A sophisticated SEO poisoning campaign, Operation Rewrite, utilizes a malicious IIS module called BadIIS to hijack legitimate web servers and redirect unsuspecting visitors to scam and malware sites.
First observed in March 2025, this activity, tracked as CL-UNK-1037, displays Chinese-language code artifacts and infrastructure overlaps with the “Group 9” cluster, leading analysts to attribute the operation to a Chinese-speaking threat actor with high confidence.
Additionally, the campaign’s tactics and toolkit share notable similarities with Cisco Talos’s “DragonRank” SEO poisoning attacks.
The campaign follows a two-phase approach. In the poisoning phase, BadIIS intercepts requests from search engine crawlers identified by matching User-Agent headers against a list of keywords, including Google, Bing, Yahoo, Cốc Cốc, and Timkhap, and fetches keyword-stuffed HTML from a Command and Control (C2) server.
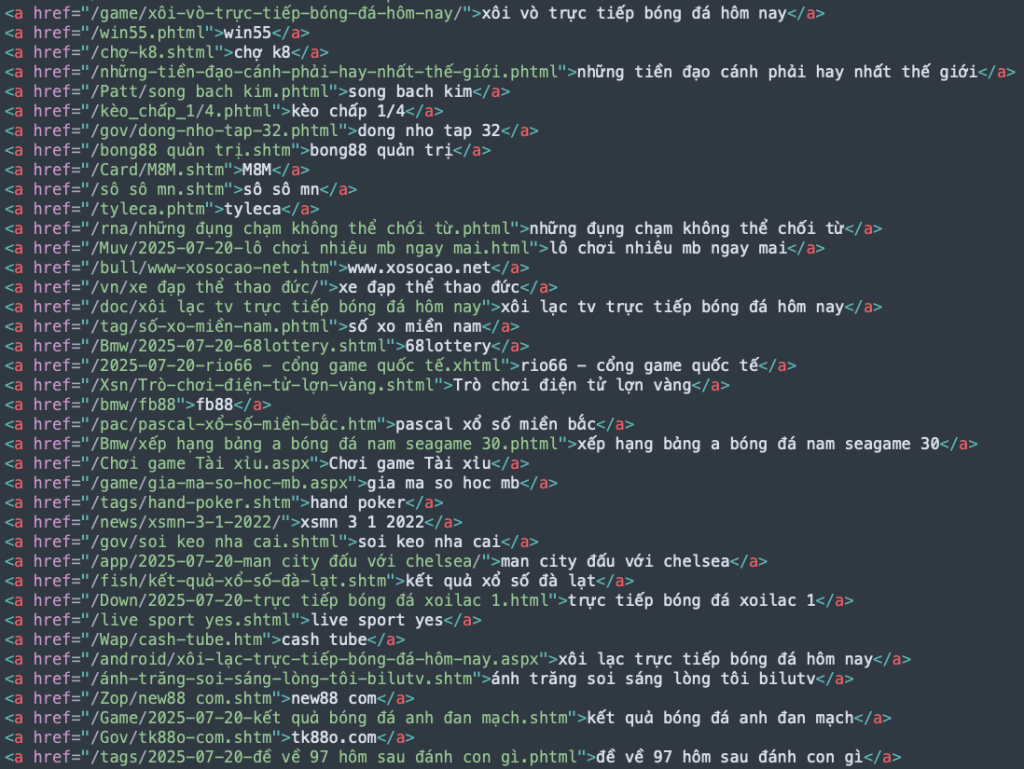
This malicious content is served only to crawlers, causing search engines to index the compromised domain for popular queries. In the redirection phase, when real users arrive via a search engine referrer, BadIIS proxies a redirect to attacker-controlled sites hosting scams or malware.
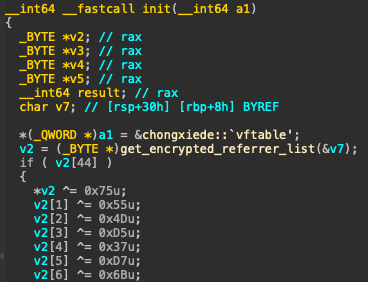
Beyond the native IIS implant, whose RegisterModule function initializes a Pinyin-named chongxiede (“rewrite”) object and decrypts its configuration. Operation Rewrite features three additional variants:
- An ASP.NET handler embedding poisoning logic in its
Page_Loadevent to cloak malicious payloads based on the HTTP_REFERER. - A managed C# IIS module that intercepts 404 errors for scam page injection and dynamically implants spam links on valid pages.
- An all-in-one PHP script that generates fake XML sitemaps for Googlebot and rewrites HTML templates with embedded keywords, while redirecting mobile search visitors to betting sites.
Investigators uncovered C2 domains. 404.008php[.]com, 404.yyphw[.]com, 404.300bt[.]com mirroring Group 9’s known infrastructure (qp.008php[.]com, fcp.yyphw[.]com, sc.300bt[.]com) and sharing core code patterns such as OnBeginRequest and OnSendResponse hooks.
Though no direct domain overlaps link Operation Rewrite to DragonRank, both campaigns exhibit recurring “zz” URI patterns and leverage similar SEO proxy mechanisms.
To detect and mitigate BadIIS implants, security teams should audit IIS module lists for unusual DLLs, monitor outbound connections to the identified C2 domains, and look for web shell activity, particularly ZIP archives placed in web-accessible paths and scheduled lateral movement tasks.
Palo Alto Networks users can leverage Advanced WildFire, Advanced URL Filtering, Advanced DNS Security, and Cortex XDR to block malicious payloads, disrupt C2 communications, and alert on anomalous proxy behavior.
Continuous IIS server validation, crawler response analysis, and tailored threat-hunting rules based on the campaign’s unique configuration markers will strengthen defenses against Operation Rewrite and similar SEO poisoning threats.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
