
A new Android banking malware, which researchers named Massiv, is posing as an IPTV app to steal digital identities and access online banking accounts.
The malware relies on screen overlays and keylogging to obtain sensitive data and can take remote control of a compromised device.
In a campaign observed by researchers at fraud detection and mobile threat intelligence company ThreatFabric, Massiv targeted a Portuguese government app that connects with Chave Móvel Digital – Portugal’s digital authentication and signature system.
The two service contain user data that could be used to bypass know-your-customer (KYC) verifications or to access banking accounts and other public and private online services.
.jpg)
Source: ThreatFabric
“MTI research identified cases where new accounts were opened in the name of the victim (user of the infected device) in new banks and services (not used by the victim),” describes the ThreatFabric report.
“Since those accounts are fully under fraudster control, they can further use them as a part of money laundering scheme as well as getting loans and cashing out the money, leaving unsuspecting victim in debts in the bank they never opened account themselves.”
Massiv provides two remote control modes for its operators: a screen live-streaming mode that leverages Android’s MediaProjection API, and a UI-tree mode that extracts structured data from the Accessibility Service.
The latter includes visible text, interface element names, screen coordinates, and interaction attributes, allowing attackers to click buttons, edit text fields, and more.
This second mode is particularly helpful for bypassing screen-capture protections commonly used in banking, communication, and other apps that host sensitive content.
An interesting trend identified by ThreatFabric through the discovery of Massiv is the increasing use of IPTV apps as lures for Android malware infections, a technique that has increased over the past eight months.
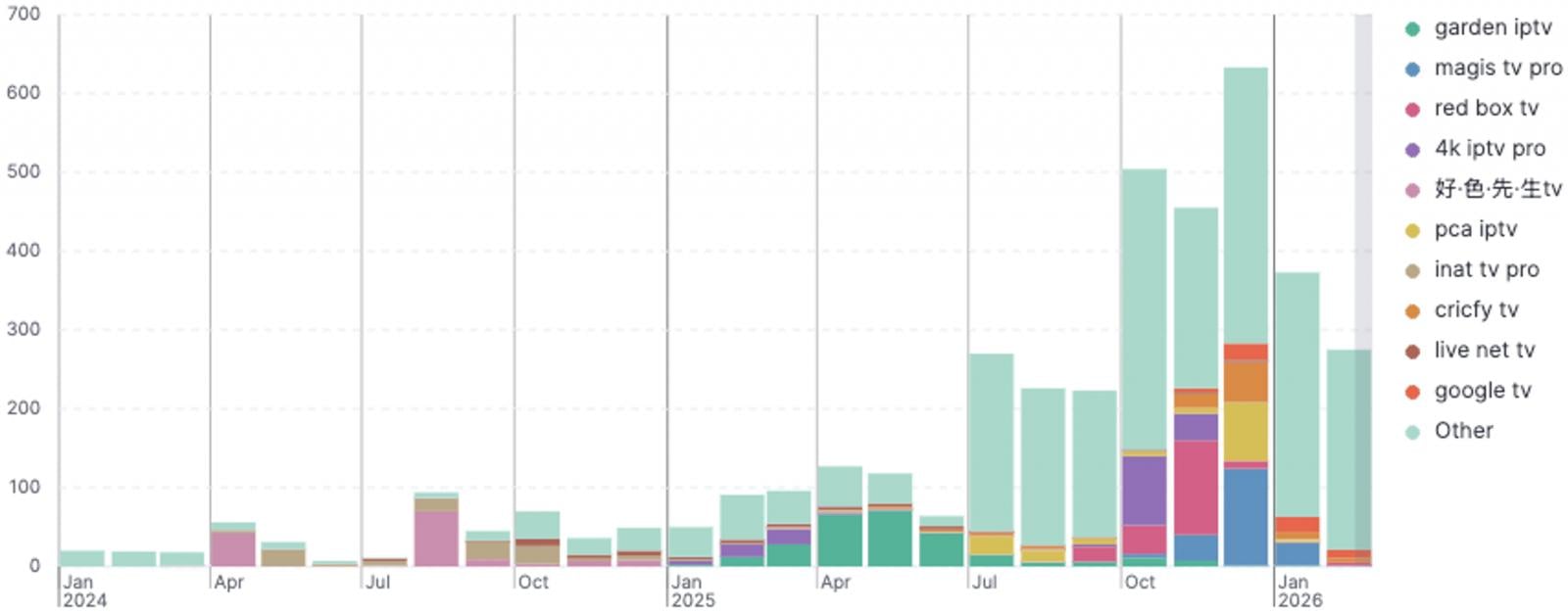
Source: ThreatFabric
These apps typically play a key role in copyright infringement, so they cannot be found on Google Play due to policy violations. Sourcing them as APKs from unofficial channels is considered normal for their users, who are accustomed to sideloading them.
In most cases, the IPTV app is fake, does not offer access to pirated broadcasts, and the APK is a dropper that installs the malware payload. In some cases, the app displays a legitimate IPTV website in a WebView to maintain the illusion.
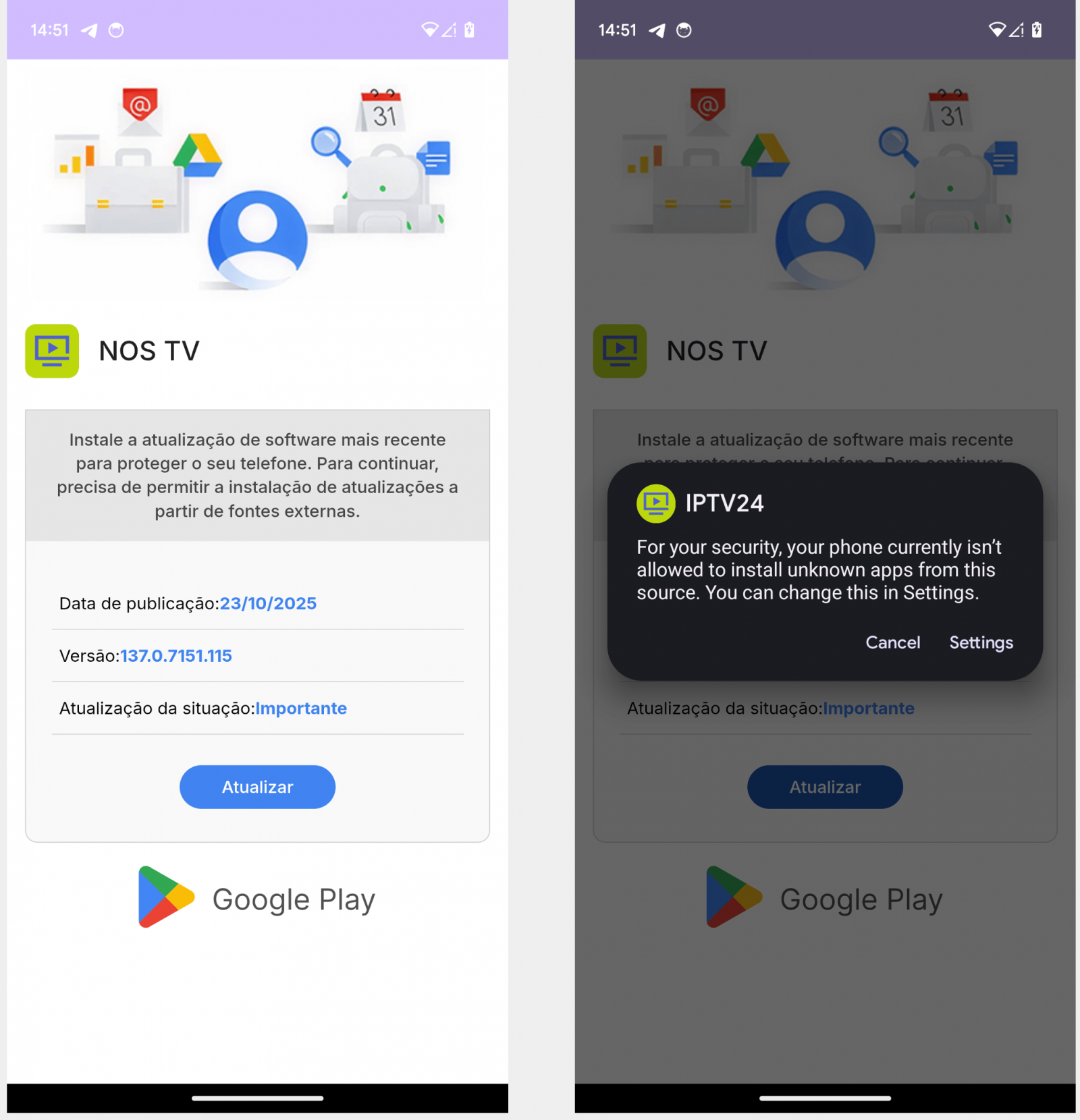
Source: ThreatFabric
The researchers report that fake IPTV-masking malware droppers have primarily targeted users in Spain, Portugal, France, and Turkey.
Android users are recommended to only download vetted apps from reputable publishers available on official channels (Google Play), keep Play Protect active, and use it to regularly scan the device.
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.


