A newly named threat actor, TA585, is emerging as one of the most technically self-reliant cybercriminal groups discovered by Proofpoint in 2025.
Unlike other actors in the malware-as-a-service (MaaS) ecosystem that rely on third-party access brokers or traffic delivery networks, TA585 independently manages its entire attack chain from infrastructure and email delivery to malware installation.
At the center of its current campaigns is MonsterV2, a premium malware suite combining the capabilities of a remote access trojan (RAT), stealer, and loader.
First spotted on cybercrime forums in February 2025, MonsterV2 is known for its extensive functionality and steep pricing, with enterprise packages costing up to $2,000 per month.
Proofpoint first linked TA585 to MonsterV2 activity through campaigns in April and May 2025 that showcased the actor’s unique approach to social engineering and content injection.
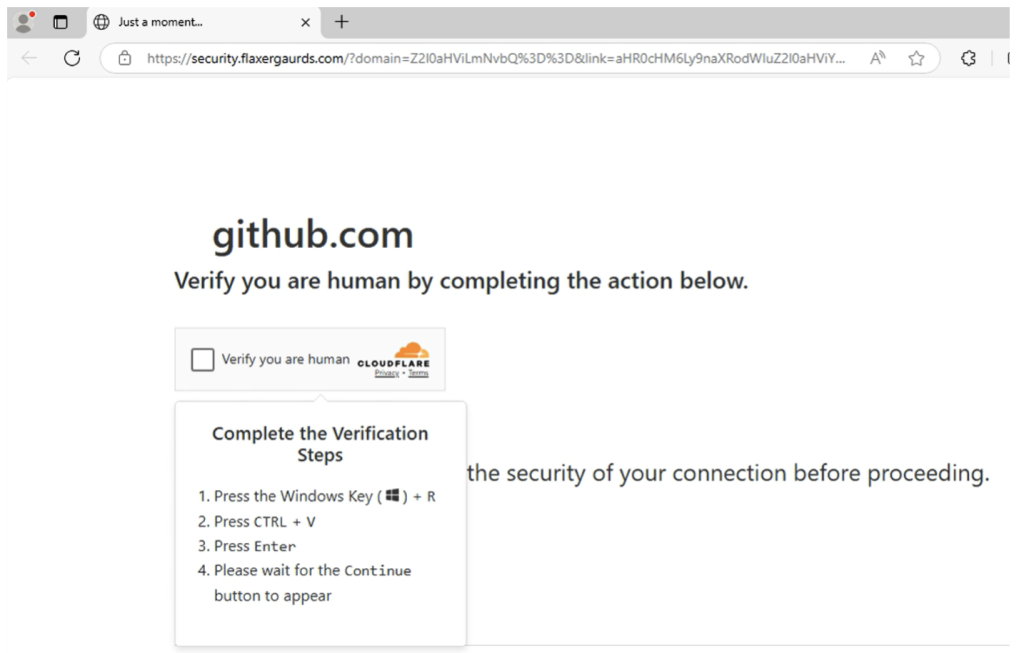
TA585’s most distinctive technique involves web injection attacks on vulnerable websites. Proofpoint researchers uncovered malicious JavaScript injections added to legitimate but compromised domains, enabling a fake overlay to appear as a CAPTCHA verification screen.
This overlay uses the ClickFix technique, which tricks users into running a PowerShell command manually through the Windows Run box.
The injected script dynamically filters incoming traffic, ensuring that only genuine visitor sessions, not bots or automated scanners, trigger the malicious payload.
Once executed, the PowerShell command downloads and installs MonsterV2 or other malware, such as Rhadamanthys Stealer, leveraging TA585’s own filtering infrastructure to maintain control over payload distribution.
Proofpoint found that compromised business email URLs and GitHub notification lures are also used to deliver malware. In GitHub-themed attacks, TA585 creates issues in fake repositories and tags legitimate users to trick them into opening URLs that lead to actor-controlled sites.
These pages mimic GitHub’s interface but secretly invoke the exact ClickFix mechanism to launch malicious scripts.
Upon successful execution, MonsterV2 decrypts its configuration using the ChaCha20 cipher and decompresses it with ZLib. The configuration includes C2 domains, privilege escalation flags, and anti-sandbox directives.
The malware gathers detailed system information such as hostnames, usernames, and IP addresses and transmits it to command servers via an encrypted TCP channel.
MonsterV2’s feature set includes HVNC (Hidden Virtual Network Computing) for covert remote access, clipper functions that hijack cryptocurrency transactions, and credential theft from browsers, Telegram, and Discord.
It notably avoids systems located in CIS countries. Often, MonsterV2 arrives encrypted with SonicCrypt, a crypter capable of defeating static analysis and bypassing Windows Defender protections.
Proofpoint concludes that TA585’s self-contained structure and technical proficiency represent a growing trend of vertically integrated cybercrime models, signaling the next stage in professionalized malware operations.
| Indicators | Description | First Seen |
| SHA256: ccac0311b3e3674282d87db9fb8a151c7b11405662159a46dda71039f2200a67 C2: 139.180.160[.]173 Port: 7712 | MonsterV2 SHA256 file hash, C2, and Port | 2025-02-22 |
| SHA256: 666944b19c707afaa05453909d395f979a267b28ff43d90d143cd36f6b74b53e C2: 155.138.150[.]12 Port: 7712 | MonsterV2 SHA256 file hash, C2, and Port | 2025-03-08 |
| SHA256: 7cd1fd7f526d4f85771e3b44f5be064b24fbb1e304148bbac72f95114a13d8c5 C2: 83.217.208[.]77: Port: 7712 |
MonsterV2 SHA256 file hash, C2, and Port | 2025-05-12 |
| SHA256: 0e83e8bfa61400e2b544190400152a54d3544bf31cfec9dda21954a79cf581e9 C2: 83.217.208[.]77 Port: 7712 |
MonsterV2 SHA256 file hash, C2, and Port | 2025-05-19 |
| SHA256: d221bf1318b8c768a6d824e79c9e87b488c1ae632b33848b638e6b2d4c76182b C2: 91.200.14[.]69 Port: 7712 |
MonsterV2 SHA256 file hash, C2, and Port | 2025-05-26 |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
