETLM Insights
MuddyWater remains an active, espionage-focused Advanced Persistent Threat (APT) group aligned with Iranian state interests. The group continues to evolve its attack methodologies and expand its operational footprint across multiple industries and geographies to execute high-impact cyber-espionage campaigns.
Recent observations indicate that the threat actor is potentially enhancing its technical sophistication and operational resilience. The group is expected to increasingly leverage AI-generated phishing lures, deepfake media, and cloud- hosted command-and-control (C2) infrastructures to improve deception, persistence, and scalability of its operations.
The threat actor’s tactics, techniques, and choice of targets demonstrate a clear espionage-driven intent, primarily focused on intelligence collection and sustained network infiltration within strategic sectors.
The continued evolution of this actor underscores the necessity for organizations to strengthen email and identity security, cloud monitoring, and behavioral analytics to detect and mitigate sophisticated, state-linked intrusion attempts.
IOCs
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule MuddyWater_Indicators
meta:
author = “CYFIRMA”
description = “Detects files containing specific CVEs, IPs, domains, and Mozi-related indicators”
date = “2025-10-28”
strings:
// CVE indicators
$cve1 = “CVE-2017-0199”
$cve2 = “CVE-2017-8759”
$cve3 = “CVE-2017-11882”
$cve4 = “CVE-2017-17215”
$cve5 = “CVE-2020-0688”
$cve6 = “CVE-2025-4609”
$cve7 = “CVE-2020-1472”
$cve8 = “CVE-2018-13379”
$cve9 = “CVE-2014-8361”
$cve10 = “CVE-2019-0797”
// IP addresses
$ip1 = “1.1.1.1”
$ip2 = “67.228.235.91”
$ip3 = “141.98.252.143”
$ip4 = “31.171.154.67”
// Domains
$domain1 = “lab52.io”
$domain2 = “filetransfer.io”
$domain3 = “rambler.ru”
// Malware/Mozi indicators
$mozi1 = “elf:mozi.m”
$mozi2 = “Mozi.m”
$mozi3 = “index.php” condition:
any of ($cve*) or any of ($ip*) or any of ($domain*) or any of ($mozi*)
Recommendations
Strategic
- Incorporate Digital Risk Protection (DRP) as part of the overall security posture to proactively defend against impersonations and phishing attacks.
- Assess and deploy alternatives for an advanced endpoint protection solution that provides detection/prevention for malware and malicious activities that do not rely on signature-based detection methods.
Management
- Look for email security solutions that use ML- and AI-based anti-phishing technology for BEC protection to analyze conversation history to detect anomalies, as well as computer vision to analyze suspect links within emails.
- Regularly reinforce awareness of unauthorized attempts with end-users across the environment and emphasize the human weakness in mandatory information security training sessions.
Tactical
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- For better protection coverage against email attacks (like spear phishing, business email compromise, or credential phishing attacks), organizations should augment built-in email security with layers that take a materially different approach to threat detection.
- Protect accounts with multi-factor authentication. Exert caution when opening email attachments or clicking on embedded links supplied via email communications, SMS, or messaging.
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Add the YARA rules for threat detection and monitoring, which will help to detect anomalies in log events, identify and monitor suspicious activities.
3. Major Geopolitical Developments in Cybersecurity
China accuses the US of hacking its National Time Service Center
China’s Ministry of State Security (MSS) has alleged that the U.S. National Security Agency (NSA) conducted a cyberattack on the National Time Service Center (NTSC), a public institution tasked with maintaining China’s standard time. Comparable to the U.S. Naval Observatory, the NTSC supports critical sectors, including communications, finance, power, transportation, surveying, and defense, with high-precision time services. The MSS claims to possess “ironclad evidence” of the NSA’s attempts to steal state secrets and engage in cyber espionage, with China’s CERT releasing a technical analysis of the incident. However, many Western analysts view these accusations as a diversion from allegations against Beijing’s Salt Typhoon hacking operations.
From April 18, 2023, the intruders reportedly used those credentials to repeatedly infiltrate NTSC computers, mapping the institute’s network infrastructure for further probing. The campaign escalated between August 2023 and June 2024, with the deployment of a sophisticated “cyber warfare platform” that, according to the Chinese government, activated 42 specialized cyber tools to launch high-intensity attacks on multiple internal NTSC systems, including attempts to sabotage the Accurate Ground-based Time Service System (AGTSS), a terrestrial backup to China’s GPS equivalent.
ETLM Assessment:
The MSS described these tactics as involving forged digital certificates to evade antivirus software, high-strength encryption to erase traces, and operations routed through proxies in the Philippines, Japan, Taiwan, Europe, and VPNs, often conducted during late-night hours in Beijing time. If true, this modus operandi would mean attackers have pursued a dual-track strategy of intelligence gathering and strategic sabotage preparation. Primarily, the objectives centered on stealing state secrets and conducting cyber espionage. Secondarily, the escalation to deploying a “cyber warfare platform” with 42 specialized tools between August 2023 and June 2024 suggests a focus on pre-positioning for disruption, aiming to implant persistent access for future sabotage rather than immediate exploitation.
Disabling or manipulating the high-precision ground-based timing system (AGTSS), potentially by injecting malware to alter time signals or erase synchronization data, leads to immediate desynchronization of national networks. This could manifest among many other things as network and communications failures: Time-stamped packets in telecommunications would misalign, causing packet loss, delayed data transmission, or complete outages in mobile and internet services, paralyzing emergency response and daily connectivity. This aligns with geopolitical motives in the U.S.-China rivalry, where controlling timing infrastructure could yield leverage in conflicts over Taiwan or the South China Sea by enabling timed disruptions to Beijing’s command-and-control networks.
Russian hackers behind US nuclear weapons manufacturing site hack; Russian hackers deploy new malware
According to recent research, foreign hackers used SharePoint vulnerabilities to breach the Kansas City National Security Campus (KCNSC), which manufactures roughly 80% of the non-nuclear parts in the US’s nuclear stockpile. Microsoft patched the flaws this summer after the vulnerabilities were exploited in a wave of zero-day attacks. The US National Nuclear Security Administration (NNSA) disclosed in July that it had been affected by the attacks but didn’t share details.
While researchers attributed the initial zero-day attacks to Chinese state-sponsored actors, US security personnel quoted in the media attribute the KCNSC incident to a Russian threat actor. Meanwhile, Russian hackers have been observed by researchers deploying new strains of malware dubbed NOROBOT. Just five days after Google’s May 2025 report on COLDRIVER’s LOSTKEYS malware, the group adopted new malware families. Researchers note that COLDRIVER is deploying the new malware more aggressively than any prior campaigns. Delivered through CAPTCHA- themed ClickFix attacks, NOROBOT’s infection chain has evolved significantly. Initially simplified to boost deployment success, it later regained complexity by splitting cryptography keys, complicating campaign tracking. This ongoing development underscores COLDRIVER’s efforts to evade detection and target high-value individuals for intelligence collection.
ETLM Assessment:
FSB-linked hackers, often operating as state-sponsored cyber units, are known for their sophisticated and covert operations targeting government entities, critical infrastructure, and private organizations worldwide. Groups like Fancy Bear (APT28), believed to be associated with Russia’s Federal Security Service (FSB), have been implicated in high-profile cyberattacks, election interference, and breaches of European governmental networks. These hackers employ advanced techniques, including spear-phishing, zero-day exploits, and custom malware, to infiltrate systems and extract sensitive data. Their activities are typically driven by geopolitical motives, aiming to gather intelligence, disrupt adversaries, or influence political outcomes. The FSB’s backing provides these groups with significant resources, enabling persistent and evolving campaigns that challenge global cybersecurity efforts. A campaign like the KCNSC hack this summer would be in line with their operations.
4. Rise in Malware/Ransomware and Phishing
RansomHouse Ransomware Impacts Kurogane Kasei Co., Ltd
- Attack Type: Ransomware
- Target Industry: Manufacturing
- Target Geography: Japan
- Ransomware: RansomHouse Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Kurogane Kasei Co., Ltd (https[:]//www[.]kuroganekasei[.]com/), was compromised by RansomHouse Ransomware. Kurogane Kasei Co., Ltd. is a development-focused Japanese chemical manufacturer specializing in organic synthesis and fine chemicals. The company’s main operations include joint research and development, contract synthesis, and scalable chemical production ranging from small gram-scale prototypes to ton-scale manufacturing. They actively serve sectors such as electronics, pharmaceuticals, and agrochemicals, leveraging advanced technologies like esterification and maintaining specialized facilities for dust-free, metal-free processes, especially for high-purity and low-metal ion chemical applications crucial to electronic materials. The compromised data includes sensitive and confidential information related to the organization.

Source: Dark Web
Relevancy & Insights:
- RansomHouse emerged in March of 2022 and is categorized as a multi-pronged extortion threat. The attackers exfiltrate all enticing data and threaten to post it all publicly.
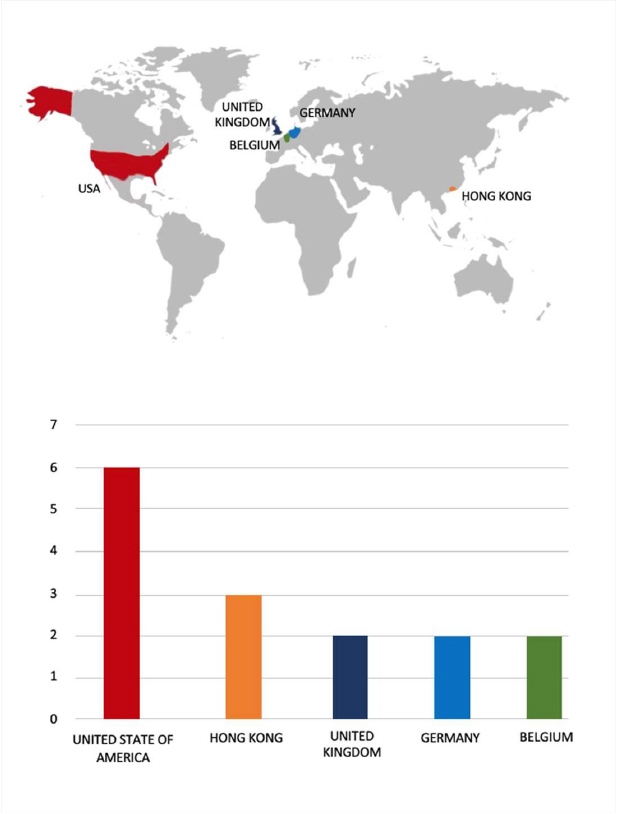
- The RansomHouse Ransomware group primarily targets countries such as the United States of America, Hong Kong, the United Kingdom, Germany, and Belgium.
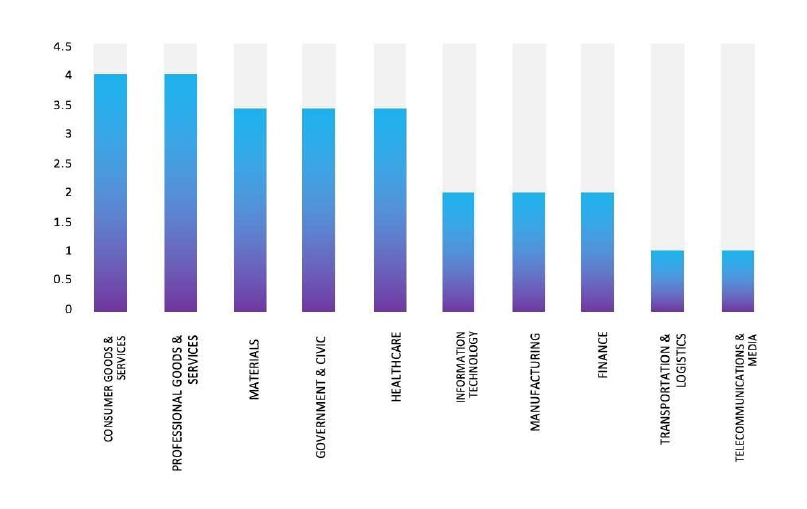
- The RansomHouse Ransomware group primarily targets industries such as Consumer Goods & Services, Professional Goods & Services, Materials, Government & Civic, and Healthcare.
- Based on the RansomHouse Ransomware victims list from 1st Jan 2025 to 28th October 2025, the top 5 Target Countries are as follows:
- The Top 10 Industries most affected by the RansomHouse Ransomware victims list from 1st Jan 2025 to 28th October 2025 are as follows
ETLM Assessment:
According to CYFIRMA’s assessment, RansomHouse ransomware predominantly targets large enterprises and high-value organizations through phishing and spear phishing campaigns. The group also employs third-party frameworks, such as Vatet Loader, Metasploit, and Cobalt Strike, to gain initial access and perform lateral movements within victim networks. RansomHouse typically skips data encryption, focusing instead on exfiltrating sensitive data to extort victims by threatening to publicly release the stolen information. This approach allows the group to maintain stealth and prolong their presence in targeted environments.
SafePay Ransomware Impacts the MINO Group
- Attack Type: Ransomware
- Target Industry: Manufacturing
- Target Geography: Japan
- Ransomware: SafePay Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary
CYFIRMA observed in an underground forum that a company from Japan, MINO Group (https[:]//www[.]mino-in[.]co[.]jp/), was compromised by SafePay Ransomware. MINO Group is a Japanese manufacturer that designs and builds screen-printing machines, stencil makers, dryers, printing accessories, and specialty inks. The exposed data comprises highly confidential and sensitive information associated with the organization.
Source: Dark Web
Relevancy & Insights:
- SafePay Ransomware is a rapidly emerging and sophisticated ransomware threat first identified in September 2024.
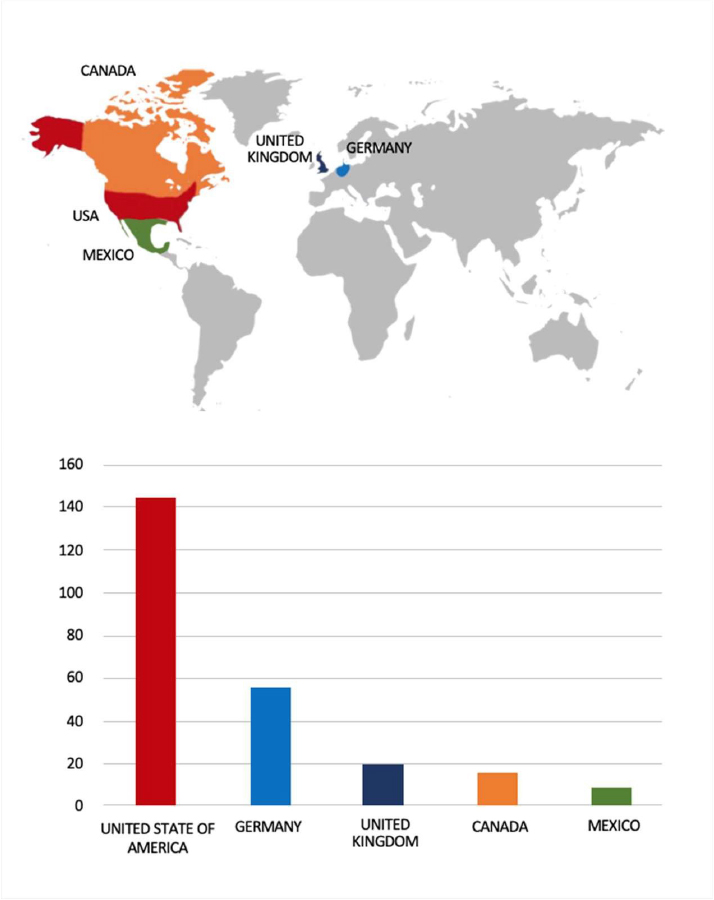
- The SafePay Ransomware group primarily targets countries such as the United States of America, Germany, the United Kingdom, Canada, and Mexico.
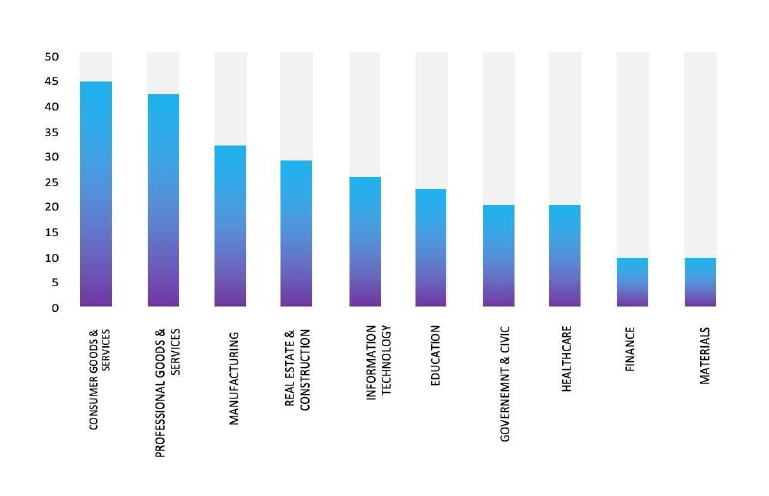
- The SafePay Ransomware group primarily targets industries, including Consumer Goods & Services, Professional Goods & Services, Manufacturing, Real Estate & Construction, and Information Technology.
- Based on the SafePay Ransomware victims list from 1st Jan 2025 to 28th October 2025, the top 5 Target Countries are as follows:
- The Top 10 Industries most affected by the SafePay Ransomware victims list from 1st Jan 2025 to 28th October 2025 are as follows:
ETLM Assessment:
According to CYFIRMA’s assessment, SafePay represents a sophisticated, fast- moving ransomware threat capitalizing on VPN weaknesses and credential theft, employing effective double extortion tactics to maximize ransom payments.
Organizations, especially in highly targeted sectors and regions, must prioritize layered defenses and active hunting for early detection.
5. Vulnerabilities and Exploits
Vulnerability in Docker Desktop for Windows installer
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Client/Desktop applications
- Vulnerability: CVE-2025-9164
- CVSS Base Score: 8.8 Source
- Vulnerability Type: Untrusted search path
- Summary: The vulnerability allows a local user to escalate privileges on the system.
Relevancy & Insights:
The vulnerability exists due to the usage of an untrusted search path in Docker Desktop Installer.exe.
Impact:
A local user can place a malicious .dll file into a specific location on the system and execute arbitrary code with escalated privileges.
Affected Products:
https[:]//docs[.]docker[.]com/security/security- announcements/#docker-desktop-4490-security-update-cve-2025-9164
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
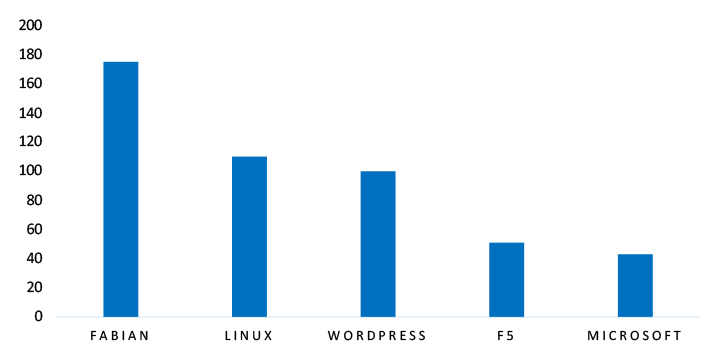
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in Docker Desktop for Windows Installer can pose significant threats to user privacy and system security. This can impact various industries globally, including technology, finance, healthcare, and software development. Ensuring the security of Docker Desktop for Windows is crucial for maintaining the integrity and protection of users’ environments worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding containerized application development, virtualization processes, and secure software deployment across different geographic regions and sectors.
6. Latest Cyber-Attacks, Incidents, and Breaches
The Gentlemen Ransomware attacked and published the data of 2GO Group, Inc.
- Threat Actor: The Gentlemen Ransomware
- Attack Type: Ransomware
- Objective: Data Leak, Financial Gains
- Target Technology: Web Applications
- Target Industry: Logistics and Transportation
- Target Geography: Philippines
- Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
Recently, the Gentlemen Ransomware was observed attacking and publishing the data of 2GO Group, Inc. (https[:]//2go[.]com[.]ph/) on its dark web website. 2GO Group, Inc. is the largest integrated transportation and logistics provider in the Philippines, offering end-to-end multimodal logistics and transportation solutions.
2GO operates through several specialized business units, including 2GO Sea Solutions, 2GO Express, 2GO Special Containers and Projects, 2GO Forwarding, and 2GO Logistics, providing services ranging from sea freight and passenger transport to warehousing, special container transport, project logistics, express delivery, and e-commerce logistics. The ransomware attack on 2GO Group resulted in a significant data leak, compromising a variety of sensitive organizational information. The exposed data includes personally identifiable information (PII), financial records, and transportation and logistics data, along with other confidential and proprietary information related to the company.
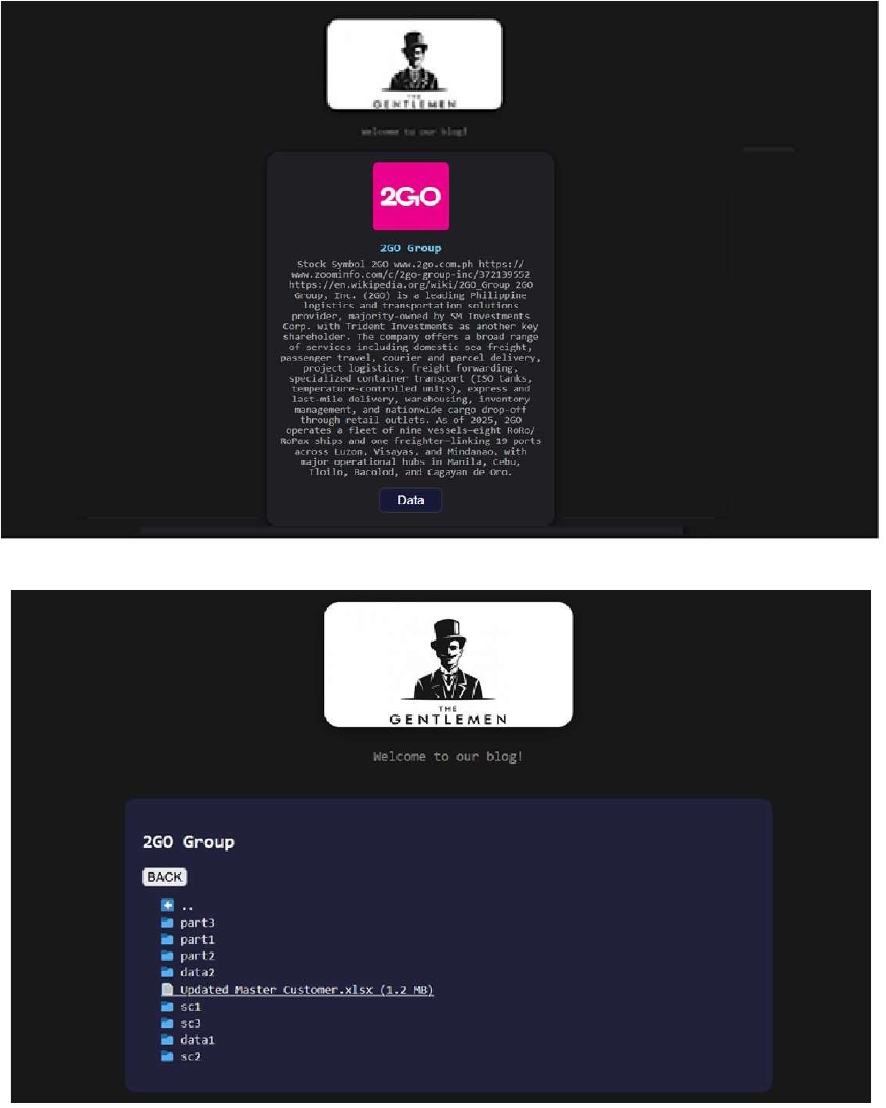
Source: Dark Web
Relevancy & Insights:
- The Gentlemen ransomware is a recently emerged, highly sophisticated threat group.
- The Gentlemen Ransomware group primarily targets industries, including Manufacturing, Healthcare, Materials, Information Technology, and Consumer Goods & Services.
ETLM Assessment:
According to CYFIRMA’s assessment, the Gentlemen ransomware group exemplifies the rising sophistication and persistence of modern ransomware actors, necessitating tailored enterprise defenses and vigilant threat monitoring.
7. Data Leaks
Royal Thai Army Enlistment Portal Data Advertised on a Leak Site
- Attack Type: Data leak
- Target Industry: Government
- Target Geography: Thailand
- Objective: Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary: The CYFIRMA Research team observed that a threat actor, “Kazu,” claims to have breached the Official Royal Thai Army Online Enlistment Portal (RTA). This portal is the official online system used for voluntary military enlistment, allowing eligible Thai males to apply to serve as regular soldiers instead of going through the traditional draft process.
According to the actor, the allegedly compromised data is being offered for sale and includes:
- A total of 30,084 files
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
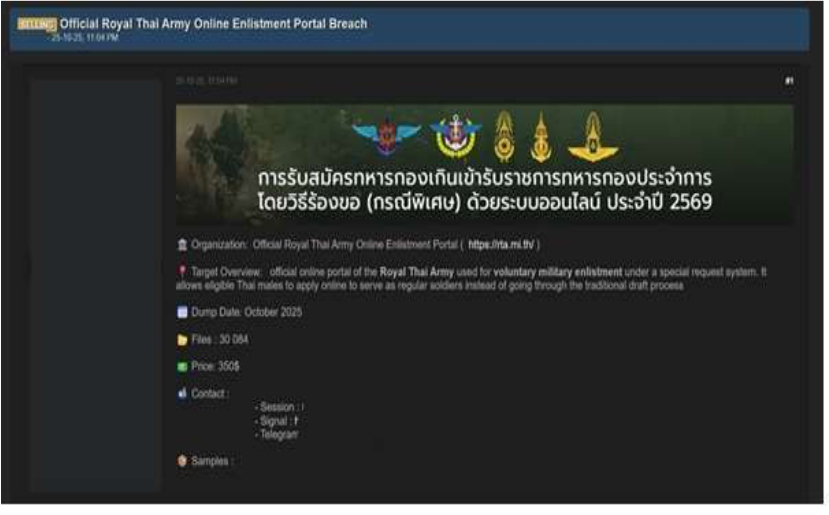
Source: Underground Forums
Vidal Health Insurance TPA Pvt. Ltd. (Vidal Health) Data Advertised on a Leak Site
- Attack Type: Data leak
- Target Industry: Finance, Healthcare Services
- Target Geography: India
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed that a threat actor, “Kazu,” claims to have breached Vidal Health Insurance TPA Pvt. Ltd. (Vidal Health), a leading IRDAI-licensed third-party administrator in India. The company facilitates health insurance services, including claims processing and cashless hospitalization, for major insurers and government health schemes like Ayushman Bharat.
The threat actor is advertising a database of 472 GB, allegedly exfiltrated in October 2025 and containing 326,865 files. The data is being offered for sale for $3,000.
According to the actor and samples provided, the compromised data includes a vast amount of sensitive patient and personal information:
- Full names
- Patient medical records
- Lab reports (e.g., ECG, USG)
- Pre-authorization and consultation forms
- Hospital admission and billing documents
- Know Your Customer (KYC) files
- Photo IDs
- Aadhaar card details
- PAN card details
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Kazu” has recently emerged as a notably active group engaged in data leak activities. Credible sources have tied the group to multiple security breaches involving unauthorized system access and attempts to sell stolen data on dark web marketplaces. The group’s ongoing operations illustrate the persistent and escalating cyber threats stemming from underground forums. These incidents reinforce the critical need for organizations to bolster cybersecurity through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
- Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being exploited.
- Ensure proper database configuration to mitigate the risk of database-related attacks.
- Establish robust password management policies, incorporating multi-factor authentication and role-based access to fortify credential security and prevent unauthorized access.
8. Other Observations
The CYFIRMA Research team observed that a threat actor claims to have breached Jazeera Airways (jazeeraairways.com), a Kuwaiti low-cost airline. The actor alleges the data contains 15 million passenger records spanning from 2020 to 2023 and is offering it for sale.
According to the actor, the compromised data includes a vast amount of personally identifiable information (PII). Screenshots provided as proof suggest the leak originates from the airline’s database tables and includes the following data types:
- Full names
- Date of Birth (DOB)
- Gender
- Nationality and country of residence
- Email addresses
- Physical addresses
- Passenger IDs and Booking IDs
- Hashed passwords (potentially for agents or employees)
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
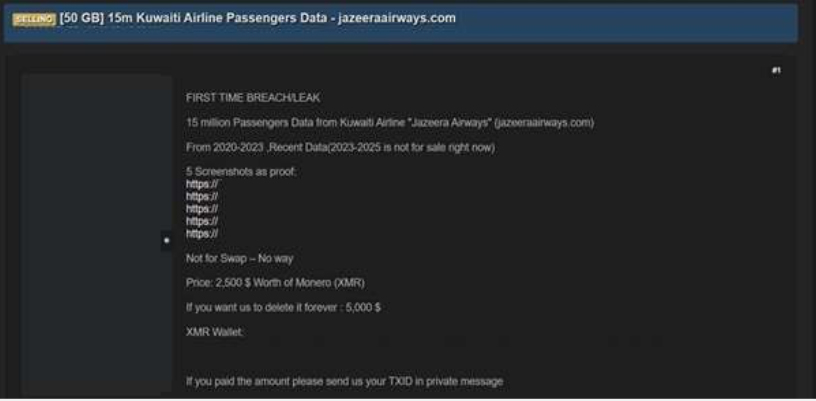
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organisations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Delay a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, and active network monitoring, through next-generation security solutions and a ready-to-go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence, providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied, and the proper implementation of security technologies, followed by corrective actions, remediations, and lessons learned.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcomings of EDR and SIEM solutions.
- Detection processes should be tested to ensure awareness of anomalous events. Timely communication of anomalies should be continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defences based on the tactical intelligence provided.
- Deploy detection technologies that are behavioral anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.
Situational Awareness – Cyber News
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
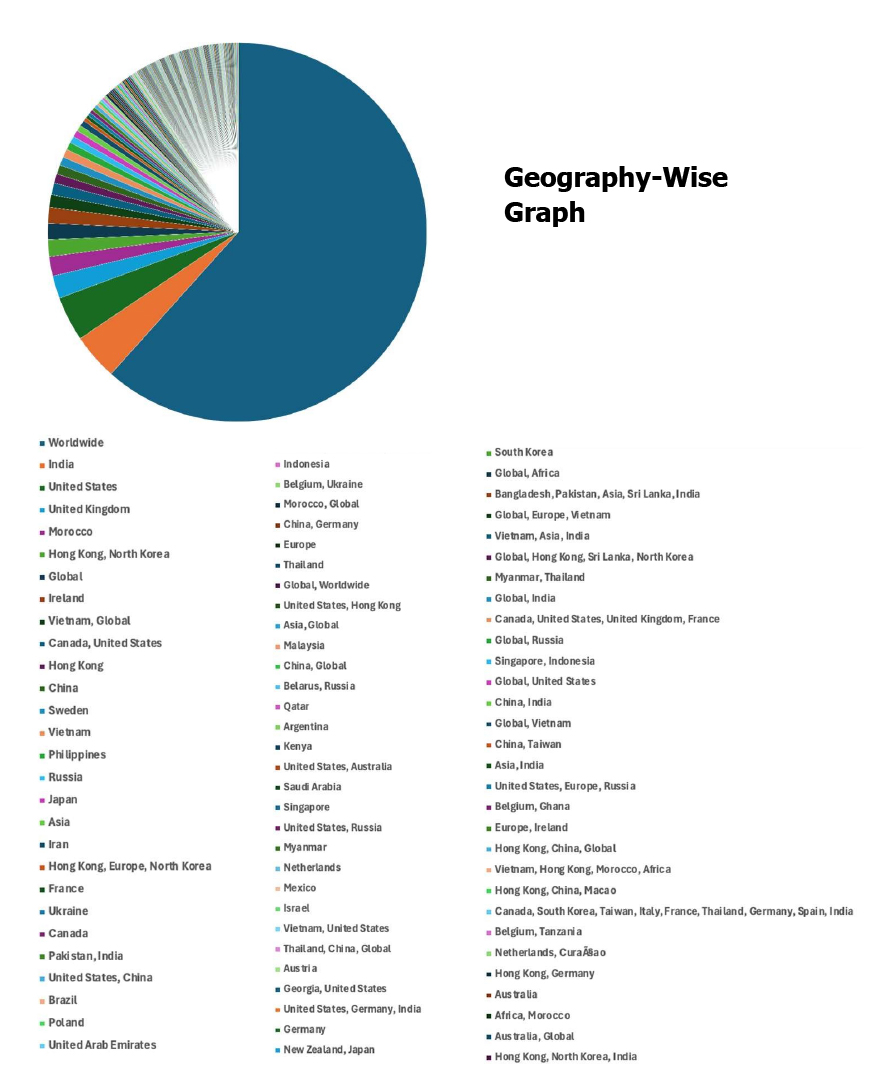


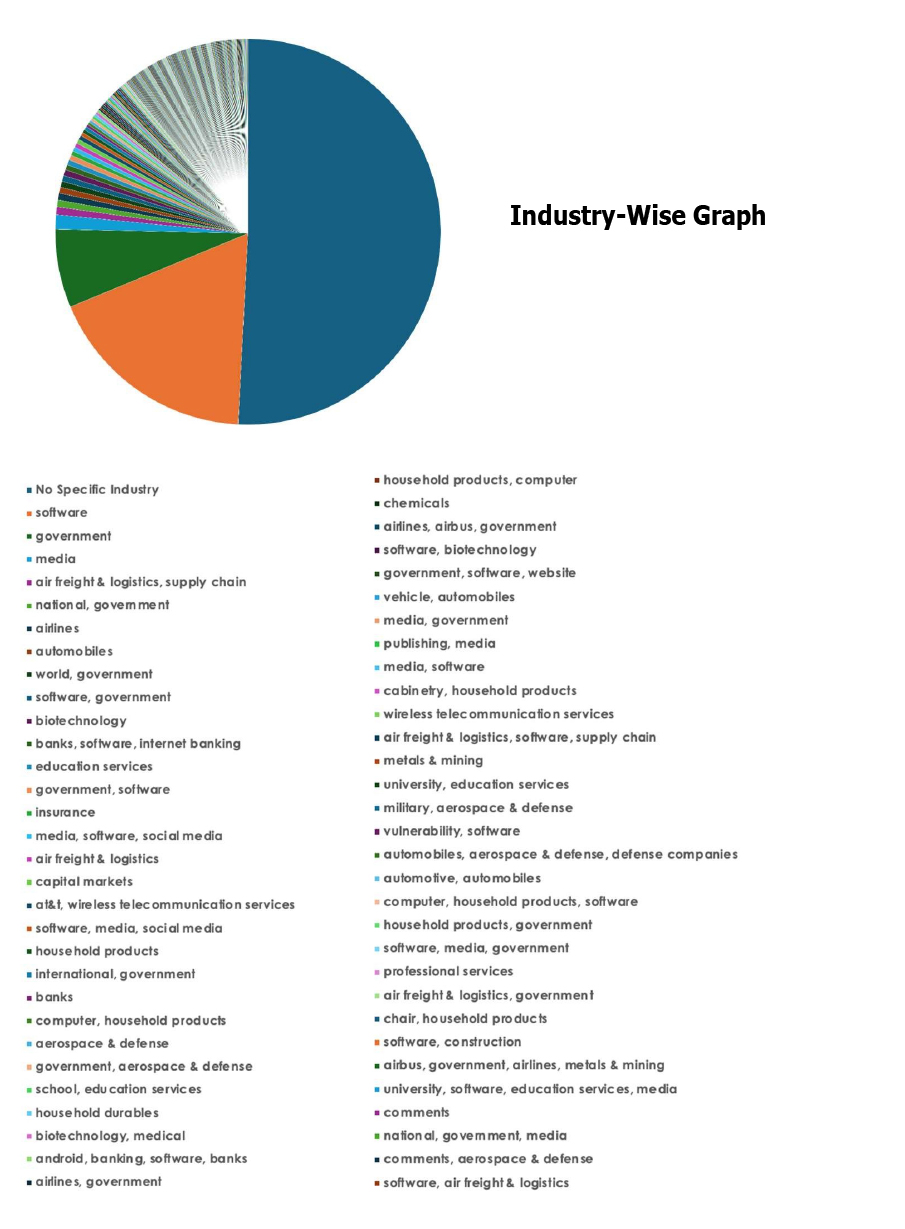

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.
