Researchers at Forcepoint X-Labs have discovered a phishing campaign using Phorpiex malware to deliver Global Group ransomware. The attack uses deceptive Windows shortcut files (.lnk) and a unique ‘mute’ mode to encrypt data offline and evade traditional security detection.
A major new security report has alerted the public to a massive global email scam designed to hijack computers and lock away personal files. Researchers at Forcepoint X-Labs, led by Senior Security Researcher Lydia McElligott, have discovered that a long-running hacker network known as Phorpiex, active since roughly 2010, is now being used to spread a nasty type of virus called Global Group ransomware.
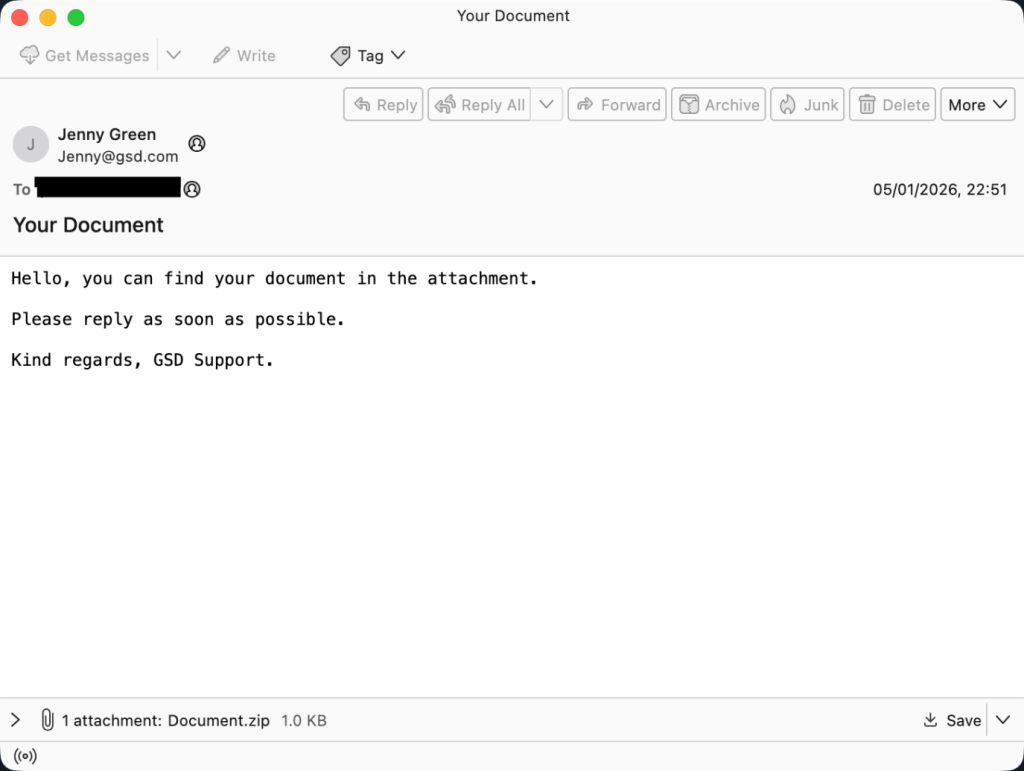
This campaign, active throughout 2024 and 2025, starts with a plain email. The subject line usually reads “Your Document,” a phrase designed to make you curious or worried enough to click. Inside is an attachment or a Zip folder, often named Document.doc.lnk. Hackers use a double extension here because Windows often hides the last part of a file name. To a normal person, it just looks like Document.doc, but further probing revealed it is actually a Windows Shortcut file (.lnk).
Once clicked, the shortcut quietly tells your computer to run background commands using a method called Living off the Land (LotL). Instead of bringing its own suspicious tools, it hijacks your computer’s “healthy” programs, like PowerShell and Command Prompt, to do its dirty work. These commands download the actual virus, which hides in system folders under names like windrv.exe to look like a legitimate Windows part.
The research, shared with Hackread.com, identifies the final payload as Global Group, a successor to the older Mamona ransomware. What makes this version troublesome is its “mute” mode. Unlike most viruses that “call home” to the internet for instructions, Global Group does everything locally.
“The ransomware does not retrieve an external encryption key; instead, it generates the key on the host machine itself,” researchers noted in the blog post published today.
Because it doesn’t need a server connection, it can lock files even on offline computers. Further investigation revealed it uses a strong locking system called ChaCha20-Poly1305, making it nearly impossible to recover files without the criminal’s digital key.
This virus is a “clean” criminal. To hinder investigators, it uses a ping command to the address 127.0.0.7 as a three-second timer. Once finished, it deletes its own files from your hard drive to leave less evidence behind.
Researchers found that the virus even hunts for your backups. It quietly deletes Volume Shadow Copies, the “safety net” files used to restore data. Once finished, your documents will have a .Reco extension, and your wallpaper will be replaced with a ransom note.
This campaign shows that hackers don’t always need complex technology to trap users; sometimes, they just need a simple shortcut and a convincing email. Using common sense is key. Do not open unsolicited emails, click links they contain, or download and run any attached files.