This newsletter is brought to you by cloud security firm Prowler. You can subscribe to an audio version of this newsletter as a podcast by searching for “Risky Business” in your podcatcher or subscribing via this RSS feed.
A Russian man has pleaded guilty to hacking US companies and selling access to ransomware groups.
Aleksei Olegovich Volkov went online under the hacker name of chubaka.kor, and worked as an initial access broker (IAB) for the Yanluowang ransomware.
Volkov used various techniques to breach a corporate employee’s account, escalate access to the employer’s network, and then sold that access to other cyber criminals.
According to court documents, between July 2021 and November 2022, Volkov regularly sold access to individuals who later deployed the Yanluowang ransomware.
Investigators tied Volkov to intrusions and subsequent ransomware attacks on seven US companies, including a bank, a telco, and an engineering firm.
Two of the seven victims paid ransoms of $1.5 million in Bitcoin, of which Volkov also got a cut, according to charging documents.
Although court documents don’t mention this, Volkov was charged shortly after the Yanluowang hacked and tried to ransom Cisco in May 2022. It’s unclear if that played any role, but tickling the parent company of the vaunted Talos IR teams might have been a bad decision.
The Yanluowang eventually shuttered operations in November 2022 after it got hacked, and internal chats and its source code were leaked online.
Volkov was eventually arrested in 2024, after he moved to Rome, most likely to escape the complications of Russia’s invasion of Ukraine and the state’s ever-increasing military drafting. He was extradited to the US that same year.
He faces up to 50 years in prison and fines of up to $1 million. A date for the sentencing hearing has not been set yet. He will also have to pay restitution to past victims.
[h/t Seamus Hughes of CourtHouseNews] [h/t OnionToranaga]
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
TISZA leak: Hungary’s main opposition party has suffered a major security breach. Hackers leaked more than 200,000 user records from the TISZA party’s mobile app. This is the party’s second breach this year. TISZA leader Péter Magyar blamed the hack on Russian hackers. [KiberBlog//Hungary Today]
APT breaches US CBO: The US Congressional Budget Office has been hacked by a foreign hacking group. The intruders are believed to have stolen emails and internal chat logs. The hack was discovered last week and is still under investigation. The CBO creates economic projections for proposed bills. [Washington Post//Politico]
WaPo breach linked to Oracle hacks: The Washington Post has joined the list of companies that have been impacted by a recent wave of zero-day attacks against Oracle EBS environments. [Reuters]
Illuminate fined for 2022 breach: Illuminate, an IT provider of school attendance and grading software, has agreed to pay a $5.1 million fine to the NY OAG for a 2022 security breach that exposed the data of 1.7 million students. [h/t DataBreaches.net]
Balancer IR: Trail of Bits has published an incident report on the $128 million hack of the Balancer DeFi platform last week.
“The root cause of the hack was a rounding direction issue that had been present in the code for many years. When the bug was first introduced, the threat landscape of the blockchain ecosystem was significantly different, and arithmetic issues in particular were not widely considered likely vectors for exploitation.”
General tech and privacy
Tinder to rummage through your photos: Tinder will use AI to analyze a user’s photo gallery to learn more about their interests and personality. The AI will request permission before accessing the camera roll. The new feature is named Chemistry and has been rolled out for tests in Australia and New Zealand. Tinder becomes the second company, after Meta, to deploy AI on its users’ private galleries. The dating app has seen nine straight quarters of declining paying subscribers. [TechCrunch]
Chrome to remove XSLT support: Google will remove support for the XSLT language from the Chrome browser by late 2026. Extensible Stylesheet Language Transformations is a system similar to CSS, designed to stylize XML documents. Google cited security reasons for removing support. XSLT support will be removed in Chrome version 155, scheduled for November next year. Firefox and Safari will also remove XSLT support, but they have not announced clear deadlines.
Firefox paid support: Mozilla has announced Firefox paid support for corporate customers.
Akamai reports disruptions in Russia: The Russian government has started filtering Akamai traffic, leading to disruptions for some local customers. Akamai says it is aware of the government’s actions, but it’s unable to do anything. A full block has not yet been fully implemented. Russia has required all foreign cloud providers to open offices in the country and register with the state.
EU GDPR changes to cookie nightmare: Proposed changes to the EU GDPR legislation would allow European users to accept or refuse tracking cookies using browser or device settings. The changes are currently being discussed by EU lawmakers looking to simplify GDPR laws and reduce the number of cookie consent banners. Companies that will ignore device-level tracking refusals would risk fines of up to €20 million or 4% of their annual turnover under the new rules. [Analysis by Lukasz Olejnik]
Government, politics, and policy
Europol data sharing law gets green light: The European Parliament’s Committee on Civil Liberties, Justice and Home Affairs (LIBE) has voted to advance legislation proposed by Europol that will expand data sharing and the use of biometrics across the bloc. [The Record]
CMMC 2 compliance lagging behind: Most US cybersecurity government contractors are lagging behind on compliance with the US government’s new Cybersecurity Maturity Model Certification 2.0 framework. Phase 1 of CMMC 2 compliance will be enforced starting Monday, November 10. [Bloomberg Law]
Australia sanctions North Korean hackers: Australia has imposed financial sanctions and travel bans on North Korean hackers. Sanctions were levied on one individual and four entities associated with the DPRK’s state-sponsored hacking program. Sanctioned entities include the Kimsuky, Lazarus, and Andariel hacking groups. WannaCry developer Park Jin Hyok and his employer, Chosun Expo, were also sanctioned.
ICC replaces US software: The International Criminal Court has migrated from Microsoft Office to OpenDesk after the US sanctioned some of its judges. [Handelsblatt//Euractiv]
Austria abandons Microsoft too: The Austrian Armed Forces has abandoned Office for LibreOffice, while the country’s ministry of economy has also moved from Microsoft to NextCloud. [It’s FOSS]
Singapore to punish scammers with cane beatings: Singapore authorities will punish scammers, recruiters, and money mules with cane beatings. Scammers could receive between 6 and 24 strokes, and money mules up to 12. Lawmakers updated the country’s criminal law last week to include physical punishments. The country lost almost $2.85 billion to scams over the past half-decade. [The Straits Times]
Chinese bus fears spread: Last week, an investigation in Norway found that Chinese electric buses contained killswitches and remote access vulnerabilities. Now, the same fears are close to sparking official investigations in many other countries, such as Australia, Denmark, the UK, and the Netherlands. [h/t Ravi Nayyar]
Trump ally named NSO boss: Israeli spyware maker the NSO Group has named a new chairman. The company has named David Friedman to the position. Friedman is a former lawyer for Donald Trump and was also appointed ambassador to Israel during Trump’s first presidency. Friedman was appointed after a consortium of US investors acquired the company last month. Under his new role, Friedman has promised to help lift sanctions and return to the US market. [The Marker//Wall Street Journal//Haaretz]
⚠️ David Friedman, Trump’s former ambassador to Israel and one of the key architects of the Abraham Accords, has been appointed head of #spyware vendor NSO Group.
www.themarker.com/technation/2…—Vas Panagiotopoulos (@vaspanagiotopoulos.com) 2025-11-09T15:47:34.957Z
In this Risky Business sponsor interview, Casey Ellis chats to Toni de la Fuente, founder and CEO of Prowler, an open source platform for cloud security. They chat about how and why Prowler selectively applies AI to ensure it adds value rather than just because they can.
Arrests, cybercrime, and threat intel
FBI goes after Archive[.]is: The FBI has launched a criminal investigation against Archive[.]is, a popular website archiving toolkit. The agency has requested information about the site’s owner from Canadian domain registrar Tucows. The website is often used to bypass paywalls for paid news articles. [404 Media//Archive[.]is tweet]
New: The FBI filed a subpoena trying to unmask the person or people behind archive.is / archive.today, which have been running anonymously for 13 yrs. Site was widely used by GamerGate, and then to bypass paywalls but has become kind of core archiving infrastructure
www.404media.co/fbi-tries-to…—Jason Koebler (@jasonkoebler.bsky.social) 2025-11-06T14:53:55.455Z
Samourai Wallet dev gets prison sentence: The co-founder and CEO of cryptocurrency mixing service Samourai Wallet was sentenced to five years in prison. Keonne Rodriguez received the maximum prison sentence for his crimes. Authorities shut down the Samourai Wallet website in April 2024. The service was used to launder more than $237 million in crypto linked to hacks, online fraud, and drug trafficking. Samourai Wallet CTO William Lonergan Hill will be sentenced later this month. [CoinDesk]
Hackers sentenced over gambling site hacks: Singaporean authorities have sentenced three Chinese nationals to prison for hacking-related charges. All three received prison sentences of more than two years and four months in prison. The three hacked into online gambling sites to cheat on games and steal personal data. The three are part of a six-man hacker group arrested in September last year. Authorities seized assets worth $40 million from the group.
Pakistani arrested over data breach: A Pakistani man was arrested for allegedly selling the data of millions of citizens online. Anees Ahmed Shah, from the city of Bhakkar, was taken into custody by the country’s cybercrime agency last week. Officials claim Shah bought the personal data of Pakistani citizens from black markets and then resold it on dedicated websites. The sites provided access to names, ID card numbers, home addresses, and travel records. [The Express Tribune]
Cambodia raids Bavet scam centers: The Cambodian government has raided two cyber scam compounds in the city of Bavet. More than 650 suspects, mostly foreign nationals, were taken into custody. One scam compound specialized in impersonating government agencies, while the second ran investment scams. [Phnom Penh Post]
CAMBODIA: More video circulating alleged to show workers escaping a Cambodian scam compound, this time in Bavet. 1/6
—Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2025-11-08T10:15:44.254Z
CAMBODIA: More clips circulating of Bavet scam compound breakout. 1/4
—Cyber Scam Monitor (@cyberscammonitor.bsky.social) 2025-11-08T11:12:26.150Z
KK Park to be demolished: Myanmar military’s junta has started demolishing buildings in the country’s largest scam compound. Controlled demolitions began on October 23 at KK Park, in the city of Myawaddy. 24 of the park’s 250 buildings have been demolished using dynamite by the local border force. [Vietnam.vn//The Irrawaddy]

Judge rules mistrial in MEV hacker case: A New York judge has ruled a mistrial in the case of two brothers who stole $25 million worth of cryptocurrency from crypto-trading bots. The judge sent the jury home after they couldn’t reach a verdict. The two brothers, Anton and James Peraire-Bueno, were charged in May 2024. Their defense argued that the brothers used their MIT education to execute a novel but legitimate trading strategy. The DOJ claimed the two exploited vulnerabilities in MEV trading bots and then laundered the extracted funds. [Reuters]
Stalkerware goes down: The number of unique stalkerware products has gone down over the past half-decade. An audit of stalkerware detections on mobile antivirus products found that many stalkerware apps are variations of a small number of products. Unique stalkerware families went down from 20 in 2020 to 17 this year. Detections stayed the same, with a few mobile security products detecting most threats, while others were still very far behind.
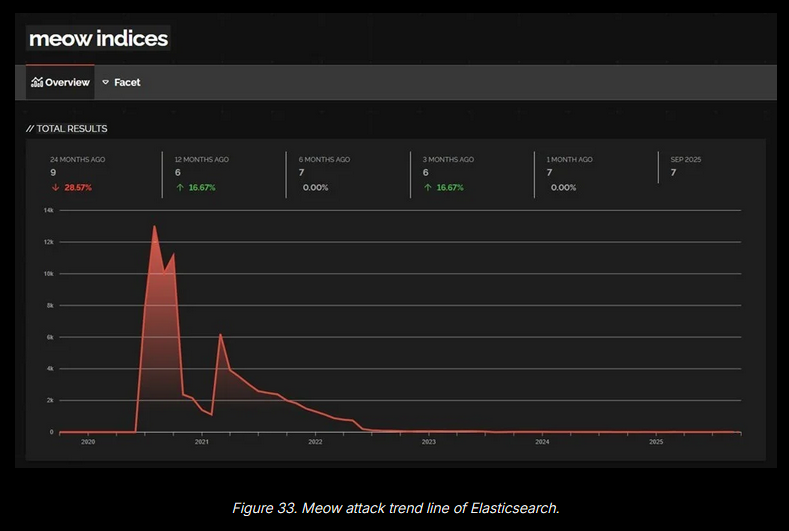
MEOW attacks decline: Trustwave says the MEOW campaign appears to have subsided. MEOW attacks appeared in 2020. A mysterious group hacked and deleted data, overwriting indexes with the word “meow” on databases left exposed on the internet without a password.
123456 remains top password: A study of two billion passwords leaked this year reveals that 123456 is still the most widely used password.
Malicious casino spam: Sucuri looks at the rising waves of online gambling and casino spam targeting Asian audiences and hosted on hacked sites, reminiscent of the old pharma campaigns targeting English-speaking audiences in the past.
Malicious AI agent impersonators: Radware is sounding the alarm that threat actors are actively developing malicious bots that pose as more popular and legitimate AI agents, which they then use for attacks, such as website scraping, brute-forcing, form automation, and so on.
New npm malware: Fifty-seven malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Ransomware in VS Code extensions: A malicious VS Code extension on the official marketplace tried to deploy ransomware on developer systems. According to Secure Annex, the ransomware appears to have been vibe-coded, hardcoded its encryption key, and appears to have been some sort of joke or experiment.
Ransomware has appeared in the VS Marketplace and makes me worry. Clearly created through AI, it makes many mistakes like including decryption tools in extension. If this makes it into the marketplace through, what impact would anything more sophisticated cause?
secureannex.com/blog/ransomv…—
Malware technical reports
GlassWorm returns: GlassWorm, a worm that spreads using VS Code extensions, has returned on the OpenVSX portal.
Eleven11/RapperBot evolution: The Netscout team has published a short history of the rise and fall of the Eleven11 (RapperBot) DDoS botnet, up until the arrest of one of its admins.
RondoDox expands exploit arsenal: The RondoDox IoT botnet has apparently expanded its exploit arsenal by 650%, per Belzebub.
Fantasy Hub RAT: Zimperium has identified a new Android RAT named Fantasy Hub that is currently advertised under a MaaS model via ads on hacking forums and Telegram.
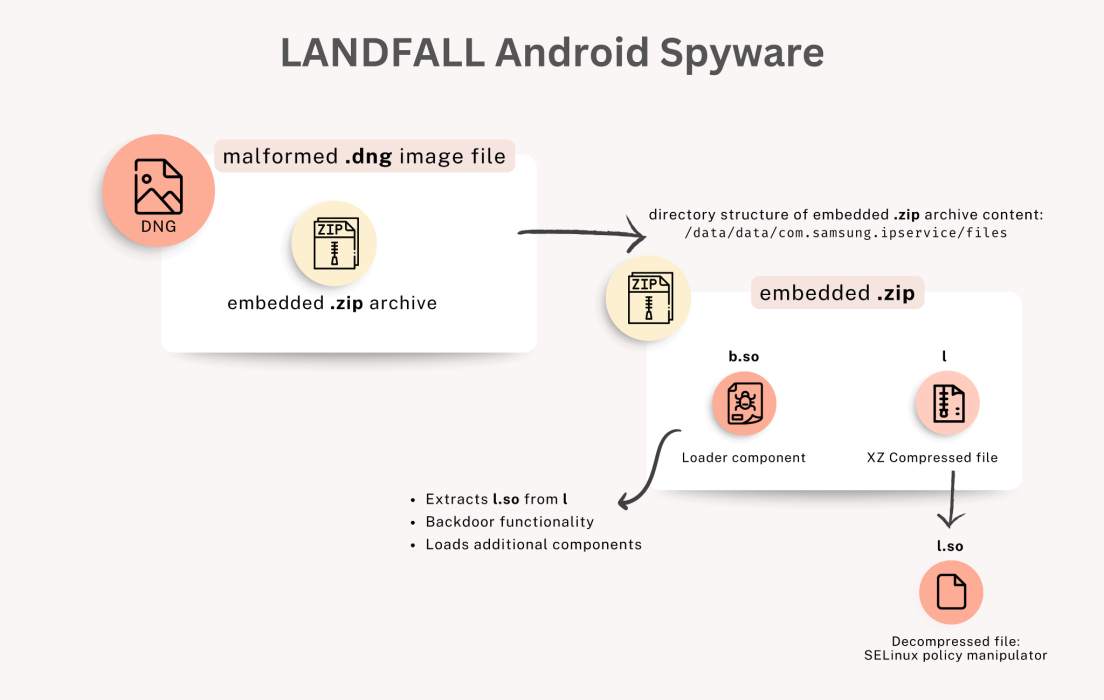
Samsung zero-day delivers Landfall spyware: A new commercial-grade Android spyware has been spotted in a campaign targeting the Middle East. The attackers used malicious image files to trigger a Samsung zero-day and install the new Landfall spyware. Samsung patched the zero-day (CVE-2025-21042) in April, but traces of the spyware have been found dating back to July of last year. Security firm Palo Alto Networks has not linked the zero-day to any spyware vendor or state.
In this sponsored product demo, Prowler founder and CEO Toni de la Fuente walks Risky Business host Patrick Gray through the company’s open-source cloud security platform. Toni demonstrates how Prowler can identify and remediate security issues across AWS, Azure, GCP, and Kubernetes. There’s a pointy-clicky GUI interface and a CLI, and both come in handy in different ways. The Prowler platform is completely free and open source, but there is a hosted version you can pay for if you don’t want to run it yourself.
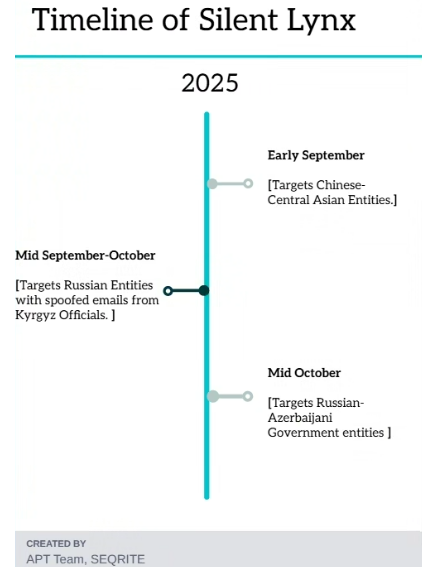
Silent Lynx: Seqrite has spotted the Silent Lynx APT (YoroTrooper, Sturgeon Phisher, Cavalry Werewolf, ShadowSilk) shift its focus on targeting the Azerbaidjan government.
APT-C-60 (DarkHotel): The APT-C-60 group, aka DarkHotel, is continuing its attacks on Japan, attacks first spotted in October by the country’s CERT. China’s Qihoo 360 also looks at the same group.
New Lazarus Comebacker version: ENKI researchers have spotted a new version of Comebacker, a downloader and backdoor previously used by North Korean hacking group Lazarus.
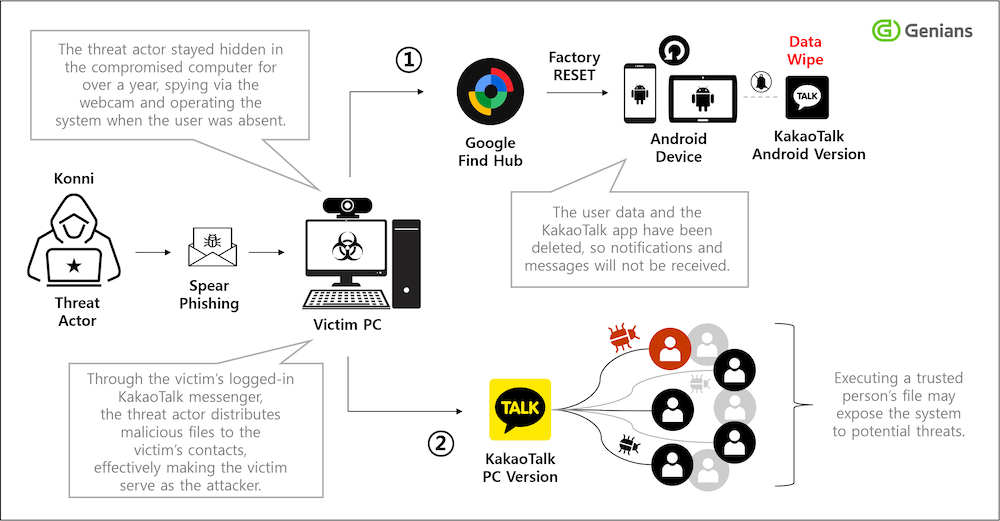
Konni APT wipes victim Android phones: A North Korea APT is breaching targets and wiping its victims’ Android phones. The hacks are part of a campaign targeting North Korean human rights activists. Konni operators breach their PCs and spam their KakaoTalk contacts with malware. The attackers then wipe the Android devices via the Google Find hub to prevent victims from receiving KakaoTalk notifications or replies from friends.
Django SQLi: The Django Python framework has patched an SQL injection vulnerability in its database component. The vulnerability (CVE-2025-64459) can be exploited by adding internal query parameters to user input. It can allow attackers to bypass authentication, elevate privileges, and access sensitive data. Django is the Python language’s most widely used web framework.
Monsta FTP RCE: WatchTowr Labs has published a write-up about a pre-auth RCE it found in Monsta FTP, a web-based file-transfer solution. This is now tracked as CVE-2025-34299.
ASP.NET request smuggling: Praetorian’s Siddhant Kalgutkar has published a technical write-up on CVE-2025-55315, an HTTP request smuggling vulnerability in ASP.NET Core’s Kestrel server. The bug netted Kalgutkar a $10,000 bounty from Microsoft. The bug was patched last month.
RunC vuln allows container breakout: Three vulnerabilities in Docker’s RunC lightweight container runtime can allow threat actors to break out from containers to host systems.
LangGraph RCE: An RCE vulnerability has been discovered and patched in LangChain’s LangGraph toolkit for building AI agents.
QNAP security updates: QNAP has released security fixes, including for some of the bugs used at the recent Pwn2Own Dublin hacking contest.
KubeVirt security audit: Quarkslab has completed a security audit of open-source project KubeVirt, a virtual machine management add-on for Kubernetes.
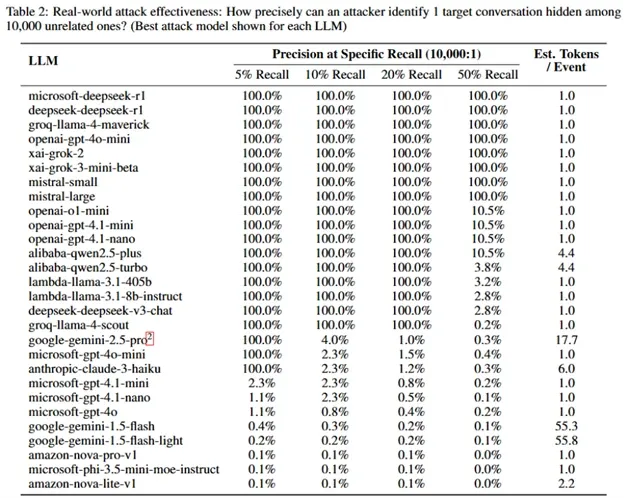
Whisper Leak attack: Microsoft has discovered a new side-channel attack that can leak the topic of AI chatbot discussions. The new Whisper Leak targets the encrypted TLS traffic between AI chatbots and their backend LLMs. In Microsoft’s tests, the attack had a 100% precision rate against some LLMs. Microsoft, OpenAI, Mistral, and xAI have deployed protections against Whisper Leak.
Infosec industry
Threat/trend reports: Bitsight [PDF], Comparitech, CyFirma, Eclypsium, Google [PDF], and Nagomi Security have recently published reports and summaries covering various threats and infosec industry trends.
New tool—Blade: Security firm CyberCX has open-sourced Blade, a command-line tool written in Go, designed to interact with BloodHound CE and Neo4j.
New tool—MAD-CAT: Security researcher Karl Biron has released MAD-CAT, a tool that simulates destructive attacks on database systems.
New tool—DonPwner: Security researcher Mor David has open-sourced DonPwner, a tool for safe password spray attacks with built-in delay and jitter mechanisms to avoid account lockouts, automatic removal of successfully authenticated users, and credential analysis against secretsdump files.
New tool—Venom C2: IBM X-Force researcher Bobby Cooke has released Venom C2, a dependency‑free Python 3 C&C framework for red-team operations.
New tool—NoMoreStealers: Security researcher EvilBytecode has released NoMoreStealers, a Windows kernel-mode minifilter driver that monitors file system access to protect against information-stealing malware.
New tool—GMSGadget: Security researcher Kévin Gervot has released a project named GMSGadget. The project tracks JavaScript gadgets that can be used to bypass XSS mitigations. The project is similar to other initiatives that track benign tools that can be abused for attacks on Windows (LOLBAS, LOLDrivers, and LOFLCAB), Linux (GTFOBins), macOS (LOOBins), CI/CD pipelines (LOTP), ESXi VMs (LOLESXi), RMM software (LOLRMM), and tunneling technologies (LOLTunnels).
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about aggressive US cyber operations targeting the Venezuelan government in President Trump’s first term. These were narrowly successful in that they achieved their immediate operational goals, but they didn’t achieve Trump’s broader policy goal of ousting Venezuelan leader Nicolás Maduro.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the futility of using aggressive cyber operations to send messages between states.
