Researchers have identified a surge in sophisticated supply chain tactics by the North Korea–linked WaterPlum group, specifically its Cluster B (also known as BlockNovas), which has broadened the distribution of its novel OtterCandy malware through the ClickFake Interview campaign in Japan and beyond.
Previous campaigns under WaterPlum, including Contagious Interview and earlier iterations of ClickFake Interview, relied primarily on the GolangGhost backdoor and the macOS-focused FrostyFerret implant.
Since July 2025, however, Cluster B has pivoted to a cross-platform Node.js–based RAT and information stealer called OtterCandy, marking a significant escalation in both capabilities and targeting.
OtterCandy merges features from two earlier WaterPlum tools, RATatouille and OtterCookie. The malware initiates by launching a Node.js runtime and connecting to its command-and-control (C2) server via Socket.IO, establishing an interactive channel that supports a suite of data-exfiltration and remote-control commands.
Upon connection, OtterCandy transmits a JSON payload containing initial system identifiers. In version 1 (v1), this included only a “username” field for rudimentary tracking. Version 2 (v2), released in late August 2025, enhances attribution by adding a “client_id” field to distinguish victims more reliably across sessions.
OtterCandy achieves persistence through two mechanisms. First, it relies on a precursor loader named DiggingBeaver, which plants registry entries or launch-agent files on Windows, macOS, and Linux.
Second, the malware itself listens for the SIGINT event via Node.js’s process.on('SIGINT', …) handler.
When triggered, OtterCandy respawns its primary process, ensuring resilience against basic termination attempts.
In v2, the malware extends its stealth by integrating a new ss_del A command that not only clears registry keys responsible for persistence but also removes associated files and directories, minimizing forensic artifacts.
A core functionality of OtterCandy is the exfiltration of browser credentials, cryptocurrency wallet files, and arbitrary user documents.
In v1, four hardcoded browser extension IDs were targeted; v2 expands this list to seven, capturing a broader range of extensions popular in enterprise and consumer environments. Additionally, v1’s Chromium-based browser stealer sent only partial credential sets.
Under v2, the stealer now harvests complete profile data, including saved passwords, cookies, autofill entries, and browsing history, before packaging files in a ZIP archive for transmission.
The adoption of OtterCandy by Cluster B underscores a shift toward modular, language-agnostic malware that can be rapidly updated and deployed across operating systems.
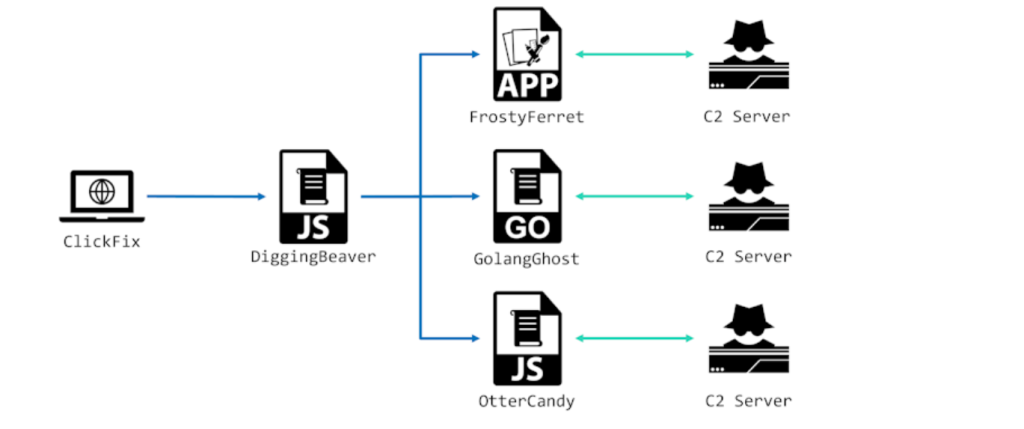
Its use within the well-established ClickFake Interview framework leverages social engineering and recruitment themes to lure victims into executing the malware.
Organizations operating in Japan and other targeted regions should reinforce endpoint detection rules for Node.js processes originating from nonstandard paths, monitor Socket.IO traffic anomalies, and audit recent registry or launch-agent modifications indicative of DiggingBeaver activity.
Patching and removing leftover artifacts via the ss_del routine can thwart v2’s cleanup efforts and aid in forensic analysis.
Continuous monitoring of WaterPlum’s evolving toolset is imperative, as Cluster B demonstrates both shared resource utilization and independent development of advanced data-stealing capabilities.
The emergence of OtterCandy as a primary payload marks a critical inflection point in DPRK threat actor operations, warranting heightened vigilance across supply chain and endpoint security controls.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
