A recent investigation by NVISO has uncovered a new wave in the ongoing “Contagious Interview” campaign, linked to DPRK‑aligned threat actors, that leverages legitimate JSON storage services such as JSON Keeper, JSONsilo, and npoint.io to deliver malware from trojanized code repositories.
The campaign, traced back to at least 2023, continues to target software developers, particularly in cryptocurrency and Web3 sectors, under the guise of fake technical interviews.
The operation begins when fake recruiters approach developers on professional platforms like LinkedIn, posing as representatives of tech or other industries.
The victim is persuaded to download a so‑called “demo” project from GitLab or GitHub, allegedly part of an interview test. Upon inspection, these demo repositories appear functional, often representing real‑estate or Web3 applications built using Node.js.
Hidden in these repositories is a configuration file, typically stored at server/config/.config.env. This file contains a base64‑encoded variable masked as an API key. However, once decoded, it reveals a URL hosted on one of the abused JSON storage platforms.
The retrieved JSON actually contains obfuscated JavaScript, which the Node.js application automatically imports and executes as a legitimate library call.
This obfuscated script ultimately leads to the download of BeaverTail, an infostealer that collects browser data, cryptocurrency wallet credentials, keychain files, and other sensitive documents before delivering the next‑stage payload.
The second‑stage malware, InvisibleFerret, is a Python‑based modular RAT previously detailed by Palo Alto Networks. NVISO analysis confirms it now includes new functionality to fetch components from Pastebin.
The module internally referenced as “pow” decodes up to 1,000 Pastebin URLs encrypted with an XOR key (“!!!HappyPenguin1950!!!”), further transforming and validating them through RSA signatures before downloading additional payloads.
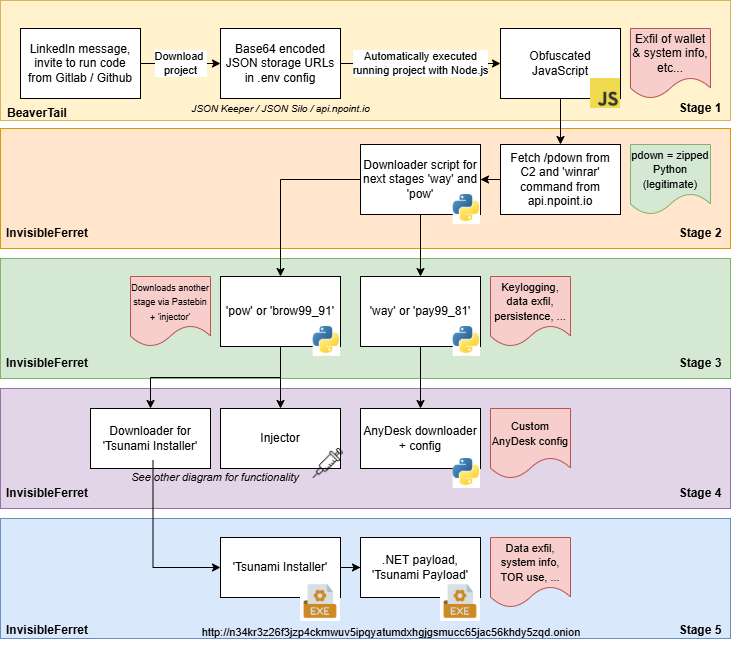
One of these payloads, named Tsunami, performs extensive system fingerprinting, adds Windows Defender exclusions, and creates scheduled tasks for persistence.
A variant observed on VirusTotal also integrated a TOR client to contact a hard‑coded .onion command‑and‑control domain, though the server was offline at the time of analysis.
NVISO identified that the actors used multiple layers of legitimate infrastructure, including JSON storage APIs, GitLab repositories, and the Railway platform, to conceal payload transfers. Representatives of the abused services have been notified and are actively removing malicious data.
The report reinforces earlier warnings: developers should never execute code provided during unsolicited interviews without sandbox inspection, and should treat configuration variables and embedded URLs as potential infection vectors.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
