A sophisticated new malware campaign has targeted the global developer community, with the threat actor known as TigerJack infiltrating multiple extension marketplaces to deploy malicious Visual Studio Code (VS Code) extensions.
Security researchers have linked TigerJack to at least 11 compromised extensions distributed under the publisher identities ab-498, 498, and 498-00, cumulatively affecting more than 17,000 developers worldwide.
The extensions steal source code, mine cryptocurrency, and create persistent remote access backdoors on infected systems.
Among the most damaging of TigerJack’s creations are two highly popular extensions, “C++ Playground” and “HTTP Format.”
Initially available on Microsoft’s VS Code Marketplace, both were quietly taken down after extensive compromise. However, they remain fully operational on the OpenVSX marketplace, which is used by IDEs such as Cursor and Windsurf, where they continue to spread unchecked.
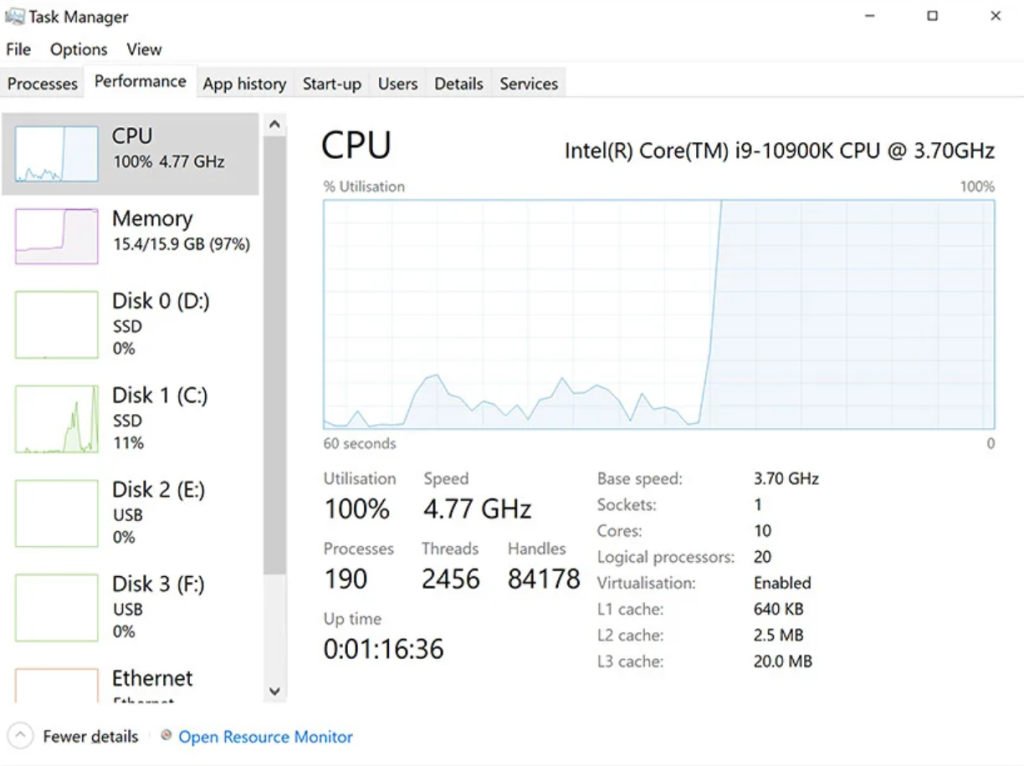
The C++ Playground extension posed as a professional C++ development tool with error highlighting, formatting, and real-time compilation features. Hidden within its operational code was a data exfiltration script that activated on every document change event.
It monitored .cpp files and transmitted their content to multiple remote endpoints, including ab498.pythonanywhere.com and api.codex.jaagrav.in.
This process occurred in near real-time, allowing the attacker to intercept sensitive intellectual property directly from developers’ local workspaces. The payload structure captured complete code snippets, input data, and even replaced versions for analysis.
The HTTP Format extension, marketed as an HTTP request formatter, concealed a cryptocurrency mining module. Embedded CoinIMP API credentials enabled TigerJack to monitor mining efficiency and withdraw profits directly to controlled wallets.
Systems running the extension silently performed mining operations, leading to high CPU usage, performance degradation, and hardware strain. Developers often assumed their machines were lagging due to IDE issues, never realizing their systems were being exploited for cryptomining.
Beyond theft and mining, several extensions distributed under TigerJack’s accounts included a remote code execution (RCE) backdoor that checked every 20 minutes for new commands hosted on https://ab498.pythonanywhere.com/static/in4.js.
This dynamic malware architecture allowed the actor to execute arbitrary code, deploy additional payloads, and gain complete system control without detection or updates.
The campaign demonstrated professional-level social engineering. Multiple extensions were initially benign to accumulate positive reviews before being updated with malicious payloads, a Trojan horse technique ensuring long-term persistence.
While Microsoft removed the extensions, it issued no public advisory, leaving affected users unaware of their compromise. On OpenVSX, the same malware remains downloadable, exposing thousands more developers.
Security researchers warn that this fragmented ecosystem enables cross-marketplace persistence, where malicious extensions evade detection through platform migration, an alarming sign of evolving supply-chain threats targeting the software development community.
Network:
- ab498.pythonanywhere[.]com
- api.codex.jaagrav[.]in
- coinimp[.]com
Extensions:
- ab-498.cppplayground
- ab-498.httpformat
- ab-498.pythonformat
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
