One of our customers was contacted on LinkedIn about a job offer. The initial message was followed up by an email:
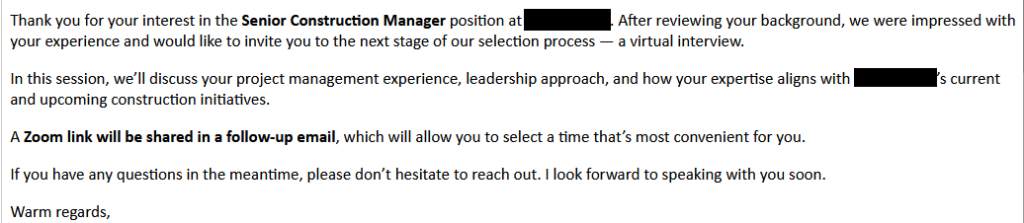
“Thank you for your interest in the Senior Construction Manager position at company. After reviewing your background, we were impressed with your experience and would like to invite you to the next stage of our selection process — a virtual interview.
In this session, we’ll discuss your project management experience, leadership approach, and how your expertise aligns with company’s current and upcoming construction initiatives.
A Zoom link will be shared in a follow-up email, which will allow you to select a time that’s most convenient for you.
If you have any questions in the meantime, please don’t hesitate to reach out. I look forward to speaking with you soon.
Warm regards,”
I edited out the company name and the name of the supposed recruiter, but when we Googled that alleged recruiter’s name, he does work at the impersonated company (just not in HR). That’s not unique, though. We’ve heard several variants of very similar stories involving other companies and other names.
Other red flags included the fact that the email came from a Gmail address (not a company domain), and that the company has no openings for a Senior Construction Manager.
When our target replied they were looking forward to the interview, they received the “Meeting invitation” by email:
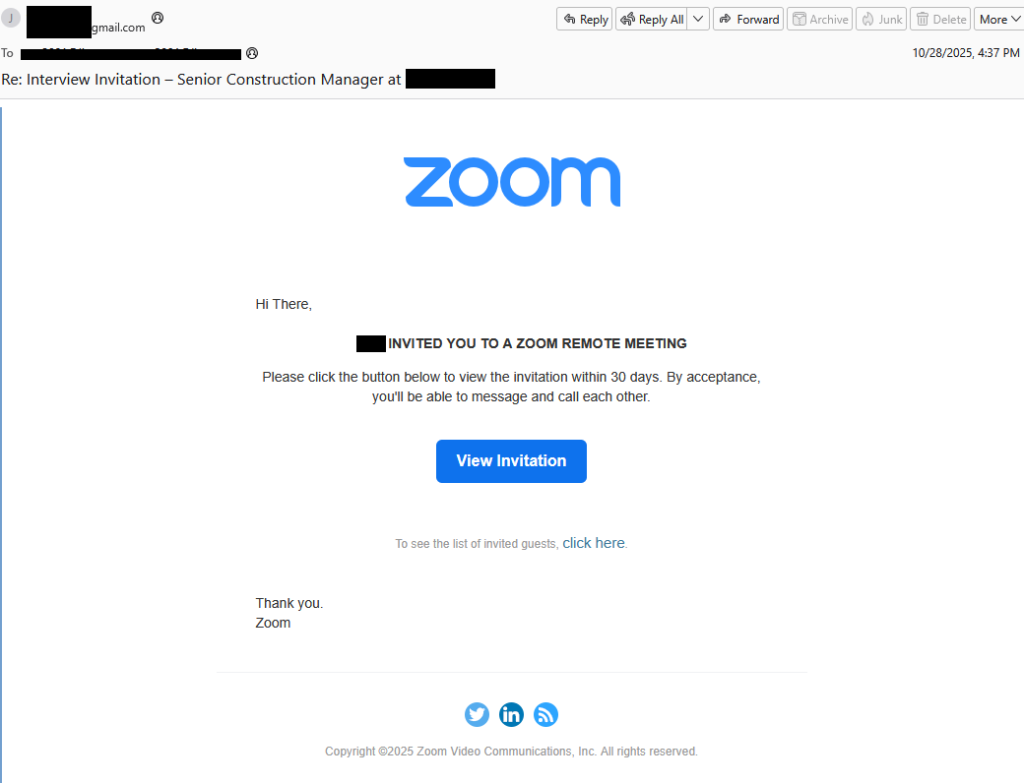
“Hi There,
recruiter INVITED YOU TO A ZOOM REMOTE MEETING
Please click the button below to view the invitation within 30 days. By acceptance, you’ll be able to message and call each other.
View Invitation button
To see the list of invited guests, click here.
Thank you.
Zoom”
Both links in this email were shortened t[.]co links that redirected to meetingzs[.]com/bt.
That site is currently unavailable, but users have reported seeing fake Windows update warnings, or notifications about having to install updates for their meeting application (Zoom, Teams—name your favorite). Our logs show that we blocked meetingzs[.]com for phishing and hosting a file called GoToResolveUnattendedUpdater.exe.
![Malwarebytes blocks meetingzs[.]com](https://www.malwarebytes.com/wp-content/uploads/sites/2/2025/11/meetingzscomblock.png)
While this file is not malicious in itself, it can be abused by cybercriminals. It’s associated with LogMeIn Resolve, a remote support tool, which attackers can fake or misuse to execute ransomware payloads once installed.
This tactic is part of a broader trend where attackers pose as recruiters or trusted contacts, inviting targets to meetings and requiring them to install software updates to participate. Those updates, however, can be malware installers or Remote Monitoring and Management (RMM) tools which can give attackers direct access to your device.
This type of attack is a prime example of how social engineering is becoming the primary way to gain initial access to you or your company’s system.
The best way to stay safe is to be able to recognize attacks like these, but there are some other things you can do.
- Always keep your operating system, software, and security tools updated regularly with the latest patches to close vulnerabilities.
- Use a real-time anti-malware solution with a web protection component.
- Be extremely cautious with unsolicited communications, especially those inviting you to meetings or requesting software installs or updates; verify the sender and context independently.
- Avoid clicking on links or downloading attachments from unknown or unexpected sources. Verify their authenticity first.
- Compare the URL in the browsers’ address bar to what you’re expecting.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
