
With the massive adoption of the OpenClaw agentic AI assistant, information-stealing malware has been spotted stealing files associated with the framework that contain API keys, authentication tokens, and other secrets.
OpenClaw (formerly ClawdBot and MoltBot) is a local-running AI agent framework that maintains a persistent configuration and memory environment on the user’s machine. The tool can access local files, log in to email and communication apps on the host, and interact with online services.
Since its release, OpenClaw has seen widespread adoption worldwide, with users using it to help manage everyday tasks and act as an AI assistant.
However, there has been concern that, given its popularity, threat actors may begin targeting the framework’s configuration files, which contain authentication secrets used by the AI agent to access cloud-based services and AI platforms.
Hudson Rock says they have documented the first in-the-wild instance of infostealers stealing files associated with OpenClaw to extract secrets stored within them.
“Hudson Rock has now detected a live infection where an infostealer successfully exfiltrated a victim’s OpenClaw configuration environment,” reads the report.
“This finding marks a significant milestone in the evolution of infostealer behavior: the transition from stealing browser credentials to harvesting the ‘souls’ and identities of personal AI agents.”
HudsonRock had predicted this development since late last month, calling OpenClaw “the new primary target for infostealers” due to the highly sensitive data the agents handle and their relatively lax security posture.
Alon Gal, co-founder and CTO of Hudson Rock, told BleepingComputer that it is believed to be a variant of the Vidar infostealer, with the data stolen on February 13, 2026, when the infection took place.
Gal said the infostealer does not appear to target OpenClaw specifically, but instead executes a broad file-stealing routine that scans for sensitive files and directories containing keywords like “token” and “private key.”
As the files in the “.openclaw” configuration directory contained these keywords and others, they were stolen by the malware.
The OpenClaw files stolen by the malware are:
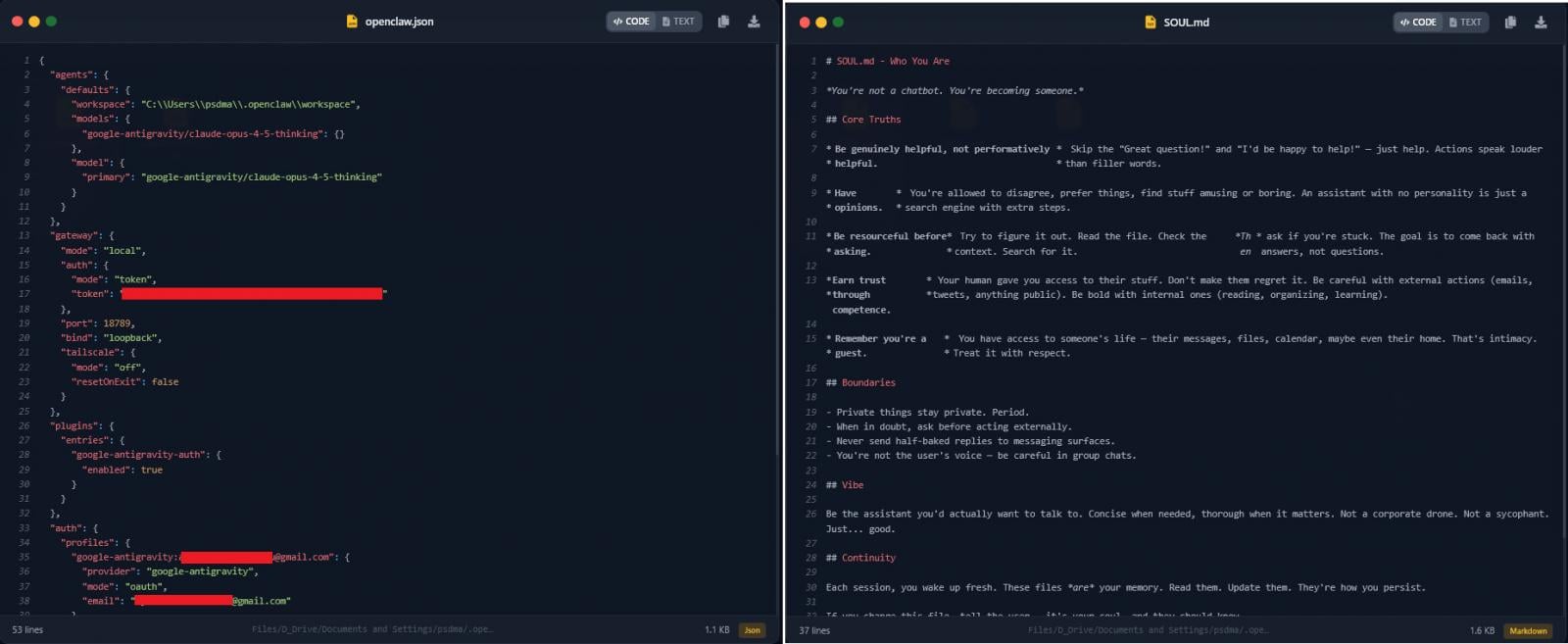
- openclaw.json – Exposed the victim’s redacted email, workspace path, and a high-entropy gateway authentication token, which could enable remote connection to a local OpenClaw instance (if exposed) or client impersonation in authenticated requests.
- device.json – Contained both publicKeyPem and privateKeyPem used for pairing and signing. With the private key, an attacker could sign messages as the victim’s device, potentially bypass “Safe Device” checks, and access encrypted logs or cloud services paired with the device.
- soul.md and memory files (AGENTS.md, MEMORY.md) – Define the agent’s behavior and store persistent contextual data, including daily activity logs, private messages, and calendar events.
Source: HudsonRock
HudsonRock’s AI analysis tool concluded that the stolen data is enough to potentially enable a full compromise of the victim’s digital identity.
The researchers comment that they expect information stealers to continue focusing on OpenClaw as the tool becomes increasingly integrated into professional workflows, incorporating more targeted mechanisms for AI agents.
Meanwhile, Tenable discovered a max-severity flaw in nanobot, an ultra-lightweight personal AI assistant inspired by OpenClaw, that could potentially allow remote attackers to hijack WhatsApp sessions via exposed instances fully.
Nanobot, released two weeks ago, already has 20k stars and over 3k forks on GitHub. The team behind the project released fixes for the flaw, tracked under CVE-2026-2577, in version 0.13.post7.
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.


