MSIX emerged as the next-generation standard for Windows app packaging, boasting containerization, trust through digital signatures, and robust support for both modern and traditional applications.
Yet this very combination of flexibility, virtualization, and automation has laid the groundwork for a new wave of malware delivery operations targeting enterprise environments.
What was once an innovation in secure deployment has now been systematically weaponized, turning the MSIX ecosystem into a hunting ground for persistent, evasive attacks.
Over the past year, MSIX’s technical advantages have been exploited by threat actors running Loader-as-a-Service (LaaS) operations.
These commercialized criminal services offer MSIX-packaged droppers on a subscription basis, complete with developer-signed certificates and obfuscated installer payloads.

Attackers leverage MSIX’s code-signing model and support for legacy Win32 and script-based payloads to distribute sophisticated downloaders and ransomware.
The threat doesn’t end with traditional phishing; malvertising campaigns now seed Google search results with sponsored links to cloned software sites.
Victims seeking popular applications such as Chrome, Teams, or Zoom are tricked into downloading malicious MSIX packages that display all the signs of legitimacy, from polished assets to valid signatures.
Social engineering has also migrated into corporate channels, with attackers sending convincing SharePoint or Teams notifications that lead users to install weaponized packages under the guise of workplace productivity.
The technical structure of MSIX packages enables adversaries to evade security controls at multiple layers.
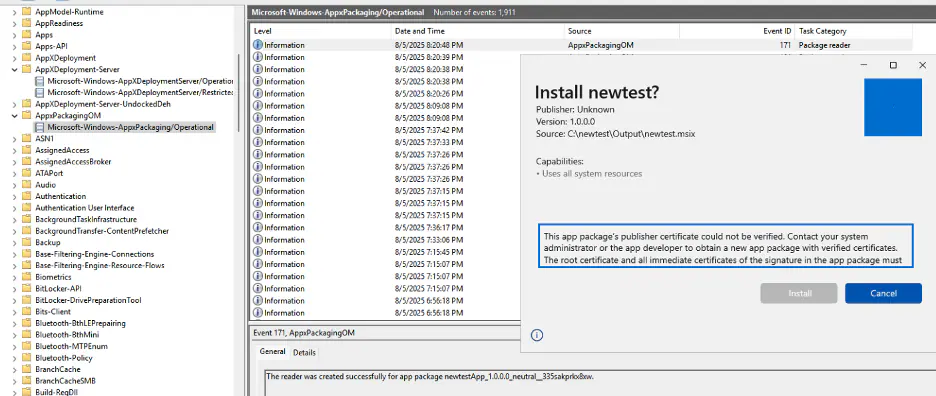
MSIX enforces a stringent manifest and signature validation process, but premium loader kits now use developer-signed certificates that are trusted by Windows but not widely flagged by security tools.
Once launched, malicious packages leverage capabilities such as runFullTrust and Package Support Framework scripting to invoke PowerShell or DLL stagers straight from virtualized file system paths.
This approach obscures visibility into process creation and lateral execution, bypassing endpoint agent controls that depend on traditional MSI or EXE process tracing.
File operations are redirected to isolated container spaces, complicating forensic investigations and allowing malware to persist after deployment cleanup routines.
The result is a new breed of persistent malware, capable of establishing execution footholds within the boundaries of what appears to be a standard, well-formed app.
Defending against the MSIX threat requires new detection paradigms and safe, controlled testing environments. Manual creation of realistic attacker packages is time-consuming and hazardous, so the security community has responded with automation.
Splunk’s MSIXBuilder utility abstracts the complexity of building, signing, and deploying test packages, enabling defenders to rapidly simulate real-world MSIX-based attacks without exposing networks to live malware.
On the detection side, attention has shifted to in-depth Windows event log analysis. Key log sources, such as AppXDeploymentServer, AppXPackaging, and process creation events, can reveal early signs of unsigned, developer-signed, or full-trust package installations and script executions from virtualized directories.
Correlating these observables across the deployment lifecycle is essential to distinguish benign activity from covert loader operations, helping organizations close the gap between adversary innovation and defender response.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
