This newsletter is brought to you by cloud security firm Prowler. You can subscribe to an audio version of this newsletter as a podcast by searching for “Risky Business” in your podcatcher or subscribing via this RSS feed.
More than 12,000 internal documents were leaked online from Chinese security firm KnownSec.
The files were uploaded last week on GitHub by an unknown individual and later removed before the repo got any widespread circulation.
According to analyses from Mrxn and NetAskari, who got their hands on the leak, the most recent documents are from 2023. This suggests this was likely when the files were stolen/exfiltrated from the company’s network, or at least someone intentionally truncated the leak to keep the most recent files for themselves.
At the time of writing, it is unclear if this is the case of a disgruntled employee leaking things out of spite or a hack-and-dump operation orchestrated by hacktivists or state-sponsored hackers.
As for the files themselves, they are a massive intelligence gold mine.
KnownSec is widely known to security researchers in the West for its ZoomEye IoT search engine, but the company is also a major cyber contractor for the Chinese military and intelligence services.
The leak allegedly contains extensive details about KnownSec’s contracts with the Chinese government, hacking tools developed by its employees, and a list of targets from where the company gathered intelligence.
As NetAskari points out, the so-called “cyber weapons” as they’ve been described in some places, appear to be the regular RATs and data extraction and analysis tools that law enforcement tends to acquire everywhere around the globe.
The most interesting part of the leak is the “targets list,” a spreadsheet with the names of 80 entities from which KnownSec collected data.
Per NetAskari, the leak suggests KnownSec was involved in mapping out other nations’ digital infrastructure, which is no surprise since the company operates ZoomEye, a project that basically maps everything on the internet, similarly to how many Western products also do, like Shodan, Censys, or BinaryEdge. According to security firm StealthMole, KnownSec was involved in mapping the internet infrastructure of 28 countries.
The part that stands out is that KnownSec appears to have also collected data from the more “interesting” leaky servers it found in some countries.
This allegedly includes 95GB of immigration data from India, 3TB of call records stolen from South Korea’s LG U-Plus telecom operator, 459GB of road planning data from Taiwan, passwords for Taiwanese Yahoo accounts, data on Brazilian LinkedIn accounts, and all sorts of random things you find on leaky servers.
The leak looks rather benign compared to a similar leak at i-SOON, another Chinese cyber contractor.
That leak, in early 2024, linked i-SOON to official Chinese cyber operations and led to the US government indicting ten of the company’s employees this year.
Due to its considerable size, we might need a little more time to assess the importance of this leak.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
CBO breach not contained: A security breach at the US Congressional Budget Office has not been contained and is still ongoing. Workers at other federal agencies were told not to interact with CBO staff for the time being. This included clicking links in emails and interacting with staff via Zoom, Microsoft Teams, and emails. [Politico]
Hackers leak Redback plans: An Iranian hacktivist group has leaked classified schematics for Australia’s Redback infantry fighting vehicles. The Cyber Toufan group published the files on its Telegram channel over the weekend. The group stole the files from Maya Technologies, an Israeli defense contractor involved in the production of some components. [Iran International]
JLR hack affected UK’s GDP growth: The ransomware attack on Jaguar Land Rover has impacted the UK’s national GDP growth. The Bank of England has confirmed that GDP growth statistics have been lower for the third quarter due to the incident. The attack disrupted car production at Jaguar factories, but also impacted the company’s entire supply chain of thousands of smaller companies. UK officials speculated the incident would impact the national GDP figure back in September.
Manassas closed due to cyberattack: Schools in the city of Manassas, near Washington, DC, stayed closed on Monday due to a cyberattack. The school district’s IT staff is restoring affected systems. Schools are set to reopen on Wednesday, after the Veterans Day holiday. [WJLA] [h/t DataBreaches.net]
Intel sues former employee for data theft: Intel has sued a former employee for allegedly stealing confidential data. The company says Jinfeng Luo stole more than 18,000 files days before his employment was set to end in July. Luo allegedly tried to copy data to an external hard drive but was blocked. He stole the files days later by connecting a NAS to Intel’s network. Luo had worked for Intel since 2014 before being fired on July 7. [The Mercury News]
Asahi at 10% after cyberattack: Japanese beermaker Asahi is only at 10% capacity more than a month after a cyberattack crippled its IT network. The beermaker has lost the number one spot in Japan’s beer market to rival Kirin since the attack. The company postponed its Q3 financial earnings, which were due this week, to focus on restoring operations ahead of the winter holidays, its strongest selling period. [Bloomberg]
General tech and privacy
The new copyright oxymoron: While AI companies are allowed to slurp everything they want, Quad9 warns that legal fees are drowning DNS resolvers, which are now being targeted by copyright owners to enforce blocks on piracy sites.
Firefox 145: Mozilla has released Firefox 144. New features and security fixes are included. The biggest feature in this release is an improved fingerprinting detection and blocking system, and the ability to force links opened from third-party apps to open next to the active tab.
Most Microsoft employees now use MFA: Microsoft says that most of its employees are now using phishing-resistant multi-factor authentication (MFA). 99.6% of employee accounts and devices have been migrated to a stronger form of MFA. The changes are part of the company’s Secure Future Initiative, a project started two years ago to overhaul the company’s security culture. The tech giant says it now has more than 35,000 engineers working full-time on security. In addition, all high-risk employees now work from locked-down Azure Virtual Desktop environments.
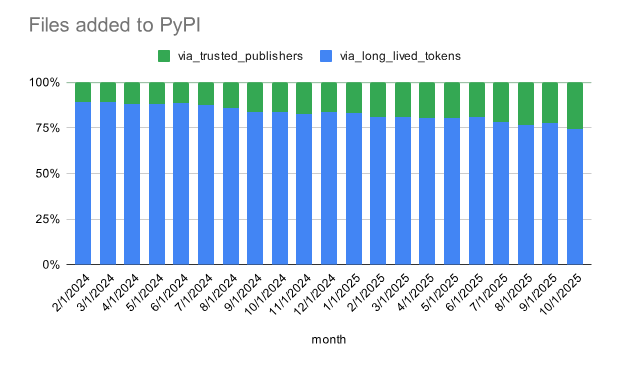
Trusted publishing adoption grows on PyPI: More than a quarter of all new PyPI package updates are now published via the platform’s Trusted Publishing mechanism. The system allows package maintainers to authorize CI/CD platforms to publish releases on their behalf using short-lived auth tokens. This eliminates the need to issue long-lived tokens to developer accounts that can be stolen and reused for malicious attacks.
Government, politics, and policy
CISA 2015 to get new extension: The crucial Cybersecurity Information Sharing Act of 2015 is about to be extended until January 30, next year. A provision in the legislation that ends the current US government shutdown also extends CISA 2015. The shutdown-ending bill passed the Senate on Sunday and is expected to clear the House this week. [CyberScoop]
FSB gets the power to cut off communications: The Russian FSB intelligence service will be able to cut off mobile and internet communications at will. The Russian government is modifying its communications law to grant the agency the legal powers over local telcos. The amendments are vague, and the FSB will be able to shut down mobile and internet access for anything that can be considered “emerging threats.” [Vedomosti]
UK NCSC retires two tools: The UK’s cybersecurity agency will retire its Web Check and Mail Check services on March 31, next year.
In this Risky Business sponsor interview, Casey Ellis chats with Toni de la Fuente, founder and CEO of Prowler, an open source platform for cloud security. They chat about how and why Prowler selectively applies AI to ensure it adds value rather than just because they can.
Arrests, cybercrime, and threat intel
Facebook phishing: Check Point researchers have spotted another phishing campaign targeting the owners of Facebook Business pages, primarily in the US.
Most K8s run recent versions: A DataDog study has found that most Kubernetes servers deployed in the wild are running supported versions, which must be some sort of world record.
Malicious npm package steals tokens: Veracode researchers have spotted a malicious npm package designed to steal tokens and secrets from an infected developer’s GitHub build systems.
£200 million in cyber claims: The Association of British Insurers has paid £197 million in cyber insurance claims to UK businesses last year. The sum is a 230% year-over-year increase over the £59 million paid in 2023. More than half of the payments were for ransomware and other malware-related incidents.
Malware technical reports
Maverick and Coyote: Cyberproof researchers look at the links between Maverick and Coyote, two Brazilian banking trojans. The research team also believes new versions of these two malware are in the works and are likely using AI.
Quantum Route Redirect: KnowBe4 looks at Quantum Route Redirect, a new phishing automation platform currently powering more than 1,000 phishing sites in the wild.
In this sponsored product demo, Prowler founder and CEO Toni de la Fuente walks Risky Business host Patrick Gray through the company’s open-source cloud security platform. Toni demonstrates how Prowler can identify and remediate security issues across AWS, Azure, GCP, and Kubernetes. There’s a pointy-clicky GUI interface and a CLI, and both come in handy in different ways. The Prowler platform is completely free and open source, but there is a hosted version you can pay for if you don’t want to run it yourself.
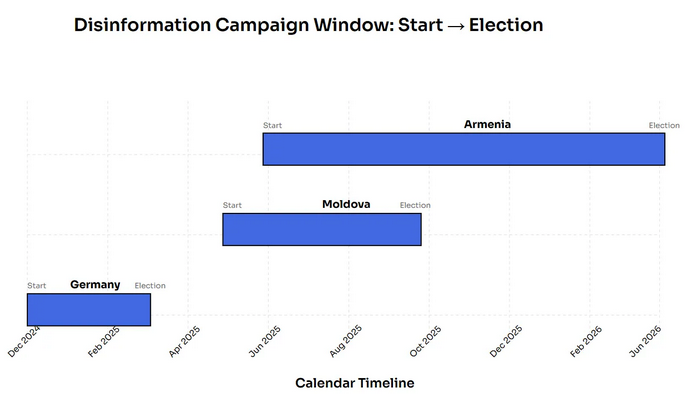
Russian info-ops switch to Armenia: After viciously targeting elections in Romania, Moldova, Poland, and the Czech Republic this year, Russian disinfo groups have now turned their sights on Armenia, “early and viciously,” according to NewsGuard. This is 14 months before the country’s election next year, the earliest campaign spotted from Russian groups so far. The tactics are the same. Fake stories about government corruption while portraying the pro-Kremlin parties as patriotic saviours.
More TrioFox exploitation: A threat actor tracked as UNC6485 has been hacking TrioFox file-sharing servers since at least late August. The attacks exploit a vulnerability (CVE-2025-12480) that can bypass authentication, access configuration files, and then run code on the TrioFox server. Patches for the bug were released in July. Attackers targeted systems that weren’t patched in time.
expr-eval vulnerability: There’s a vulnerability in expr-eval, a popular npm library used for mathematical expressions, that can lead to code execution via malicious user input. The library is often used for NLP and AI projects.
Patch Tuesday: Yesterday was the November 2025 Patch Tuesday. We had security updates from Adobe, Microsoft, Dell, IBM, SAP, Ivanti, Firefox, Supermicro, Intel, NVIDIA, Schneider Electric, Siemens, Rockwell Automation, Synology, and Zoom. Apple, Android, Chrome, Elastic, Fortinet, D-Link, AMD, ABB, Samsung, Qualcomm, Cisco, Palo Alto Networks, QNAP, Drupal, Django, and Moxa released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 63 vulnerabilities, including fixes for an actively exploited zero-day, CVE-2025-62215, a Windows kernel EoP.
Infosec industry
Threat/trend reports: ABI, BSI, Check Point, Google Wiz, Incogni, and S&P Global have recently published reports and summaries covering various threats and infosec industry trends.
New tool—PhantomTask: Advens researcher BlackWasp has released PhantomTask, a Windows command-line utility for creating and executing scheduled tasks with session-specific control.
New tool—Magnet: Security engineer Simone Ragonesi has released Magnet, a purple-team telemetry & simulation toolkit.
BSides Groningen videos: Talks from the BSides Groningen 2025 security conference, which took place in May, are now available on YouTube.
BSides Zagreb videos: Talks from the BSides Zagreb 2025 security conference, which took place in March, are now available on YouTube.
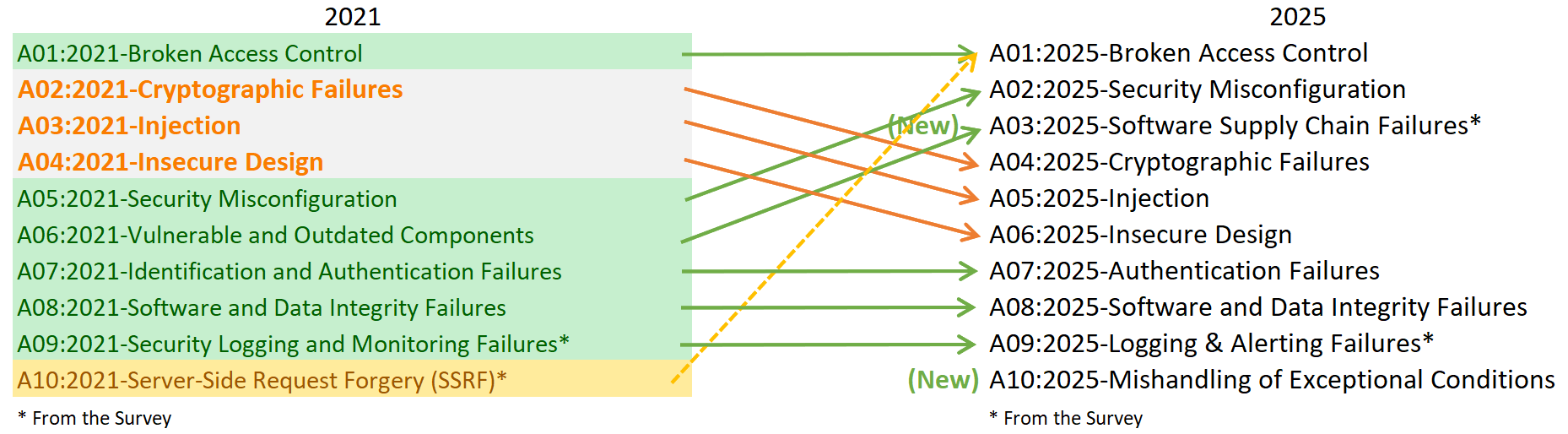
OWASP Top 10 RC1: The OWASP Foundation is releasing a new version of the OWASP Top 10 list of most dangerous vulnerabilities. For the first time, the Software Supply Chain Failures category has entered the Top 10, in the #3 spot. Another new entry is the Mishandling of Exceptional Conditions, which entered the Top at #10. The OWASP Top 10 ranking is updated once every 3-4 years. The last version was released in 2021. [h/t Uncle Joe]
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss how cyber criminals and even state actors are being dumb about using AI.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about aggressive US cyber operations targeting the Venezuelan government in President Trump’s first term. These were narrowly successful in that they achieved their immediate operational goals, but they didn’t achieve Trump’s broader policy goal of ousting Venezuelan leader Nicolás Maduro.
