This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for “Risky Business” in your podcatcher or subscribing via this RSS feed.
A Ukrainian man who developed and managed the IcedID malware botnet faked his own death in an attempt to escape the FBI and jail time in the US.
The unnamed suspect bribed Ukrainian cops to falsify a dead man’s documents and issue a death certificate in his name.
This happened in April 2024, a month before Europol and the FBI seized IcedID servers during Operation Endgame—suggesting there was either a leak in the investigation or that the suspect saw law enforcement agencies probing his servers.
According to court documents, the suspect appears to have been one of the top individuals inside the IcedID malware operation.
Despite faking his own death, the suspect continued to live at his normal residence in Uzhhorod, a Ukrainian city near the border with Slovakia, so not the smartest tool in the shed when it comes to OpSec.
He was finally arrested in December of last year. During a search of his home, he tried to pass as another person and even showed fake documents in the new name.
Ukrainian officials have now seized apartments, parking spaces, and cars that the suspect passed on to his mother, ex-wife, and her parents after his (fake) death.
The judge imposed a bail of UAH 400 million ($9.3 million), deeming him a flight risk.
Shortly after his arrest, a second IcedID developer was also arrested in Kyiv. Ukrainian court documents reveal the two were part of a larger group of IcedID developer, calling themselves the Digital 8.
The court documents mention that this second suspect has “a wide circle of acquaintances among law enforcement officers and the criminal community.”
Just like the first suspect, he was deemed a flight risk and his bail was also set at an astronomical level for Ukraine, at UAH 382.7 million ($8.9 million).
[h/t S.S., J.F., & A.C.]
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Leaked password exposed 200 airports: CloudSEK says it intercepted the leaked credentials of a tech support and maintenance company that had access to the IT networks of more than 200 airports. The account also didn’t have MFA enabled.
Odido breach: Dutch telecommunications provider Odido has fallen victim to a cyberattack. The company says hackers breached its customer contact system and harvested customer data. According to Dutch public broadcaster NOS, more than 6.2 million customers are affected. Odido says sensitive data like invoices, passwords, call records, and location data was not involved.
South Korea fines fashion brands over data breaches: South Korea’s data privacy agency has fined three fashion and luxury brands 36 billion won ($25 million) for data breaches last year. The fines applied to the South Korean branches of Christian Dior, Louis Vuitton, and Tiffany’s. The three collectively exposed the personal data of 5.5 million customers.
South Korea accuses Coupang of not saving logs: South Korean authorities have accused the country’s largest online retailer of failing to preserve logs related to a major security breach last year. The incident has exposed the personal details of more than 33 million South Koreans and has now led to a major government investigation. Coupang has been under fire for months after its executives have dodged a parliamentary inquiry and had refused to cooperate with officials. Instead, the company’s American owners have sued the Seoul government accusing it of unfair treatment. The lawsuit started with two investors and has expanded this week with three more.
Asahi recovers after ransomware attack: Japanese beer maker Asahi says its sales are now at regular levels following a ransomware attack that disrupted production and distribution last November. [NHK]
General tech and privacy
Linux Mint planning a slowdown: The developers of the Linux Mint distro are preparing to slow down their release cycle after publishing new versions every six months for almost a decade now. [Nerds.xyz]
Google releases nudes remover: Google launched a new tool this week to let users remove their nude images from search results.
Windows 11 26H1 update: This year’s spring version of Windows 11, aka the 26H1 release, will be a “scoped” release. Microsoft says the new version will only be available to new devices that ship with new specialised silicon chips. Most enterprise devices will continue to run 25H2 until the fall update.
Chrome 145: Google has released version 145 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change in this release is the formal launch of Device Bound Session Credentials, a feature that tries to prevent infostealers from taking your cookies. This feature allows websites to bind a user’s session to their device and make it harder for stolen session cookies to be used from other systems.
AGs rally behind Senate version of KOSA: A coalition of 40 US Attorneys General have urged Congress to pass the Senate version of the Kids Online Safety Act (KOSA). The AGs say the version of KOSA proposed by the US House of Representatives contains language that undermines state child protection laws. It would also limit states from addressing online harms to children.
Disney settles privacy lawsuit: Disney has agreed to pay $2.75 million to the state of California for failing to honor its consumers’ data opt-out requests, which violated the California Consumer Privacy Act (CCPA).
Government, politics, and policy
Iran targets private Gmail accounts of Israeli officials: Iranian hackers are trying to breach the personal Google accounts of Israeli officials. Attacks have spiked since Israel’s 12-day war with Iran last June. Hundreds of attacks were detected, targeting government and defense officials, academics, and journalists. Israel’s Shin Bet security agency and National Cyber Directorate say the attackers are using highly tailored approaches that are hard to spot. [The Times of Israel]
More social media bans for kids: The governments of Kazakhstan, Moldova, and Romania are considering joining the wave of countries who are considering a ban for kids under the age of 16 from registering on social media networks.
NSA might get a new lead, finally: The White House’s proposal for the next leader of NSA and CyberCommand, Army Lt. Gen. Joshua Rudd, has passed the Senate Intelligence Committee and his nomination is now on the Senate floor. [The Record]
US suspends Chinese tech bans: The US government has shelved a series of bans on Chinese technologies ahead of its talks with Beijing, probably as a sign of good will. This includes bans on China Telecom, TP-Link, China Unicom, China Mobile, and more. We’ll see if this stands. [Reuters]
New CIRCIA feedback: CISA is looking for additional feedback on the implementation of the 2022 Cyber Incident Reporting for Critical Infrastructure Act, aka CIRCIA. [CybersecurityDive]
CISA year in review: CISA published its yearly report, and the agency says it conducted 148 cyber and physical security exercises and triaged more than 30,000 cyber incidents last year.
CISA forceful transfers: Speaking in a Senate hearing, CISA acting director Madhu Gottumukkala said the agency reassigned 70 CISA employees to other DHS offices last year. He faced questions over the forced reassignments after forced transfer orders were used to pressure senior employees to quit and because some employees were forced to help immigration and border patrol forces, outside CISA’s cybersecurity tenet. [NextGov]
Switzerland ends Palantir contract: The Swiss government has ended its contract with American analytics company Palantir. Officials concluded that the platform posed a national security risk. A review carried out by the Swiss Armed Forces found that there was a significant likelihood that the US government would be able to access Swiss confidential data. [NewsCase]
Dutch Parliament says “no US tech”: The lower house of the Dutch parliament has instructed the Dutch government to keep the DigiD national ID service away from the US. The DigiD service is hosted on Solvinity, a cloud provider that was recently acquired by an American company. Dutch officials want the government to move DigiD to the servers of another Dutch or European provider. [NLTimes]
Russia blocks YouTube and Meta sites: Russia’s internet watchdog has blocked access to YouTube, Facebook, WhatsApp, and Instagram. The Roskomnadzor has removed domain names for the four platforms from Russia’s national domain name system. The agency was previously throttling traffic to YouTube and WhatsApp sites since July last year. The Russian government designated Meta an “extremist” organization after the company refused to censor content related to the Ukrainian war. The Roskomnadzor also blocked access to the Tor Project, Windscribe VPN, APK Mirror, the BBC, and several other news sites. [Kommersant]
In this Risky Business sponsor interview, Tom Uren talks to Trail of Bits CEO Dan Guido about how Trail of Bits is reworking its business processes to take advantage of AI. Dan talks about what it takes to make AI agents reliable and trustworthy and how that will give the company an edge by making its work both better and faster.
Arrests, cybercrime, and threat intel
Ukraine arrests hospital hackers: Ukraine’s cyber police detained two men who tried to steal government funds from a local hospital. The two allegedly hacked the PC of the hospital’s accountant. They then transferred more than $115,000 from the hospital’s budget to their own company’s accounts.

Phishing gang detained: Ukraine’s cyber police have also dismantled a phishing group targeting locals with smishing messages.
Ukraine dismantles scam call center: They also dismantled a call center engaging in bank and tax scams, also targeting Ukrainians.
Phobos affiliate trial begins in France: The trial of Ilia D., a prolific affiliate for the Phobos ransomware, has begun in Paris. His partner is also on trial for helping him launder the ransom payments. The couple were arrested in Milan, Italy, in August 2023. [ZDNet France]
US seeks 9 years for Trenchant leaker: US prosecutors are seeking a nine-year prison sentence for a Trenchant executive who sold zero-day exploits to foreign adversaries. Australian national Peter Williams made $1.3 million from selling eight of his employer’s exploits to a Russian company. Prosecutors are seeking a nine-year prison sentence as much as the time he spent with the company. They are also seeking $35 million in restitution, a fine of $250,000, and three years of supervised release. [TechCrunch]
Most networks run vulnerable versions of WinRAR: Security firm Stairwell says that around 80% of the IT networks it monitors run versions of WinRAR vulnerable to CVE-2025-8088, a vulnerability that has been widely exploited by cybercrime and cyber-espionage groups.
GeoServer attacks on the rise: F5 says it is seeing a spike in scans for vulnerable GeoServer platforms. This includes both old and new bugs.
Paragon leaks Graphite backend: Israeli spyware maker Paragon Solutions has accidentally leaked details of the Graphite spyware control panel. The panel was exposed in photos from a demo day in the Czech Republic. Now-deleted photos revealed Graphite’s ability to extract messages from IM clients such as WhatsApp, Signal, Telegram, Line, Snapchat, TikTok, and more.
The general counsel uploaded a picture on Linkedin showing the web panel of Paragon’s spyware.
The panel shows a phone number in Czechia, Apps, Accounts, media on the phone, the interception status and numbers extracted from social media applications.—Jurre van Bergen (@jurrevanbergen.nl) 2026-02-11T15:29:35.748Z
Pro-Kremlin hacktivist groups target the Olympics: Four of the Russian hacktivist group have taken time out of their busy schedule of harassing random EU pawn shop and city hall websites to launch DDoS attacks against Italian sites linked to the Milano Winter Olympics infrastructure. According to Intel471, the groups include NoName057, BD Anonymous, Z-Pentenst, and Server Killers.
0APT group is fake: Intel471 has joined Guidepoint, Halcyon, and DataBreach.com on calling the 0APT ransom group a fake and fraud. While the other reports looked at the names of the victims, Intel471 looked at the “evidence” the group posted on their dark web leak site.
“Thus far, the threat actor has not provided credible proof of ransomware or data exfiltration attacks as the data samples on the DLS appeared to be fabricated. As the string of alleged victims was revealed, Intel 471 researchers conducted a preliminary review of the DLS metadata and content and found numerous abnormalities. For example, the files that supposedly contained metadata of data stolen from victim networks was unusually large, reaching several terabytes each. Additionally, partial downloads of those files indicated they did not contain any useful data and in fact we observed several instances in which the content contained a repeating pattern of null bytes.”
New Scattered Spider TTPs: Palo Alto Networks has published TTPs from a recent Muddled Libra (aka Scattered Spider, UNC3944) intrusion into a VMware-based environment.
Storm-2603 targets SmarterMail: ReliaQuest looks at Storm-2603’s attacks against SmarterMail servers, which it uses to deploy the Warlock ransomware.
287 Chrome extensions steal browsing histories: A security researcher has discovered 287 Chrome extensions that exfiltrate a user’s browsing history. The extensions have been installed more than 37 million times. They range from ad blockers to AI assistants and office aids.
Malicious Chrome clusters: Security firm LayerX has discovered a cluster of 30 Chrome extensions posing as AI tools that use hidden iframes to run code in their users’ browsers.
First malicious Outlook add-in discovered: Hackers have hijacked the infrastructure of an abandoned Outlook add-in to phish users and steal their Microsoft credentials. More than 4,000 users of the AgreeTo add-in were compromised in the attack. According to Koi Security, the attackers took over an expired Vercel app domain after the developer failed to renew it. The attacker then deployed malicious code on the Vercel domain that prompted the add-in’s users to re-authenticate on a phishing site.
Scam compounds drive surge in human trafficking money laundering: Blockchain analysis company Chainalysis says cryptocurrency flows related to human trafficking activities have surged last year by 85%, mostly driven by cyber scam compounds in Southeast Asia, and carried out via Telegram-based Chinese money laundering services.
Global Telnet traffic drops: Global Telnet traffic has fallen by two-thirds over the past month. According to security firm GreyNoise, the sudden drop started on January 14, around a week before a major Telnet vulnerability was disclosed. Traffic has remained at 35% of previous levels, suggesting a concerted effort by internet service providers to block the outdated protocol.
Malware technical reports
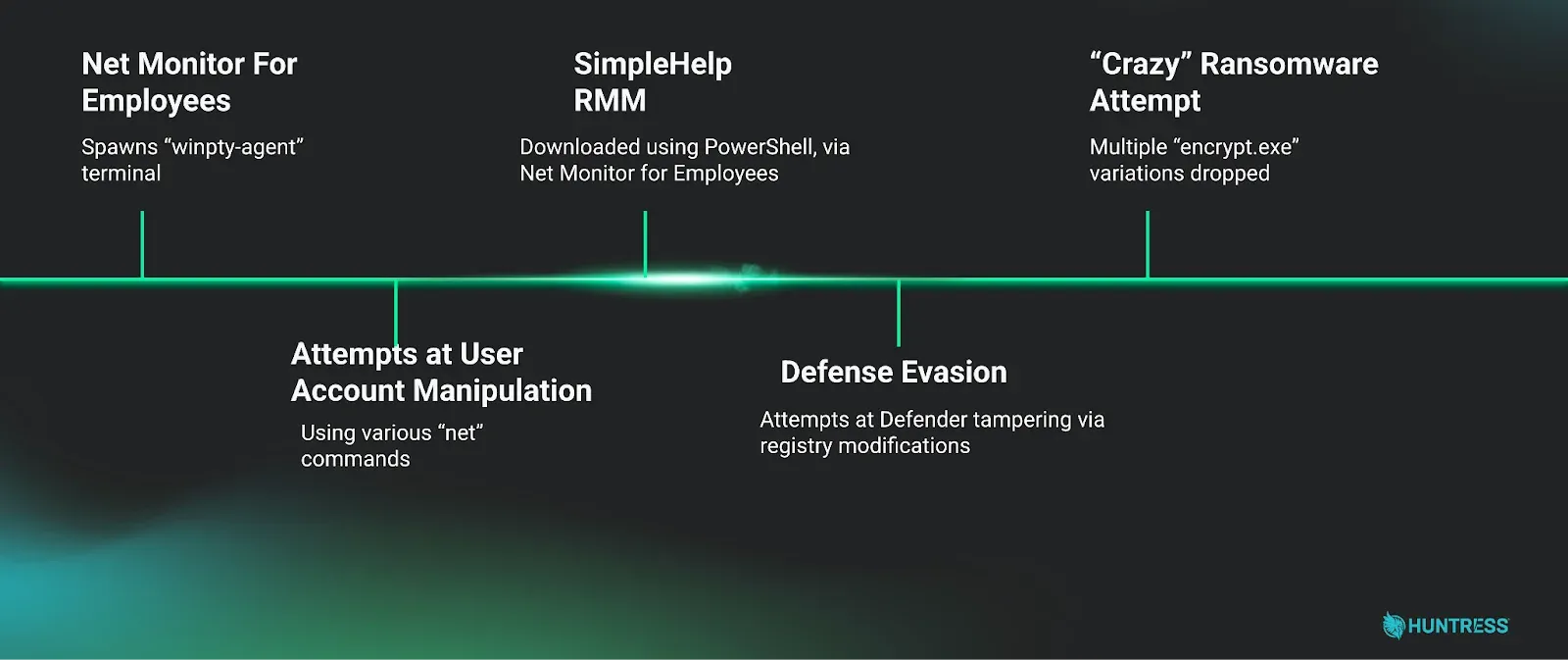
Crazy ransomware: The Crazy ransomware gang has been spotted using an employee monitoring tool named Net Monitor for Employees Professional as a pre-encryption backdoor on compromised networks. [Huntress]
LockBit 5.0 ransomware: Acronis’ security team has published a technical report on the LockBit 5.0 ransomware, which has been trying a comeback for a few months now.
DragonForce ransomware: South Korean threat intel firm S2W looks at the tactics and malware of the DragonForce ransomware operation.
BQTLock & GREENBLOOD: ANY.RUN looks at BQTLock & GREENBLOOD, two new ransomware strains that started operations this year. The latter is the ransomware group that hit Senegal’s government networks last month.
Odyssey Stealer: Censys has tracked down the infrastructure of the Odyssey Stealer malware to 10 servers running its MaaS and C2 infrastructure.
LummaStealer returns: Bitdefender is seeing new LummaStealer campaigns, almost a year after law enforcement took down the service in May of last year.
BRICKSTORM update: CISA has updated its advisory on BRICKSTORM, the backdoor planted on Ivanti devices. The update covers a new version of the backdoor.
UAT-9921 and VoidLink: Cisco Talos looks at UAT-9921, the threat actor behind the new VoidLink AI-generated Linux malware, first documented by Check Point last month.
Netdragon botnet: Chinese security firm QiAnXin has published a technical analysis of Netdragon, a DDoS botnet that has been around since late 2024. QiAnXin looked at the botnet more closely after it infected a bunch of NAS devices running fnOS, a Chinese operating system for NAS devices.
OysterLoader: The Sekoia team has published a technical analysis of OysterLoader, a C++ malware downloader, also known as Broomstick and CleanUp. The malware is often used by the Rhysida ransomware group, but also in infostealer delivery campaigns.
RenEngine: Kaspersky looks at RenEngine, a new malware loader seen in the wild this month.
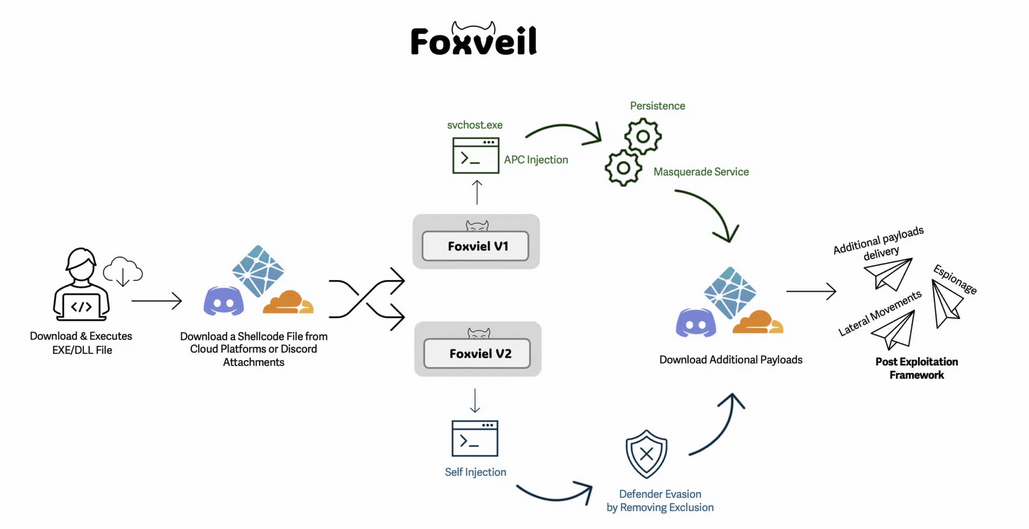
Foxveil: Cato Networks has spotted a new malware loader family. Named Foxveil, this one has been active since last August.
In this Risky Business sponsor interview, Casey Ellis chats with Keith Hoodlet from Trail of Bits. Keith is Trail of Bits’ director of engineering for AI, machine learning and application security and he joined Casey to talk about why prompt injection attack techniques that target AI are an unsolvable problem.
DPRK IT workers: Okta takes a closer look at two North Korean individuals part of a larger network of remote IT workers making money for the regime by applying for jobs at western companies.
Graphalgo campaign: ReversingLabs has spotted another DPRK campaign targeting crypto devs with malware, in this case, a RAT.
France takes down Storm-1516 sites: French authorities have taken down more than 100 websites operated by a Russian disinformation group named Storm-1516. The websites mimicked French local news outlets to attack or boost certain political candidates ahead of the French municipal elections next month. France’s national security directorate said the sites were taken down before they got any visibility. In a report last year, France’s disinformation fighting agency said the Storm-1516 group had reached a mature level of operations and were often achieving notable results. [RTL]
Google says LLMs are now essential to APTs: Google says that LLMs have become essential tools for state-backed cyber operations. The company’s threat intelligence team has spotted groups from China, Russia, Iran, and North Korea operationalize AI towards the end of last year. AI tools were used for “technical research, targeting, and the rapid generation of nuanced phishing lures.” Attackers used Gemini to analyze inboxes, to write code, and automate vulnerability research and reconnaissance. Financially motivated threat actors also experimented with AI tools, but they “have not yet made breakthroughs in developing AI tooling.”
UNC3886: Team Cymru has looked at the ORB network used by UNC3886 in its attacks against Singaporean telcos last year.
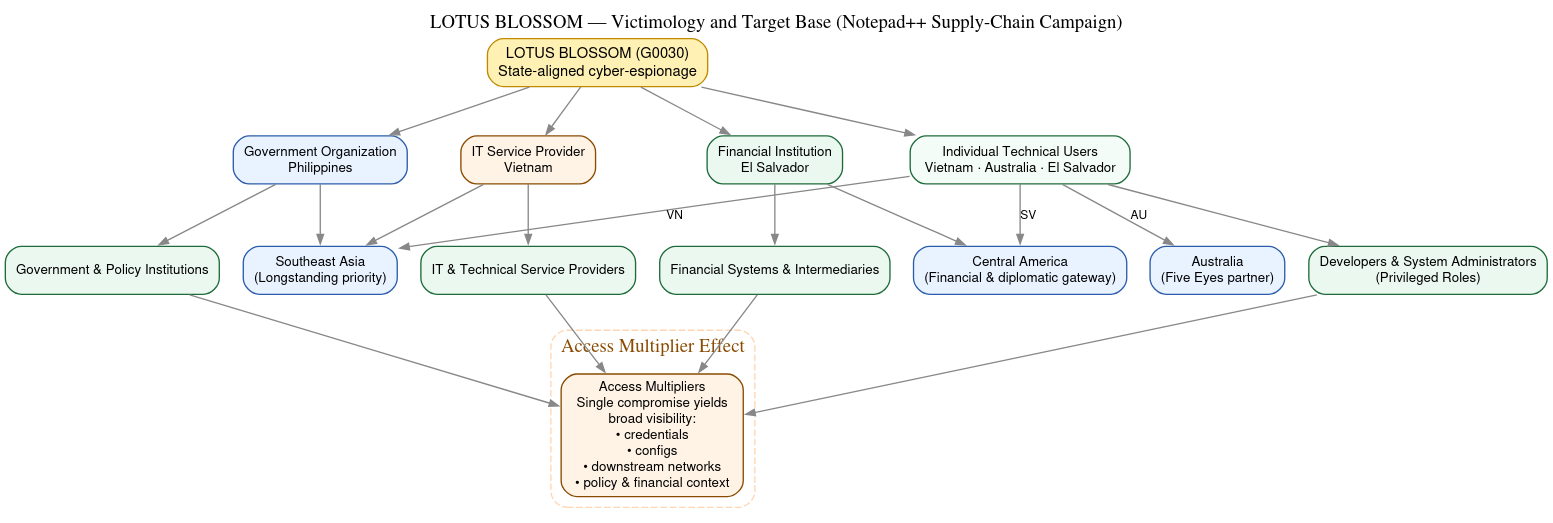
Lotus Blossom (G0030): DomainTools researchers look at the history and infrastructure of Lotus Blossom (G0030), the threat actor behind the recent Notepad++ supply chain attack. Palo Alto Networks also has its own report on the incident.
“The middle era, from approximately 2016 through 2024, marks a period of consolidation and professionalization. During this time, Lotus Blossom transitioned away from Elise and adopted the Sagerunex backdoor family, which would become a defining element of its operations for nearly a decade.”
Apple patches zero-day: Apple has released security updates to patch a zero-day that was used in “an extremely sophisticated attack.” The zero-day was used in targeted attacks against specific users running versions prior iOS 26. The attacks were discovered by the Google security team. The zero-day, tracked as CVE-2026-20700, impacts the dyld component used to link code between libraries. It is one of 37 vulnerabilities patched by Apple on Wednesday.
Age verifier bypass: Two security researchers have found a way to bypass the age verification process used on Discord, Twitch, and Snapchat. The bypass abuses a bug in the design of k-ID, a provider of age verification technology used by the platforms. The technique uses the browser’s developer console to trick the k-ID backend into thinking the user scanned their face and is an adult.
“k-id, the age verification provider discord uses doesn’t store or send your face to the server. instead, it sends a bunch of metadata about your face and general process details. while this is good for your privacy (well, considering some other providers send actual videos of your face to their servers), its also bad for them, because we can just send legitimate looking metadata to their servers and they have no way to tell its not legitimate.”
ILIAS RCEs: The ILIAS learning management platform has patched three vulnerabilities that can allow remote code execution attacks. SRLabs found and has published a write-up on the bugs.
Major WP plugin bug: More than 800,000 WordPress sites will need to be patched for a major unauth file upload bug in the WPvivid Backup plugin.
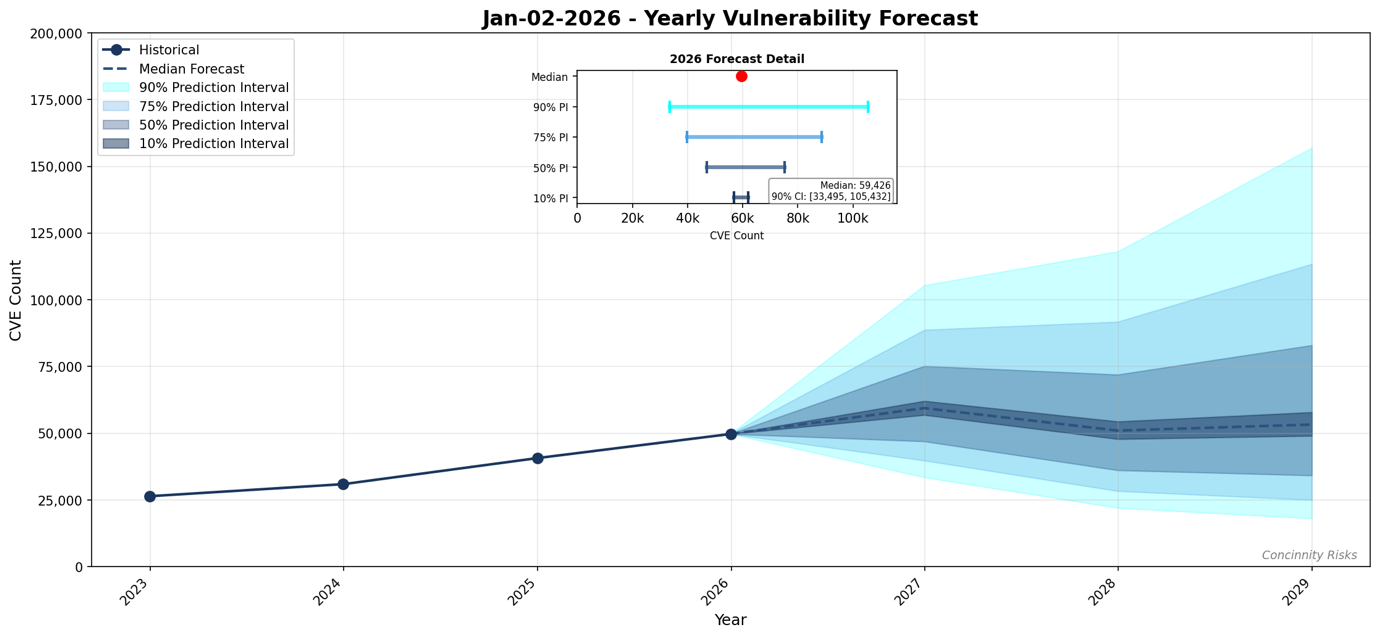
2026 vuln total expected close to 100,000: The Forum of Incident Response and Security Teams (FIRST) estimates that around 60,000 vulnerabilities will be reported throughout the year. This will be the first year on record that global bug reports go over the 50,000 threshold. FIRST says its upper estimates are twice that and that it wouldn’t be surprised if this will be the first year on record with more than 100,000 bugs. [CSO Online]
Infosec industry
Threat/trend reports: Chainalysis, CISA, FIRST, Flashpoint, Food and AG-ISAC, Kaspersky, LeakIX, Recorded Future, and TeamT5 have recently published reports and summaries covering various threats and infosec industry trends.
New tools—Claude Code default cofings: Security firm Trail of Bits and SentinelOne’s Juan Andres Guerrero-Saade have open-sourced their configurations for the Claude Code AI coding assistant.
New tool—BinaryAudit: AI startup Quesma has open-sourced BinaryAudit, an open-source benchmark for evaluating AI agents’ ability to find backdoors hidden in compiled binaries.
New tool—SCAM: 1Password has released SCAM, a new benchmark to teach AI agents how not to get scammed.
New tool—Vulnerability Spoiler Alert: Security researcher Eugene Lim has released Vulnerability Spoiler Alert, a service that monitors open-source repositories and uses Claude AI to detect when commits are patching security vulnerabilities before a CVE is even assigned or an update is released.
New tool—NanoClaw: AI startup Qwibit has released NanoClaw, a lightweight alternative to OpenClaw that runs in Apple containers for security.
Acquisition news: Israeli security giant Check Point is acquiring AI security company Cyata and attack surface management startup Cyclops Security.
Iozzo removed from security conference boards: Vincenzo Iozzo, a hacker mentioned in the Epstein Files, has been removed from the review boards of two cybersecurity conferences, Black Hat and Code Blue. [TechCrunch]
Tianfu Cup 2026: The Chinese government has secretly held another edition of the Tianfu Cup hacking contest. This year’s edition included heavy use of AI to discover new zero-days. It also included a special competitive track for reproducing exploits for already-known vulnerabilities (n-days). Exploits used at the Tianfu Cup have been collected by the Chinese government and later exploited in the wild by the country’s cyber contractors. [Natto Thoughts]
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Microsoft CEO Satya Nadella’s messaging around personnel changes at the top of its security organisation. These signal a focus on selling security products rather than on making secure products.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about why the world is destined to be perpetually insecure.
