Unit 42 researchers have identified a sophisticated Windows-based malware family, Airstalk, that exploits legitimate mobile device management APIs to establish covert command-and-control channels.
The malware exists in both PowerShell and .NET variants, with evidence suggesting a nation-state actor may have employed it in supply chain attacks. Palo Alto Networks has designated the associated threat activity cluster as CL-STA-1009.
Airstalk represents a novel approach to maintaining persistent access by weaponizing VMware’s AirWatch API, now known as Workspace ONE Unified Endpoint Management.
The malware abuses the custom device attributes feature and file upload capabilities to create a dead-drop mechanism for bidirectional communication with threat actors.
This technique allows the backdoor to blend seamlessly into legitimate MDM traffic, evading traditional security controls that typically scrutinize suspicious network behavior.
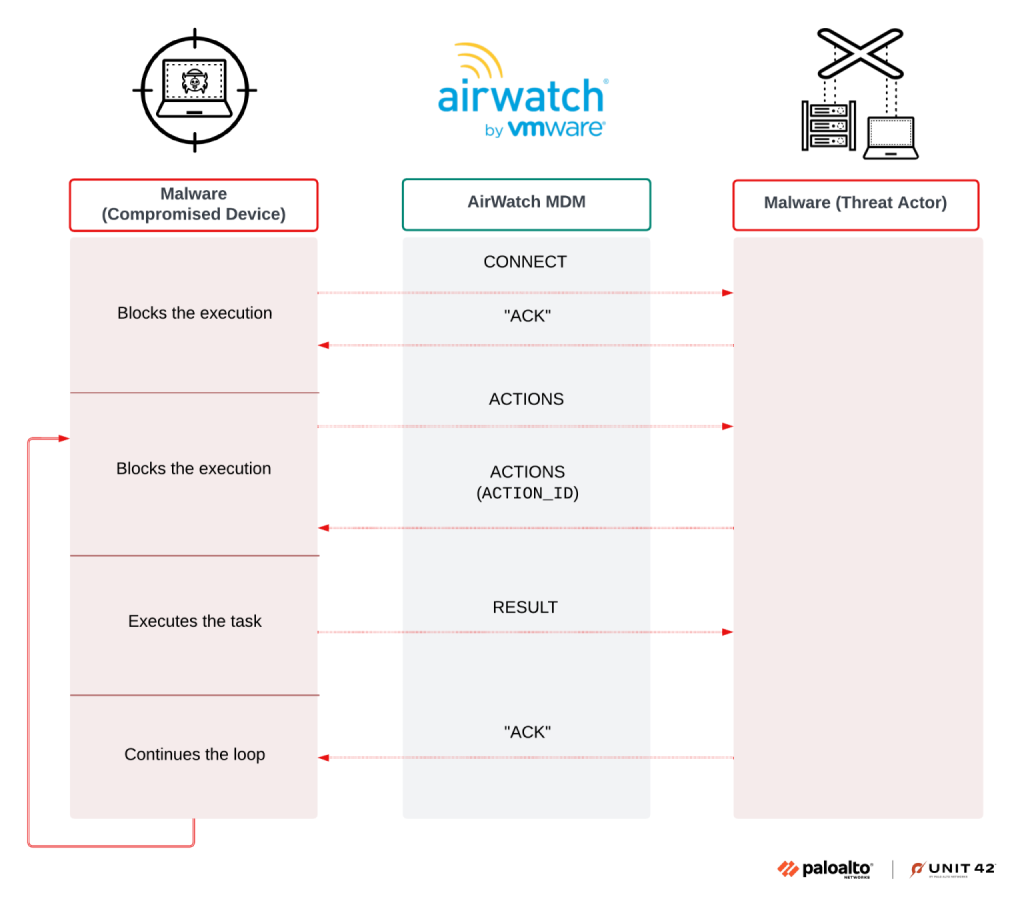
The PowerShell variant establishes C2 communication through JSON-formatted messages transmitted via the AirWatch devices endpoint.
Each message contains a client UUID derived from Windows Management Instrumentation, along with Base64-encoded serialized data specifying message types such as CONNECT, CONNECTED, ACTIONS, and RESULT.
The protocol employs a synchronization mechanism in which the malware sends connection requests and blocks execution while awaiting the attacker’s responses, ensuring reliable command delivery across multiple threads.
The .NET variant demonstrates more advanced development with enhanced capabilities targeting multiple browsers, including Chrome, Microsoft Edge, and Island Browser.
This iteration introduces additional delivery type suffixes (DEBUG, RESULT, and BASE) and implements separate execution threads for task management, debug log exfiltration, and periodic beaconing to C2 infrastructure every ten minutes.
The .NET variant implements versioning, with samples found in versions 13 and 14, indicating active development and iteration.
Both variants can execute sensitive data theft operations including screenshot capture, cookie exfiltration through Chrome remote debugging, browsing history extraction, and file enumeration.
Notably, developers left unimplemented task identifiers within the code, suggesting modular functionality reserved for future activation or deliberate obfuscation of capabilities. Defense evasion mechanisms prove particularly concerning.
The .NET variant samples carry code signatures from what researchers assess as a likely stolen certificate issued to Aoteng Industrial Automation in Langfang, China, which was revoked approximately 10 minutes after issuance on June 28, 2024.
Threat actors modified internal timestamps on later binary samples while preserving signed timestamps, allowing researchers to establish a development timeline spanning from June through November 2024.
The malware demonstrates targeted attacks against business process outsourcing organizations and supply chain partners.
Stolen browser session cookies could grant access to victim clients’ systems, while compromised screenshots and keystrokes expose proprietary information affecting both the direct target and downstream customers.
The PowerShell variant maintains persistence through scheduled tasks, whereas the .NET variant relies on behavioral stealth.
Palo Alto Networks’ Advanced WildFire, Cortex XDR, and XSIAM platforms have been updated with detections and behavioral threat protection to counter Airstalk variants. Organizations suspecting compromise should contact Unit 42’s incident response team immediately for forensic analysis and containment procedures.
| IoC | Type | Description |
| 0c444624af1c9cce6532a6f88786840ebce6ed3df9ed570ac75e07e30b0c0bde | SHA256 | Signed test sample |
| 1f8f494cc75344841e77d843ef53f8c5f1beaa2f464bcbe6f0aacf2a0757c8b5 | SHA256 | Signed test sample |
| dfdc27d81a6a21384d6dba7dcdc4c7f9348cf1bdc6df7521b886108b71b41533 | SHA256 | Airstalk .NET sample |
| b6d37334034cd699a53df3e0bcac5bbdf32d52b4fa4944e44488bd2024ad719b | SHA256 | Airstalk .NET sample |
| 4e4cbaed015dfbda3c368ca4442cd77a0a2d5e65999cd6886798495f2c29fcd5 | SHA256 | Airstalk .NET sample |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
