A recent deep-dive into ClickFix-related infrastructure reveals a previously underestimated scale of adversarial activity, as over 13,000 unique hostnames were identified as part of ongoing phishing and malware delivery operations.
ClickFix campaigns exploit the web browser’s ability to write directly to a user’s clipboard, luring victims into executing malicious scripts under the guise of CAPTCHA verification and “I am not a robot” challenges.
For example, the site greenblock[.]me, a typical ClickFix destination, prompts users to run a PowerShell command that fetches and executes a Visual Basic script, often resulting in malware infection or further compromise.
The research team began monitoring ClickFix in mid-July 2025, initially observing relatively low volumes. However, an unexpected spike in mid-August 2025 led to the accumulation of 13,695 unique ClickFix-associated domains.
The surge was not sustained, which researchers speculate could indicate rapid evolution in the campaign’s tactics or waning operator interest.
Notably, ClickFix activity was tracked using a custom telemetry module focused exclusively on frontend infrastructure, rather than the malware payloads or backend infrastructure.
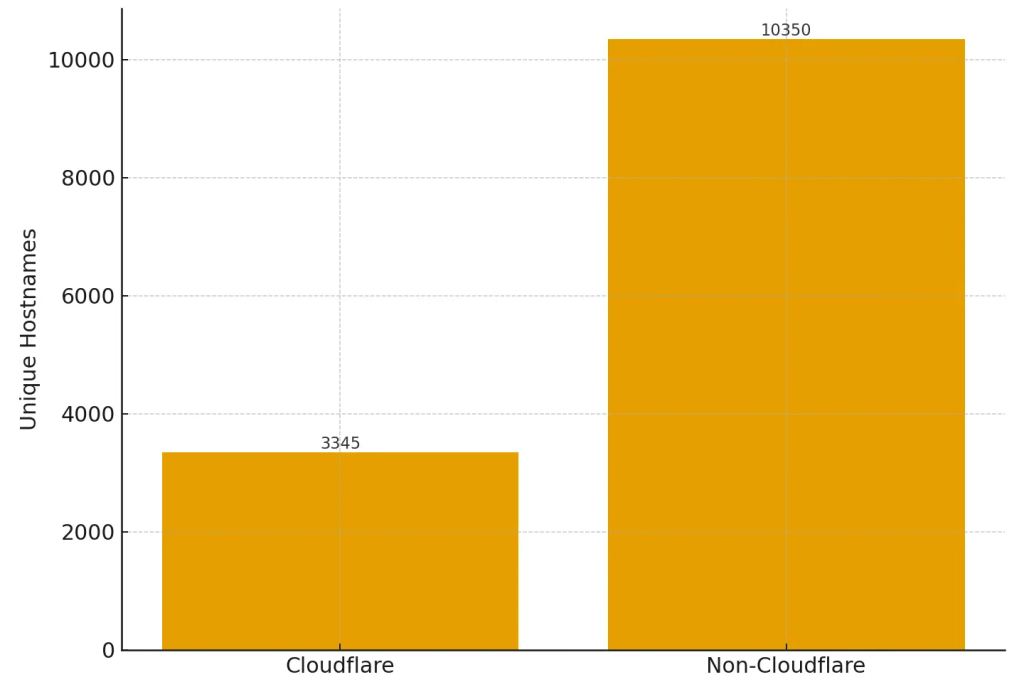
Cloudflare emerged as the single most prevalent hosting provider, shielding 24.4% (3,345 out of 13,695) of the detected malicious domains. Yet, the study identified nearly 500 different hosting providers supporting ClickFix, with many campaigns leveraging smaller VPS and CDN operators.
When Cloudflare data was temporarily excluded, analysis revealed that 41% of non-Cloudflare IP addresses hosted multiple unique ClickFix domains, often on budget or reseller networks.
Top providers included Rumahweb, Hawk Host, FranTech Solutions, and others, each with several dozen malicious hostnames associated with their infrastructure.
Regionally, the United States, Germany, Australia, Indonesia, Brazil, and Singapore ranked as central hubs for ClickFix domains, reflecting underlying trends of affordable hosting, data center concentration, and, in some cases, regional ISP targeting.
Interestingly, Indonesia and Brazil contributed an outsized share of non-Cloudflare infrastructure, hinting at the popularity of regional providers in these campaigns.
A remarkable finding was that 76.3% of ClickFix infrastructure overlapped with known Adversary-in-the-Middle (AiTM) datasets, highlighting widespread re-use of compromised or rented adversarial infrastructure across multiple cybercrime operations.
Analysis also discovered ClickFix campaigns abusing legitimate or institutional domains, including academic (.edu, .ac) and government (.gov, .mil) resources, likely due to opportunistic compromises or poorly maintained DNS records.
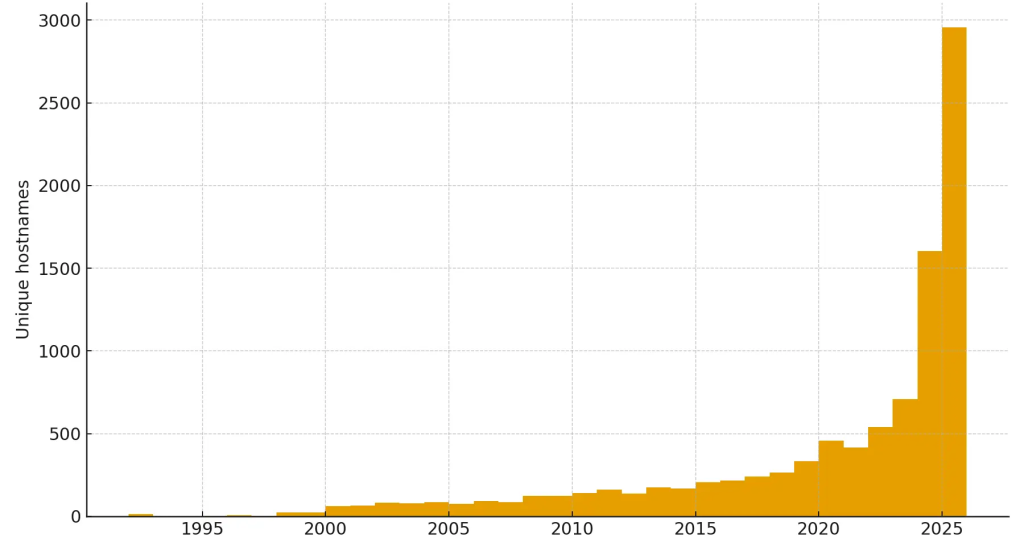
Namecheap surfaced as the registrar of choice for domain purchases, including those shielded by Cloudflare.
The ClickFix dataset, compiled over 2.5 months, exposes the shifting landscape of phishing infrastructure, technique re-use, and the ongoing exploitation of global hosting resources.
Technical indicators point to the need for continued monitoring and multi-source validation before usage in defensive blocklists.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
