South Korean cybersecurity researchers have confirmed a new remote data-wipe attack targeting Android devices, attributed to the KONNI advanced persistent threat (APT) group.
The group, with ties to North Korea’s 63 Research Center and known overlaps with Kimsuky and APT37, used Google’s asset-tracking service, Find My Device Hub, to reset devices and delete data on victims’ smartphones and tablets.
During ongoing investigations, Genians Security Center identified a series of attacks that began as spear-phishing campaigns.
Attackers impersonated trusted figures, psychological counselors, and human rights activists and distributed malware disguised as stress-relief programs via the KakaoTalk messenger.
Victims, often engaged in North Korean defector support, unknowingly installed the malicious software, enabling covert persistent access.
Initial infection was achieved through MSI installer files delivered via KakaoTalk, signed with legitimate-looking Chinese certificates.
Upon execution, these installers deployed AutoIt scripts designed for persistence and stealth, copying payloads into system directories and registering scheduled tasks for periodic execution.
The core malware components leveraged multiple RATs, including RemcosRAT, QuasarRAT, and RftRAT, all orchestrated through WordPress-hosted C2 infrastructure in several countries.
Persistence was maintained via shortcut files (e.g., “Smart_Web.lnk”) in Windows Startup folders, while the RAT modules performed surveillance, information theft, and received subsequent commands from the attackers.
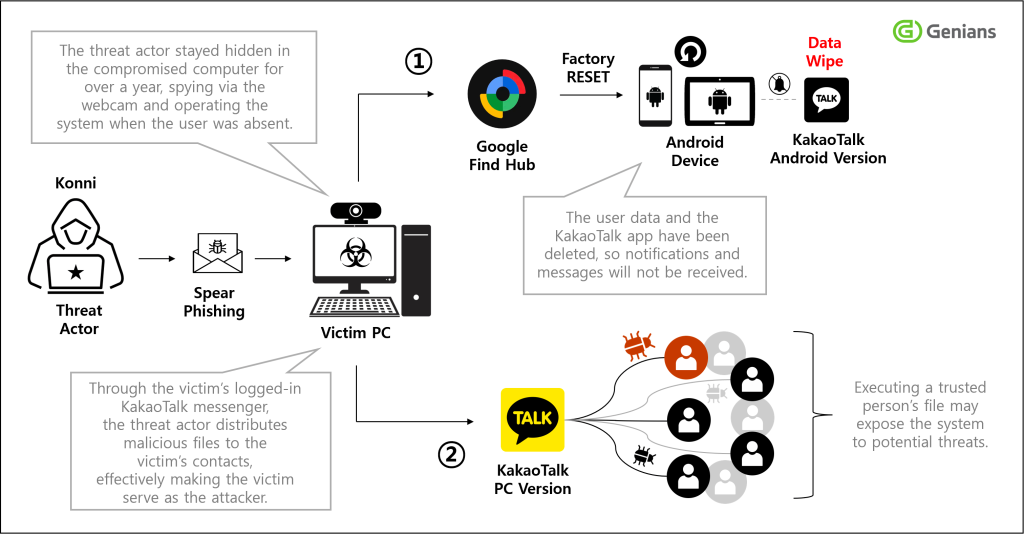
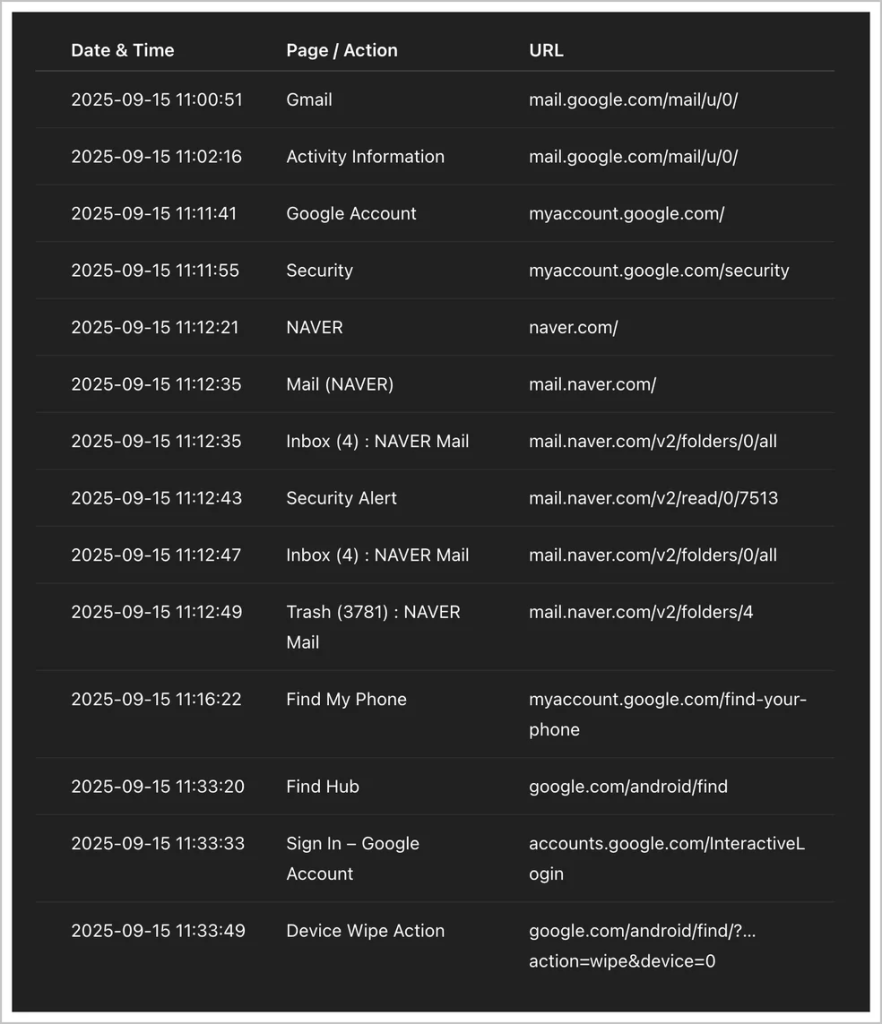
Critically, stolen Google account credentials were used to access and abuse Find My Device Hub functionalities.
Attackers tracked the victim’s locations in real time and issued remote-wipe commands via the compromised Google accounts, repeatedly resetting Android devices and deleting sensitive personal data.
After disabling device access and message alerts, attackers exploited victims’ active KakaoTalk sessions to propagate the malware, using trust-based social engineering to expand their reach.
Experts advise immediate hardening of Google account security, including mandatory password changes and enabling two-factor authentication, to prevent further abuse of Find My Device features.
Real-time security verification for remote administration requests is strongly recommended, including additional authentication steps for device resets.
End-user vigilance must be reinforced alongside technical defenses, such as endpoint detection and response (EDR) deployments.
Behavioral monitoring and IOC-linked tracking can reveal anomalous activities stemming from batch script executions, process creations, and unusual network traffic to untrusted global C2 nodes.
Rapid containment actions, such as blocking suspicious command sequences and isolating compromised endpoints, are vital.
This campaign highlights the escalation of threat actor tactics, demonstrating how legitimate services can be weaponized in targeted state-sponsored attacks.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
